A ransomware developer taunted security researchers in a tech support forum by egging them on to decrypt the newest version of their malware.
News of the DXXD ransomware first emerged in a forum post from Michael Gillespie, a security researcher who has spotted and developed decryption tools for numerous examples of crypto malware.
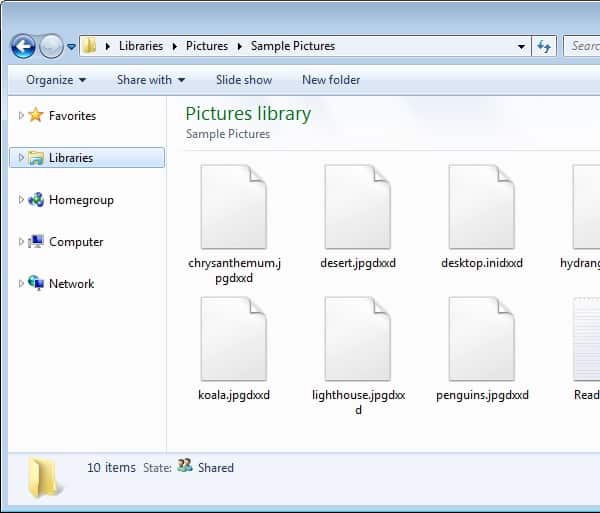
There’s nothing particularly interesting about the DXXD ransomware. When it encrypts a victim’s files, it appends dxxd to each affected filename.
That goes for files that DXXD finds on a target computer as well as network shares.
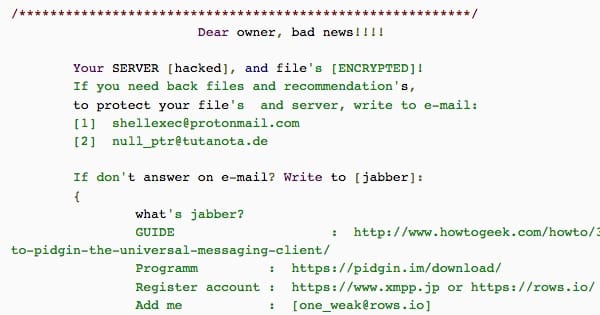
What is interesting, however, is the way the ransomware displays its ransom note.
As noted by Lawrence Abrams, a computer security expert at Bleeping Computer:
“This ransomware… also configures a Windows Registry setting that is used to display a legal notice when people log into a computer. By configuring these registry keys, the ransomware developer knows that any a user who tries to login to the server will see the ransom note.”
Specifically, the ransomware changes the registry values:
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWinlogonLegalNoticeCaption and HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWinlogonLegalNoticeText.
Doing so makes sure each and every user will see the ransom note before they log into their account.
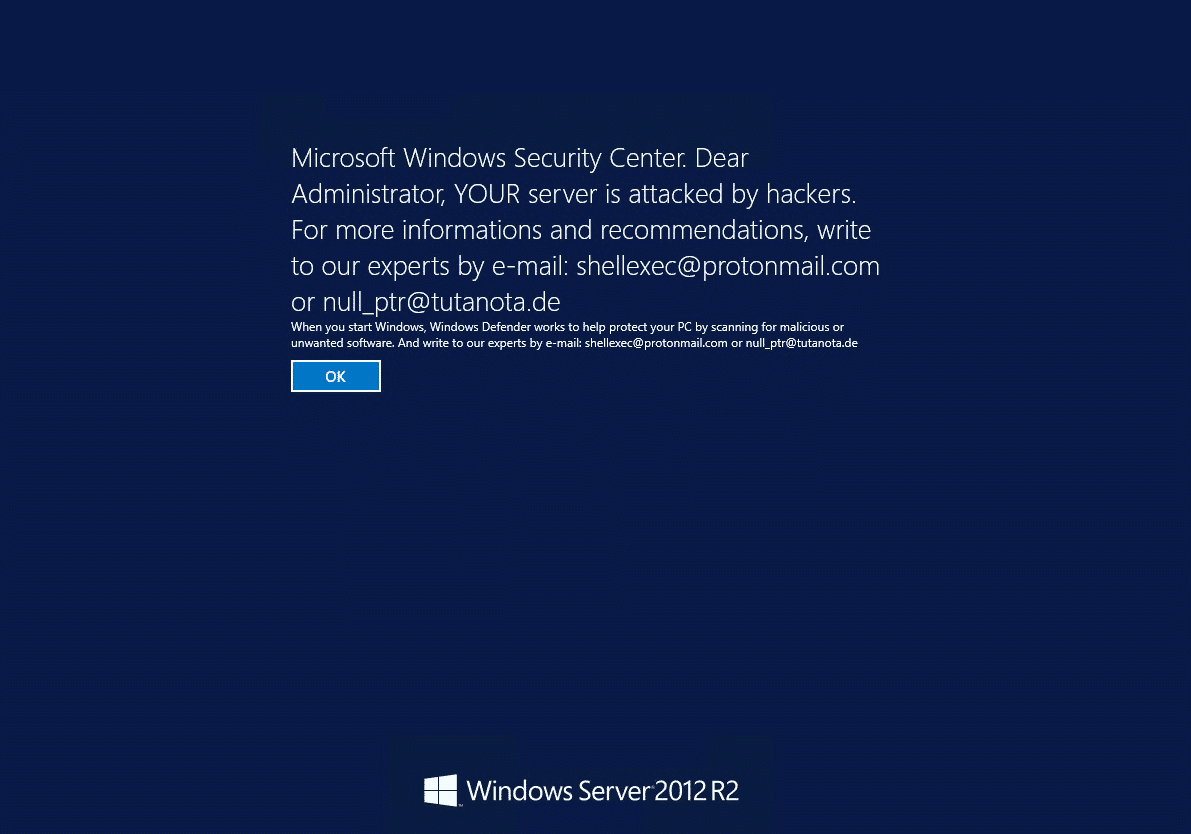
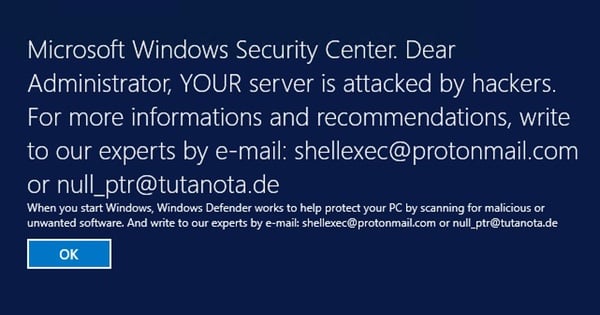
Microsoft Windows Security Center. Dear Administrator, YOUR server is attacked by hackers. For more infromations and recommendations, write to our experts by e-mail
After receiving word of DXXD, Gillespie created a decryption tool for the ransomware that allowed victims to restore access to their files for free.
Unfortunately, the ransomware developer cut the life of that utility short by modifying DXXD’s code.
But they didn’t stop there.
Determined to have the last word, the author posted on Bleeping Computer and egged Gillespie and others to decrypt the ransomware’s newest version.
hello guys..
how are you?
decrypt a new vesrion??? (its pre alpha vesrion)
The malware developer says that they have made DXXD harder to decrypt by using a zero-day vulnerability affecting Windows computers, something which Abrams thinks the author is using to hack into servers using Remote Desktop Services and brute force passwords.
Users should prepare for a ransomware infection by backing up their critical data on a regular basis. That way, they won’t need to pay the ransom if they suffer an infection. They should also maintain an up-to-date anti-virus solution on their computers and keep their software updated.
There is currently no decryption tool for DXXD. That means all victims should remove the malware from their computers, restore their files using their data backups, and change all passwords saved on their affected machines.



