 Symantec has issued a warning about what appears to be a successful scam being perpetrated against users of webmail services such as Gmail, Outlook and Yahoo.
Symantec has issued a warning about what appears to be a successful scam being perpetrated against users of webmail services such as Gmail, Outlook and Yahoo.
The scam is explained in the following short video made by Symantec.
(I say it’s a short video, and it is a short video at only 2 minutes 17 seconds. But clearly Symantec feels you have the attention span of a goldfish, so they’ve added a funky beat in the background to stop you from dozing off).
For those who can’t stand the background music, here is an explanation of how you can steal an email account, just by knowing your victim’s mobile phone number.
In the below example we will imagine that an attacker is attempting to hack into a Gmail account belonging to a victim called Alice.
Alice registers her mobile phone number with Gmail so that if she ever forgets her password Google will send her an SMS text message containing a rescue verification code so she can access her account.
A bad guy – let’s call him Malcolm – is keen to break into Alice’s account, but doesn’t know her password. However, he does know Alice’s email address and phone number.
So, he visits the Gmail login page and enters Alice’s email address. But Malcolm cannot correctly enter Alice’s password of course (because he doesn’t know it).
So instead he clicks on the “Need help?” link, normally used by legitimate users who have forgotten their passwords.
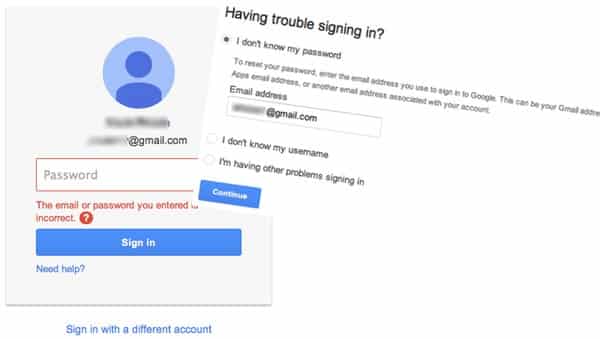
Rather than choosing one of the other options, Malcolm selects “Get a verification code on my phone: [mobile phone number]” to have an SMS message containing a six digit security code sent to Alice’s mobile phone.
This where things get sneaky.
Because at this point, Malcolm sends Alice a text pretending to be Google, and saying something like:
“Google has detected unusual activity on your account. Please respond with the code sent to your mobile device to stop unauthorized activity.”
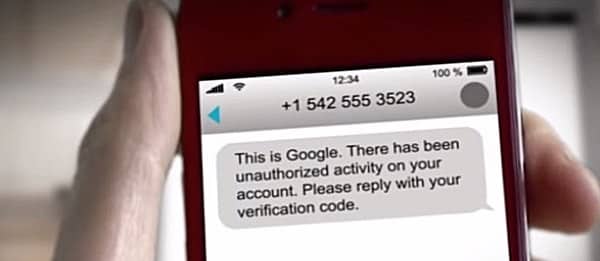
Alice, believing that the message to be legitimate, replies with the verification code she has just been sent by Google.
Malcolm can then use the code to set a temporary password and gain control over Alice’s email account.
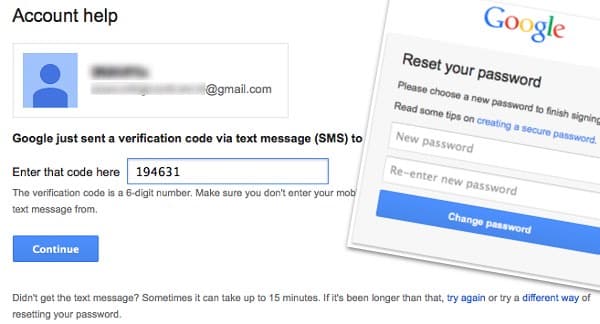
If Malcolm was keen to not raise suspicion, and continue to see every email that Alice receives for the foreseeable future, then it may be that he will reconfigure her email to automatically forward future messages to an account under his control, and then send an SMS to her containing the newly reset password:
“Thank you for verifying your Google account. Your temporary password is [TEMPORARY PASSWORD]”
Even if Alice changes her password at a later date, Malcolm will continue to receive her private email correspondence unless she looks carefully at her account’s settings.
In short – it’s a nasty piece of social engineering which it’s easy to imagine working against many people.
So, what’s the solution?
Well, the simplest advice is to be suspicious of SMS messages that ask you to text back a verification code – in particular if you did not request a verification code in the first place.
However, I wonder how many people when faced with a message that they believe to be from Google or Yahoo would act upon it immediately, with little thinking of the consequences. After all, one of the biggest worries many people might have in this day and age is to be cut off from their email account.
For more details, check out the blog post by Symantec’s Slawomir Grzonkowski.
And for advice on how to better protect your web email account, be sure to listen to this episode of the “Smashing Security” podcast:
Smashing Security #14: 'Protecting webmail - a Smashing Security splinter'
Listen on Apple Podcasts | Spotify | Pocket Casts | Other... | RSS
More episodes...


Hi,
Anyone using 2 factor authorization already, would not fall for this,and if someone tried it on me,I would report it within minutes of receiving the request. But I could certainly see where many would fall for this,and so I forwarded your article to Android Central. Hopefully they will write it up,and they always provide links for others work. As a matter of fact,they are part of Mobile Nation's with sister sites for Apple (imore) ,Blackberry (crackberry) ,and even Windows (?????) Phones.
dumb tricks.
