 At the beginning of last month, some TalkTalk customers were warned that their personal details may have been breached as part of the hack against British mobile phone operator Carphone Warehouse.
At the beginning of last month, some TalkTalk customers were warned that their personal details may have been breached as part of the hack against British mobile phone operator Carphone Warehouse.
Here is part of what TalkTalk’s statement about the incident said:
we believe that some of our mobile customers’ data may have been accessed by the criminals. This includes customers’ names, addresses, dates of birth, bank details and other personal and TalkTalk account information.
For some of the affected customers, this may have also included their My Account username and passwords – for these customers, we have already suspended their accounts until they can reset their password.
We take our customers’ security very seriously, and we’ve already put in place additional security measures to prevent further attacks. We’ve also sent an email to all customers who we believe could have been impacted by this issue.
As a result, you would hope by now that TalkTalk customers have changed their passwords, choosing something unique, and hard-to-crack.
Of course, having a unique, complex password for every website which you access is the most sensible way to run your online accounts, and that’s why you should probably use a password manager to remember all your passwords for you and store them securely.
All sounds good so far.
But, alas, TalkTalk (like British Gas before it) clearly isn’t entirely onboard with the notion of password managers.
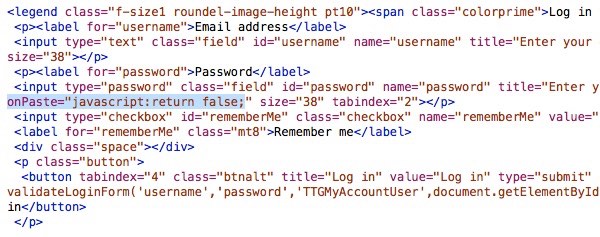
Because TalkTalk’s website actively prevents you from you cutting-and-pasting a complex password into its login form.
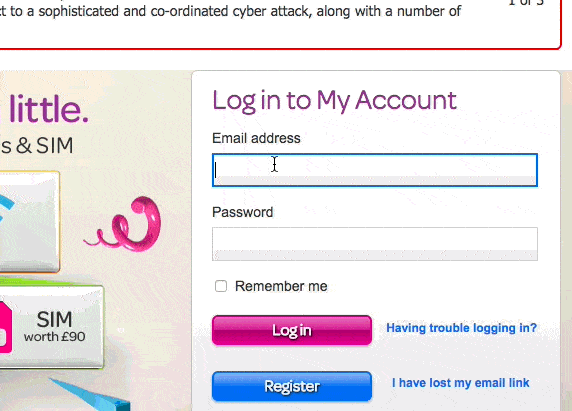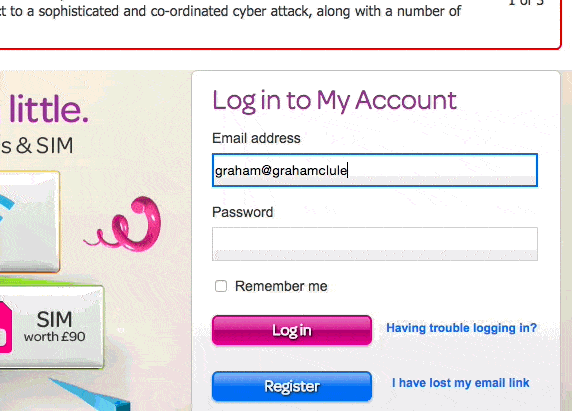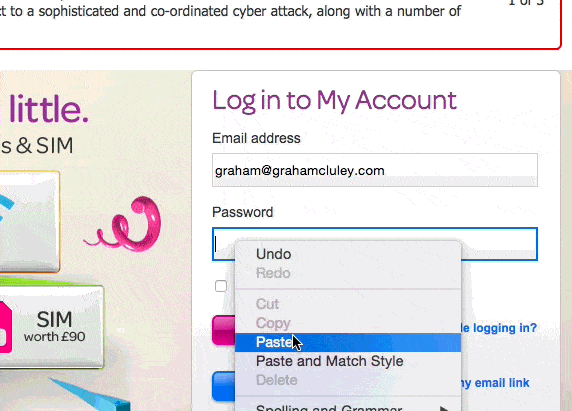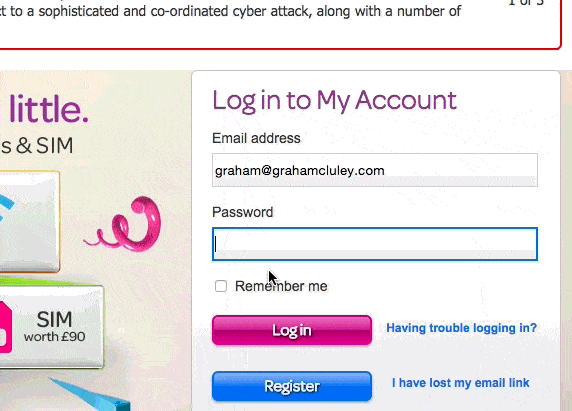
Yes, if you have a really complicated and unmemorable password for your TalkTalk account like 7X(YrLgV(LfyMNr0IhTOih`qG, the website is going to insist that you type it in manually.
