A strain of ransomware has reinvented itself and begun encrypting WordPress websites in exchange for Bitcoin ransom payments.
Lawrence Abrams of Bleeping Computer explains in a blog post that the ransomware, dubbed “CTB-Locker,” first appeared two years ago as a traditional sample of crypto-ransomware targeting ordinary users.
Since then, Abrams explains, the malware’s authors have realized that there are bigger fish worth catching:
“CTB-Locker for Websites is a ransomware that is designed specifically to target websites, encrypt their contents, and then demand a .4 bitcoin ransom to get the decryption key.”
The encryption process begins with the ransomware author hacking a poorly-secured website and replacing the existing index.php or index.html files with versions that display a ransom demand. The attacker gives victims the opportunity to decrypt two randomly pre-chosen files “for free” (presumably to prove that files are indeed recoverable), but has encrypted any documents found on the server that match a long list of file extensions.
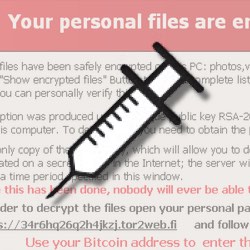
Once the site’s content is encrypted, the ransom note is displayed to anyone visiting the site.
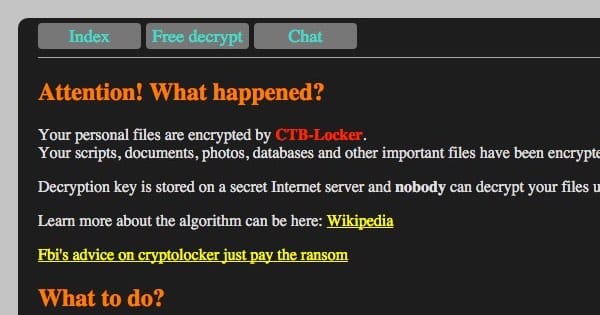
Attention! What happened?
Your personal files are encrypted by CTB-Locker.
Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site.Decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the decryption key.
Learn more about the algorithm can be here: Wikipedia
The ransom note goes on to reference a news story on the Security Ledger website that quotes an FBI spokesman’s controversial advice that companies hit by ransomware should just pay the ransom.
Abrams points out two new developments regarding this new variant of the CTB-Locker ransomware: the version targeting Windows user is now signed with stolen certificates, and the variant that encrypts websites comes equipped with a chat feature that enables victims to communicate with the ransomware authors in real-time.
At this time, it is impossible for users to obtain access to their encrypted files without paying the ransom.
The Register reports that the ransomware was first discovered by researchers Benkow Wokned and Tomas Meskauskas, who have warned that the malware at this point has likely infected hundreds of sites.
A Google search seems to confirm this claim.
Even so, Abrams is careful to point out that the current infection rate is less than CTB-Locker for Windows and other prevalent forms of crypto-ransomware. This includes Locky, a strain of ransomware that targeted a hospital located in southern California earlier in February.
Many of the websites attacked by CTB-Locker appear to be running versions of WordPress which are either out-of-date, poorly configured or running plugins with security holes.
In light of the growing threat ransomware poses to websites, owners should take it upon themselves to regularly back up the sites under their management and ensure that they are properly patched and protected. They should also make sure to protect the backend of their websites with strong authentication measures, a move which will complicate the efforts of a malicious hacker.
Anyone who suspects they have been infected by CTB-Locker for Websites should visit a support page here for further assistance.


I'm a bit baffled here.
Are there people who have their only copy of their web site, on someone else's server? They don't have a copy loccal to them that they use to upload to the server?
I suppose there must be.
When your website is a huge CMS site with permalinks for your specific URL and massive databases, its a massive inconvenience to backup to your own machine. Not that they shouldn't be using some other form if backup, however.
Whether you're responsible for a small static or an ever-growing system, sysadmin's should be mitigating against vulnerabilities. Just as important, they should also have a regularly tested backup and contingency plan.
One of the reasons I use virtual machines to both browse the web and backup my systems. Even if they get compromised you can just boot your last fresh copy up. I simply use google docs to store 90% of everything else I do. Cobbler's to the hackers!