There's a simple solution that Google could deploy…
on all text messages they send containing a verification code they should add the caveat: "DO NOT forward this code onto anybody else. Google will NEVER ask you for this information."
Great idea Bob.
(Of course, Google *will* ask for it on its website – but maybe some careful wording will get around any confusion there)
Even a line of text (in bold red) on the website re-iterating that you should not enter any unsolicited verification code. They could start adding the caveat to all their genuine text messages immediately.
Perhaps a simplification of the following?
"You should only enter a verification code if you requested one. Do not enter your code here if you did not request it. Other than when you first set-up your account we will not send unsolicited messages asking you to verify your account."
Free, easy and instant to deploy.
Quite an insidious scam and not one I've come across before. I can imaging it fooling many particularly if a hacker intentionally 'locked' a victim's account by entering a number of wrong passwords (queue the account holder trying to access their locked account (using a genuine link)).
Maybe as a respected blogger you could suggest something along these lines to the companies in question?
Bob – the thing they need to major on is that you should *never* /text/ the code to anyone else- even if the request appears to come from Google etc.
It's easy to imagine a situation where bad guy Malcolm instigates Google sending Alice the verification code and then Malcolm *phones* Alice on the number (pretending to be Google) and asking her to verify the number she's just been sent.
Maybe that takes more bottle on behalf of the attacker, but we all know how hard people find it to question the authority of someone who has rung them up, apparently in an attempt to help them.
All in all, it's a very sneaky social engineering trick.
Maybe what actually needs to happen is for the initial SMS text to add “If you did not request a verification SMS to be sent to you, please be very suspicious! Bad guys could be at work!” (ok, that may need a little polishing…)
Spot on, Bob. I was about to suggest exactly that.
This is social engineering, not hacking.
And there is the semantics (as below posts) on the former word itself.
However, a breach is a breach. Like it or not it is a very effective way to get access. Doesn't take much work, true, but it is still incredibly effective. It is easier too; indeed the weakest link has to do with humans. That is one thing Mitnick actually did understand. Quite well, I might add. Remote exploit, insider access, keylogger (even internal like those you attach to a keyboard), SE, it doesn't matter what in the end – the result is access.
The title is a bit misleading! It's pure social engineering, just knowing the phone number isn't enough the user needs to actively hand over the code!
This site doesn't write ANYTHING about hacking. Graham & others write about online snoops and vandals, then misapply the word "hacker" to them. And then presumably sometimes "Security Professionals" that keep doing that wonder why some people are so unenthusiastic about helping them as much as possible. What Graham etc. Are trying to do here is good and important, it's a pity he taints it by perpetuating misuse of a word almost sacred to many of my friends. Respect is rarely given to those who won't offer it themselves.
If "hacker" was a term of ethnicity, it would be illegal in many places to abuse the word that way. Which I think is foolish lawmaking, but being inconsistent makes it much worse.
As someone who started out underground[1] and still have ties (friends etc.) I know all too well the meaning here. But the bottom line is this: the damage is done and the damage cannot be undone. As such, it would only add confusion to an already badly messed up situation. The media and governments are to blame and they are also the hypocritical ones about it. I'm afraid reality (and lack thereof!) really doesn't care what you like or dislike; I know this from personal experience, too (maybe I should have chose the name 'Bat' but I digress…). So to be specific: he isn't tainting it as it was tainted by the media. What can he do? You're right – he does a great service. But unfortunately his points would reach much fewer people if he didn't use the specific words. That is the real tragedy (and it is a terrible one)!
[1] I'll not delve any deeper than that (I never used the name 'Coyote', though) and I never will (those that know me know exactly what I mean; the answer is above actually).
cool. now all I need to know is how to spoof a text message.
This is not news, it's just your run-of-the-mill social engineering. The attacker still has to dupe the user into handing over sensitive information.
I don't blame the user, though, for being dumb or clueless because this is a symptom of a larger problem which is that Security is Hard. It's cute that all of the biggest names in the tech industry still think passwords and two-factor auth are secure and easy to use, when in fact neither is true.
… and they never did think that… it has ALWAYS been that it was the weakest link… this goes back decades. But security is a many layered concept. Ah – there is the key! A website doesn't have many links for users around the world. The problem is that fact; the problem is NOT passwords themselves (neither is 2fa; securid cards, anyone? also old).
Edit: ah, but maybe you mean corporations. In that case maybe your point is valid. But still, passwords and such were always considered weak compared to everything else.
Shortening the validation window to a couple of minutes would also help.
A bonafide user would be expecting the code, use as soon as received, and thereby invalidate for future use.
There would only be a short window for the attacker to request the code and get it before being used, but I guess the user would be more occupied with completing the validation task before replying to the attacker, so I think chances of success for the attacker would be quite low.
Someone not expecting one may not notice a message and attacker's request in time before the code expires.
I have never given gmail or yahoo my phone number. And sometimes I get texts that are similar. Since I know I've never given my number, I don't respond.
Alice is from the past!
You have to be from the past to reply to such a text.
Hilarious.