
The WannaCry ransomware (also known as WCry or WCrypt or Wana Decryptor) burst onto the scene spectacularly today after NHS hospitals across the UK ground to a standstill, as the ransomware encrypted files and caused staff to cancel operations.
I can only imagine the chaos.
As you can imagine it’s “been a bit busy” here too. Every time I try to write something the media grab me for an interview, and I spent an hour or so in a BBC studio in Oxford while they tried to work out why they couldn’t beam me live down the wire to their studios in London.
(They never did find out what the gremlins were, but thought it “probably” wasn’t the WannaCry ransomware.)
The NHS wasn’t targeted. They’re just a huge organisation which has had insufficient investment in computer security over the years. In short, it has a lot of computers and at least some of them weren’t able to withstand an attack like this.
The state of the NHS’s cybersecurity becomes obvious when you consider that it still relies heavily on computers running Windows XP, which Microsoft started to tell people to dump way back in 2007, and finally stopped patching in April 2014.
If you were still running Windows XP after that date – well, you had something bad coming to you.
The UK Government did end up paying Microsoft over £5.5 million of taxpayers’ money to receive support and security updates for a further 12 months after April 2014 (did they not pay any attention to Microsoft’s warnings since 2007?) but that really was the last chance saloon.
But it would be wrong to think that the NHS was targeted. They weren’t. This is extortion – 21st century style. The bad guys release ransomware (in this carried by a worm which exploits a vulnerability), and their intention is to infect as many PCs as possible to make as much cash as possible.
Hitting the NHS wasn’t necessarily their intention, but it is a soft target due to its poor defences. And, of course, the implications of a widespread NHS infection is felt by many people.
Meanwhile, other organisations in other countries were also impacted. For instance, Telefonica in Spain, and FedEx.
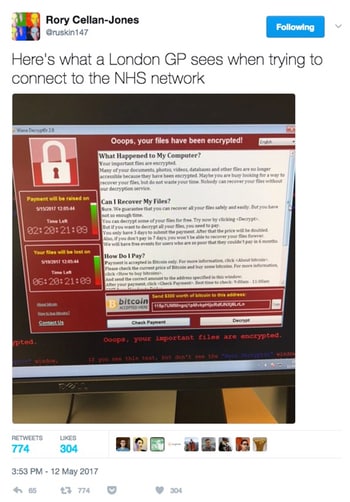
WannaCry appears to have spread at an astonishing pace because it has been spread by a worm exploiting a Microsoft vulnerability – MS17-010. Once one computer in your organisation is hit, the worm hunts for other vulnerable computers to attack.
Before you know it, you’ve got a big problem.
You probably don’t care about this if you’ve had your computers hit by WannaCry, but the story behind the MS17-010 vulnerability is an interesting one.
The vulnerability was first found by the NSA. However, they chose not to tell Microsoft about it. (Which is a shame, because that would have meant computers would have been patched earlier).
Instead, the intelligence agencies kept the details of the exploitable vulnerability to themselves, so they could use it to infiltrate computers and spy upon them. They dubbed the exploit “ETERNALBLUE”.
However, a group of hackers called the Shadow Brokers stole details of this and other exploits used by US intelligence agencies, put them up for sale, openingthe door for other criminals to exploit the vulnerabilities.
Microsoft responded with a patch, but wouldn’t it have been better if the NSA had done the decent thing for all of us on the internet and told Microsoft about the flaw as soon as they discovered it?
Sometimes you protect your country best not by spying on others, but by ensuring that everyone in the world (including the people you may want to snoop on) is better defended.
I’ll update this page with more on WannaCry as it becomes available, but for now you can either follow me on Twitter at @gcluley or (perhaps most importantly) ensure that you have applied Microsoft’s vulnerability patch MS17-010 from earlier this year.
Stay safe folks. And remember to make sure that you have a secure backup regime.
For more discussion on the issue, make sure to listen to this episode of the “Smashing Security” podcast.
Smashing Security #021: 'WannaCry - Who's to blame?'
Listen on Apple Podcasts | Spotify | Pocket Casts | Other... | RSS
More episodes...



Most infected computers are in Russia and it's a sign that WannaCry is a planned cyber-attack
against Russian organizations and institutions, including Ministry of Internal Affairs
of Russia and Investigative Committee of Russia as it's said there
https://malwareless.com/wannacry-ransomware-massively-attacks-computer-systems-world/.
Russian hackers never attacked computers inside their country with ransomware in order
to avoid further problems with police and FSB
Don't tell Trump…not that he'd understand any of what you have said here. Too many big words…sad! What worries me is if these guys attacked the National Grid? Can u imagine the chaos?
I don't think you understood what Graham has said, particularly the paragraph that begins "But it would be wrong to think that the NHS was targeted." This was a worm, not a targeted hack.
This looks like a lucky strike on very vulnerable internal system rather than a specific targeting of the NHS. I wonder if there are multiple encryptors due the the worm capability. Typically there is one PC infected and it does the encryption buit in this case there are reports of the ransom mesage appearing on many systems – -imagine the mess if the documents had been encrypted multiple times by multiple instances, the only way to return the files would be to decrypt in the reverse order the files were encrypted. Maybe this would mean that decryption was nearly impossible even when paying ransom.
Fingers crossed for robust backups!
Morrison's self-service tills run XP. I saw one booting up the other day.
That would be a version of embedded XP which still gets supported by Microsoft. Runs on an awful lot of Point-of-Sale systems and is supported until 2019
The WannaCry looks like the ".Locky" virus to me but they say that this virus needed users to download or open a file but this is not true because i picked .Locky" up on a dedicated machine that was talking to the Tor vidalia software so that i could screen scrape sites without being tracked. Browsers were not used on the machine.
No wonder Bitcoins have been going up for the past few weeks because you have to use these coins to pay for decryption key to get your files back.
Microsoft says we need updates, last thing that i will be doing since this virus they say go deployed by there NSA backdoor going wrong
I liked Tor and would not say this was it not true but see over the coming weeks if i am right or not.
Interesting to note that I tried to withdraw cash from HSBC on Thursday (the day before this) and every cash machine I tried said "Out of Service" on it. I thought at the time that something big must be going down for them to take every cash machine offline.
"These hackers "have caused enormous amounts of disruption— probably the biggest ransomware cyberattack in history," said Graham Cluley, a veteran of the anti-virus industry in Oxford, England."
You're a veteran!
Yeah, the media don't phone me up anymore either.
Amazing how some news agencies say that this is the best time to upgrade to Windows 10. There you go Microsoft, free advert and a huge jump in Windows 10 sales. Imagine if this happened when Windows 10 was still free!
Stop using Windows especially for critical systems. The only time it worked out positively is when the Iranians were stupid enough to use it at their nuclear facilities.
The problem for institutions is that they have a big investment in software (often bespoke) that runs under Windows. Changing operating system, even in some cases updating to the latest Windows, will cost them much more than just changing the operating system. Maybe this event will provide sufficient motivation.
Well. you can pay for it now or really pay for it later.
How ironic when the heads of the US intelligence and security agencies are stating they would not use Kaspersky, that the NSA is somewhat culpable in causing this massive security breach? Maybe if they had said Kaspersky was OK to use, it would not have happened?! (Massive tongue in cheek there!) Or do the NSA chiefs have lots of shares in Microsoft, hoping lots of Windows 10 sales come out of this?!
I am not an expert in these matters, but get the daily email from Graham to keep up to date with cyber security and protect myself. Thanks to you I now use a password manager after too many years of not bothering!
Which password manager do you use Barry?
Don't tell him, Pike!