
Researchers have exploited a flaw in the encryption procedure used by the Linux.Encoder.1 – the first ransomware targeting the Linux platform – to develop a decryption tool for victims.
On Thursday, Russian anti-virus company Dr. Web first disclosed the existence of Linux.Encoder.1, a strain of ransomware similar to other notorious ransomware families such as CryptoWall and TorLocker, but targeting computers running Linux rather than Windows.
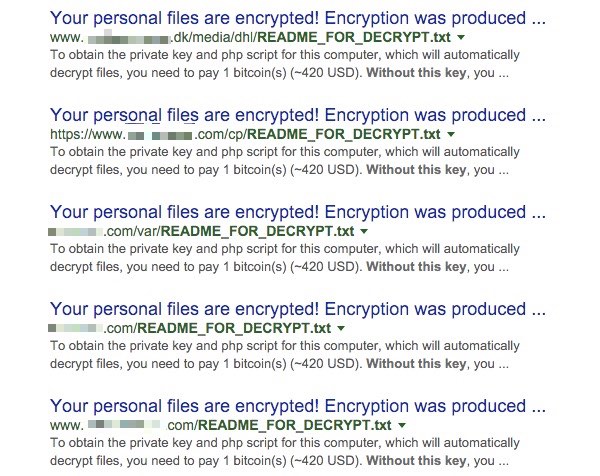
Evidence of infections by Linux.Encoder.1 are scattered across the net, because many websites appear to be revealing their impacted state in search engine results.
“Once launched with administrator privileges, the Trojan loads into the memory of its process files containing cybercriminals’ demands,” explains Dr Web in a blog post about the malware. “As an argument, the Trojan receives the path to the file containing a public RSA key. Once the files are read, the malicious program starts as a daemon and deletes its original files.”
The ransomware’s infection process proceeds as follows:
First, Linux.Encoder.1 encrypts all files found in the directories /var/lib/mysql and /etc/nginx, among others. Next, it moves on to the home directories, the directory from which it was launched, and the root directory.
Then the malware targets specific files whose names start with a specific string, including “public_html” and “www”, and those with certain file extensions, such as .docx, .jpg, and .exe.
Each of these files are encrypted with a locally generated Advanced Encryption Standard (AES) symmetric key, which the ransomware then encrypts using an RSA asymmetric key.
As Softpedia reports, Linux.Encoder.1 generates the unique RSA encryption and decryption keys on its command-and-control (C&C) server, with the private key stored on the attacker’s server and the public key sent to the victim in order for them to decrypt the AES key.
A file called README_FOR_DECRYPT.txt is dumped into a directory, giving victims instructions on how they can make a Bitcoin payment to recover their files.
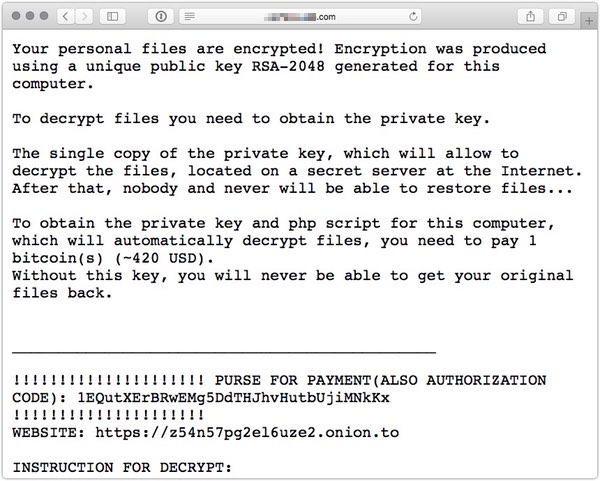
This might seem like a good setup by the ransomware’s creator. However, researchers at security firm Bitdefender have uncovered a hole in this encryption procedure, specifically with regards to the generation of the AES key:
“We realized that, rather than generating secure random keys and IVs [initialization vectors], the sample would derive these two pieces of information from the libc rand() function seeded with the current system timestamp at the moment of encryption,” explain the researchers in a blog post.
“This information can be easily retrieved by looking at the file’s timestamp. This is a huge design flaw that allows retrieval of the AES key without having to decrypt it with the RSA public key sold by the Trojan’s operator(s).”
Using this bug, the Bitdefender researchers were able to develop a free decryption tool that determines the IV and encryption key by analyzing an encrypted file, performs the decryption, and fixes permissions, thereby restoring each and every affected file to its original state.
It is fortuitous indeed when computer criminals make mistakes that benefit users.
However, as we recently saw with a buggy strain of crypto-ransomware that throws away its encryption keys, not all attackers’ mistakes are in users’ interest.
It is therefore better to leave nothing to chance.
With this in mind, I recommend that all users install a security product on their machines, roll out patches and updates as soon as they become available, and keep regular backups of their data just in case they should find themselves a victim of ransomware like Linux.Encoder.1.



Link to tool out of date … its now
http://labs.bitdefender.com/wp-content/plugins/download-monitor/download.php?id=Decrypter_0-1.3.zip
Or maybe better:
http://labs.bitdefender.com/2015/11/linux-ransomware-debut-fails-on-predictable-encryption-key/
Thank you – I've updated the link to the article as you suggested, so that should continue to work regardless of Bitdefender's version number.
I recently purchased Bitdefender for 1 year will it be updated with this Decrypter?