The end result? Users will find they make mistakes, and end up choosing dumb, non-unique, easier-to-guess or easier-to-crack passwords instead. :(
TalkTalk has achieved this by inserting a short line of code into its web form, preventing the pasting of a password into a form.
Worse still, TalkTalk’s customer care team is trying to convince its customers that this is actually good for security and “standard practice”.

Other Twitter users seem pretty unimpressed with TalkTalk’s decision too.
@gcluley @TalkTalkCare Is it safer for me to remember a ~10 char pass I'll probably re-use, or generate a 30+ char unique pass per site?
— Tom Salmon (@SalmonLogs) September 1, 2015
Now, there might be a legitimate reason to prevent users from pasting in passwords if the site is attempting some type of keyboard biometrics, but I don’t think TalkTalk is attempting anything so sophisticated.
It’s a real shame to see a company not helping its customer use safer passwords, especially in the wake of a data breach. Let’s hope they get a clue and see sense soon.



Let Talk Talk learn the hard way – don't do any business with such an insecure company. Long passwords (more than 15 characters) seem to cause many large companies a lot of problems, but they always fail to explain why limits are imposed on such fields in the first place. I have manually input 18 character passwords to some sites and had problems logging in afterwards because they silently truncated the field before storing it!
My own systems allow up to 50 characters for passwords, which is a limit I can easily increase if needs be. Similarly for usernames. And I always let my users paste into those fields on all the forms my server software presents to them. Why can't others be more secure, especially when they're a big company with lots of customers?
My neighbour is with talktalk and too this day is still being bombarded with fake support calls from India claiming to be from tallktalk phishing for that last bit of infomation
That rings a bell..
https://grahamcluley.com/serious-talktalk-data-breach-leads-to-scam-phone-calls-for-customers/
What they really need to do is implement a "three strikes and you're out for an hour" system whereby you get three attempts at the password and then you can't try again until an hour has passed. This would discourage systematic attempts at guessing it. But this involves making some tricky changes to the backend code. Just sticking in an extra bit of Javascript is a lot easier.
The PR guy is right though. This is, sadly, becoming industry standard practice.
I can't think of any site where I have an account that won't accept pasted passwords, although there are one or two (Outlook comes to mind) where one has to use "ctrl-v" rather than "right-click & paste".
Agreed this is a COMPLETELY braindead choice on the part of TalkTalk.
Don't know about this specific Javascript var, but in many cases, pages that won't let you paste do still allow dragging and dropping a selected password from another app….. so that sometimes works.
Even still, TalkTalk should wise up and realize that disabling pasting does absolutely nothing to improve security.
The trouble with folks is not what they don't know, but what they know that ain't so. (Mark Twain?) "Everybody knows" that this is now standard practice. But it isn't. They're falling into the trap of thinking that any additional "security" measure is bound to increase security.
My favourite example from a few years back was a system where they switched on password expiry after a set time, (leaving aside for the moment whether that's a good idea) and also password history, to prevent you reusing old passwords. So far, so good. But they spotted another useful looking Windows feature which prevents you making a second password change within 3 days. This is also with the aim of stopping people changing their passwords and immediately changing them back – but we've already prevented that with the password history.
So you'd struggle to think of yet another new password, and since you needed to get on with the day's work, you'd choose a relatively naff one because you hadn't had enough coffee yet to get your brain into gear. Later in the day when you were firing on all 16 cylinders, you'd be standing at the water cooler and you'd think of a really good one. But you were stuffed because you couldn't change it again. And should your account be compromised in those 3 days you'd be stuffed then too.
Ah, but the second feature prevents anyone from changing their password repeatedly in order to defeat the history and get back to the original one. Maybe, but there's negligible overhead in setting the password history to something like 24, and if anyone is prepared to change their password 25 times to get back to the original one, it's probably such a damn good password I'd probably let them!
It's called the problem of binding. Do all your security measure bind together into a cooperative whole, or might one measure defeat another? Dumb security is always dumb.
Talking about dumb password systems, a long time ago, a Clipper app I wrote had a password security feature to stop people editing the financial transactions in a mortgage system. Some execs needed to be able to change these transactions occasionally, so I devised a password system where the password changed every day and you couldn't really forget what that day's password was. Guessed it yet? It was the day's name (Monday, Tuesday, …) ! For some reason, that idea didn't last long :-)