Microsoft has adjusted its malware objective criteria to prevent adware similar to Superfish from adversely affecting users’ security.
On Monday, the Redmond-based tech giant announced the change on its TechNet Threat Research and Response Blog.
“We’re updating our Adware objective criteria to require that programs that create advertisements in browsers… only use the browsers’ supported extensibility model for installation, execution, disabling, and removal.“
The change comes nearly two years after Microsoft first debuted its new approach to adware by altering its objective criteria to include the following:
- All advertisements opened by a program must have a clear way to close the ad and must display the name of the program that created it.
- All programs that create ads must have an uninstall method linked to the name it uses on its ads.

Back in 2014, most adware was thought to only pose an inconvenience to users’ computing experiences as long as the programs were not involved in malvertising (malicious advertising), such as the attack campaign triggered on several Forbes articles earlier this year.
But things changed with Superfish.
Announced in February of this year, Superfish was a self-signed root certificate that essentially used a man-in-the-middle attack to intercept all HTTPS-protected web traffic and inject advertisements into open web browsers.
The software came pre-installed on all Lenovo PCs and laptops, and it posed a serious security risk not only because users could no longer trust secure web connections but also because of the potential for an attacker to have exploited the software’s use of the same certificate on all affected machines to compromise customers’ messages, banking details, and other sensitive information.
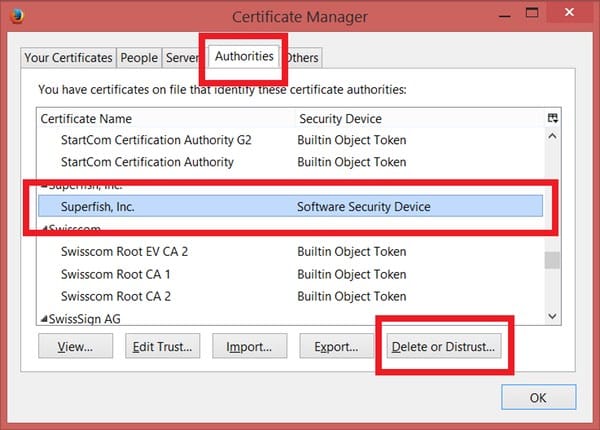
It is this behavior on the part of Superfish and similar adware that Microsoft says it is attempting to crush:
“Ad injection software has evolved, and is now using a variety of ‘man-in-the-middle’ (MiTM) techniques. Some of these techniques include injection by proxy, changing DNS settings, network layer manipulation and other methods. All of these techniques intercept communications between the Internet and the PC to inject advertisements and promotions into webpages from outside, without the control of the browser. Our intent is to keep the user in control of their browsing experience and these methods reduce that control.”
Developers are asked to comply with the new criteria, which requires that legitimate advertising programs function essentially as plugins and be removed the same way, notes The Guardian. Enforcement goes into full effect beginning on March 31, 2016, at which time those programs that do not comply will be removed.
It’s encouraging to see Microsoft taking these steps to combat adware. More fundamentally, these changes to its objective criteria seek to return some power to the user with respect to web advertising.
That’s not to say that all users will take advantage of these updates or even notice them. But some will, and we can hope that their web surfing experience will improve as a result.



I'm at two minds;
Yes it's good to see Microsoft make a step forward, however,
It's mostly their OS' that's shipped by manufactures, who inject crap in the builds to double-dip.
Granted, it's not Microsoft's fault this happens, but their popularity makes them a target.
However, having the ability to intuitively remove this junk still doesn't stop it from happening. End users need to be made aware it's installed first or else the problem still remains.
Microsoft never gives without receiving more than it concedes. The evil software publisher is poised to force its win(pre)10 spy operating system on all unsuspecting winOS users shortly after the first of the year. Like it's other known spy features, "No, thanks." is not an option.
In addition, plans include 100% data, video, and audio monitoring and recording 24/7/365 ever after; included is sharing this with I5 nations. Under guidance and funding from the biggest terrorist organization on the planet, the US fed.gov, Microsoft is ready to recording every detail of your life and using AI to know your thoughts. Everything the law prevents the fed.gov from doing, Microsoft is doing for them. (Do your own research.)
Nobody should be using Microsoft anything for any reason–EVER. You are warned. ©2015
IF MS really wanted to deal with this problem, they would just make it a condition of membership for their OEM programme and say anyone shipping malware on their machines are liable to pay the full retail cost of windows, per machine, for any machines discovered to have been deliberately shipped with this crap.