
Security researchers have spotted a massive malware campaign that sent out 23 million messages laden with Locky ransomware in the span of 24 hours.
Security experts at AppRiver detected the campaign on 28 August at around 07:00 CDT. There wasn’t much to the attack emails spewed out by the campaign. Just some seemingly innocuous subject lines like “pictures” and “documents” along with a request to “download it here.”
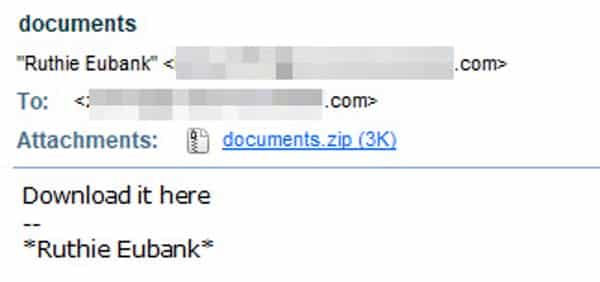
Needless to say, nothing good came to recipients who decided to open the attachment. AppRiver’s Troy Gill clarifies that point:
“Each message comes with a ZIP attachment that contains a Visual Basic Script (VBS) file that is nested inside a secondary ZIP file. Once clicked, VBS file initiates a downloader that reaches out to greatesthits[dot]mygoldmusic[dotcom] to pull down the latest Locky Ransomware. Locky goes to work encrypting all the files on the target system and appending [.]lukitus to the users now encrypted files.”
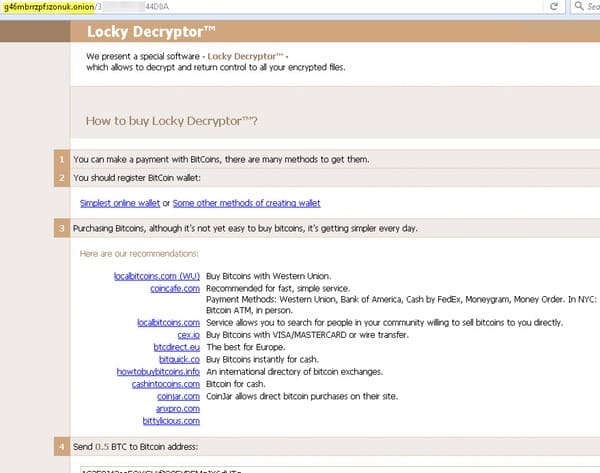
After completing its encryption routine, Locky displayed a ransom note with a link to a .onion portal. Victims who visited that site saw the ransomware’s prompt to pay 0.5 Bitcoins (approximately US $2,413.50) in exchange for “special software” known as the “Locky Decryptor.”
This campaign, which isn’t the only sudden surge in Locky-laden emails to surface in recent memory, clocked in more than 5.6 million emails within the span of three hours. That total jumped to more than 23 million attack messages over the next day.
Locky has a bit of a history of going dark and coming back out of nowhere. (Its reliance on spam-based botnets like Necurs is partially to blame.)
No doubt we’ll see more lifecycles of the ransomware threat, not to mention criminals who create their own strains that mimic Locky. With that said, users act now and develop a robust data backup plan now… before it’s too late.
If they’re ever hit by ransomware, here are a few tips that they can use for their recovery efforts.



I received several dozen of these emails.
I just showed it to VirusTotal; 36 out of 58 products failed to flag it. Of those, nine were unable to handle the 7z format it was compressed with. Although I feel sure that it wouldn't have been spammed out unless the author of the malware was confident that his targets could handle 7z.
Some of the failing products were widely used – AVG, Panda, Sophos and Symantec.
If you ever wonder how good is the antivirus that you're using, show it some of the malware that arrives at your in-box every day.
https://virustotal.com/#/file/5a789bfe28dac3e1e3ab36eb77c43f8a985197fac3f7d912b9201985f8261778/detection
Stop using Windows. Problem solved. Here's a link to an article discussing why MacOS is hard to infect,
http://rixstep.com/2/20170825,00.shtml
Please remember these people would not have a job without Windows and by sensationalizing every threat.