I see they're using two of the most secure email services at there: ProtonMail and Tutanota.
The irony.
I should have added that the following critical patches were released yesterday. Update ASAP.
https://support.microsoft.com/en-us/kb/3194798
https://technet.microsoft.com/en-us/library/security/MS16-120
DXXD2 is cracked, go to bleepingcomputer to get updated info about this.
http://www.bleepingcomputer.com/news/security/the-dxxd-ransomware-displays-legal-notice-before-users-login/
you're welcome
Not according to your link. Read it carefully.
"Researchers are currently analyzing the sample and looking for weaknesses. If one can be found, a decryptor will be released for free."
It's decryptable, check my comment. The new decrypter is only being shared in private for now, victims just have to post in the forum for help.
I need the latest decryption tool!
Michael Gillespie published a decrypter on Bleeping Computer. It looks like it covers only early versions, but you can try it anyway. You can find a link for it here:
https://www.bleepingcomputer.com/forums/t/627831/dxxd-ransomware-dxxd-help-support-readmetxt/
Hope it works out for you! If not, contact Michael and see if he can help you any further.
I wrote a separate decrypter for the second variant of DXXD. It is now publicly released, try the DXXD2Decrypter: https://www.bleepingcomputer.com/forums/t/627831/dxxd-ransomware-dxxd-help-support-readmetxt/?p=4106231
This person may have already posted in that topic (and other topics on BC and PM'd me), and we have not confirmed if it is really DXXD they are dealing with. They have files with the extension .aes256, and we have no proof of a connection yet (or sample of the malware).
Stupid fuckin' russians, insecure as all fuck, and trying to impress someone with his kiddie-script coding skills!
"Oh my god, look at me! Look at the really, really good code that I wrote, all by myself too!" the loser screams.
He learned by hacking into gay porn sites.
Likes it up the ass, you see.
With the big crazy $300 that encryption will make him, perhaps he can buy a little russian boyfriend.
Ya think?
Russians? Last I knew .de was Germany (if you knew anything about German or even had any idea about country codes, you might be able to put that together..might being keyword). The location stated on his profile suggests Iceland.
Charming display of racism and bigotry.
So the script Kiddies are at it again, huh!??! Poor selfish little snots. Boo hooo I have no life so I must create a malware to hurt people! Get a life you Newbs! Anyone who gets infected deserved to be infect, Know what not to open. If you don't know, then STAY OFF THE INTERNET!!!!!!
Suprised that he posted in the forum – that's just asking for trouble.
hi, anyone knows solution for xtbl, cerber3 and cerber4 ransomwares ?
You can try this for XTBL: http://esec-lab.sogeti.com/posts/2016/06/07/the-story-of-yet-another-ransomfailware.html .