Do you run WordPress on your website? If so, you’re in good company.
Around 19% of the world’s websites are thought to run WordPress, which is even more astonishing when you consider that many sites don’t have any content management system at all.
And although running your own self-hosted version of WordPress (as opposed to using the technology at WordPress.com) has many benefits, there are security issues that must always be borne in mind as well.
Such as the need to take great care about what third-party WordPress plugins you install. You need to be confident that the plugins are kept up to date, and that they have been coded securely by a team who are on the look out for vulnerabilities.
That’s advice which will be ringing in the ears of many WordPress site owners today, after a major malware attack struck an estimated 100,000 sites.
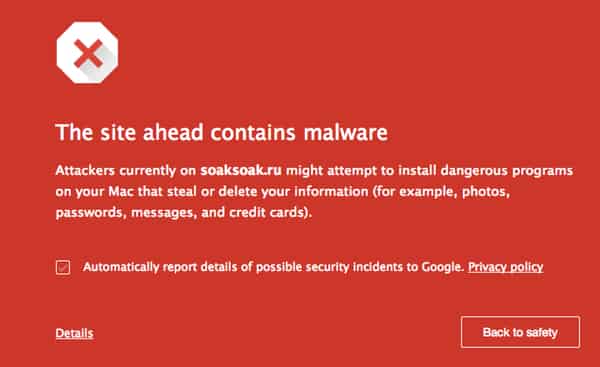
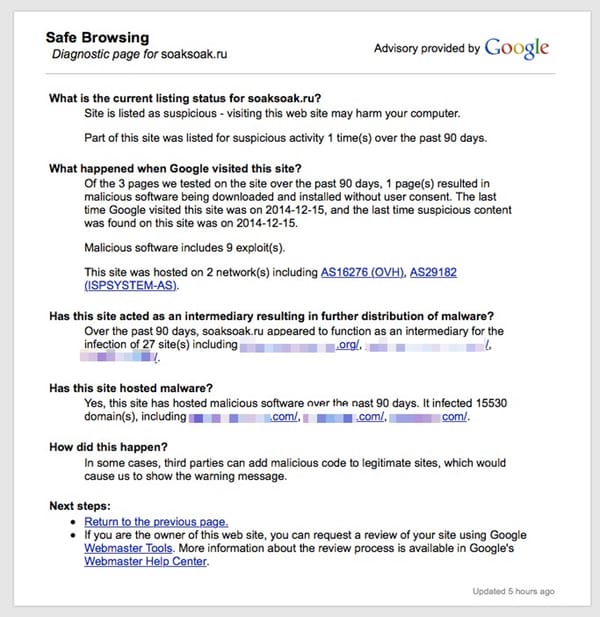
Researchers at Sucuri are reporting that many WordPress websites have been compromised in an attack which attempts to download JavaScript malware from a site called soaksoak.ru.
Once compromised, websites may unexpectedly redirect users to a webpage at soaksoak.ru and/or download malware onto computers without their owner’s knowledge.
It’s not known precisely how the attack, which has been dubbed “SoakSoak” for understandable reasons, manages to compromise WordPress sites but a preliminary analysis by Sucuri points a finger of blame in the direction of a critical vulnerability in the Slider Revolution Responsive plugin they first reported back in September.
Concerns were raised that Slider Revolution plugin was widely incorporated into WordPress themes, and that users may be oblivious to the security issue because they hadn’t purchased the plugin directly from its developers. At the time of writing, the latest version of the plugin is 4.6 (dated 3 December 2014)
It later transpired that ThemePunch, developers of the Slider Revolution plugin, had known about the serious security vulnerability since February 2014 – but had chosen to remain “relatively silent” about it in order to avoid a “mass exploitation of the issue”.
This weekend, Google block-listed over 11,000 domains on Sunday morning it identified has been struck during the attack – a quick-thinking reaction which hopefully will make it more difficult for the attackers to monetise their cybercriminal campaign.
Many WordPress-powered websites use dozens of plugins from third parties, meaning its just as important to keep them updated, and protected against security vulnerabilities as the software on your regular computers.
If plugins have been coded sloppily by developers there is always the risk that your website could become compromised, and that they could put the computers of visiting users at risk.
Sadly, it seems, you can’t always rely on being notified when a security patch is available for all of the plugins that you (or the WordPress theme that you running) use on your website.
Please note: self-hosted WordPress sites are different from sites hosted on wordpress.com. You cannot run the plugin on WordPress.com, and so sites running on that managed platform are not affected.
This article originally appeared on the Optimal Security blog.