
It feels like only yesterday that we were all talking about how Epic Games was putting Android users at risk by refusing to put its hit game Fortnite into the Google Play store, and instead recommending players disable a security setting to install it.
It wasn’t yesterday though. It was about three weeks ago.
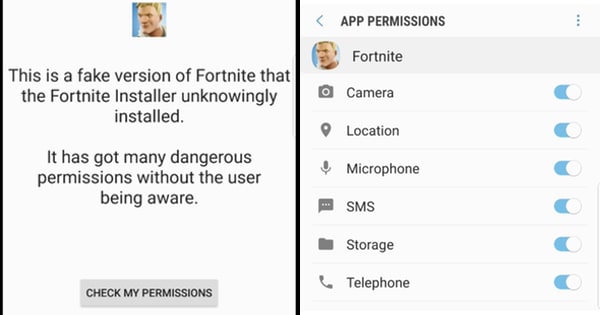
Sadly, in completely predictable news, Google revealed publicly on Friday that it had discovered that Fortnite’s unorthodox Android installer was vulnerable to being hijacked by other apps, allowing any app on your phone to silently download and install anything they like, including apps with full permissions to spy upon you.
Google actually privately reported this issue to Epic Games back on 15 August, and – to its credit – the makers of Fortnite worked “around the clock” confirming the vulnerability, developing a fix, testing it, and rolling it out.
However, Epic Games is not at all happy with Google’s security researchers now making details of the vulnerability public.
In the opinion of Epic Games boss Tim Sweeney, Google should have waited longer before going public with details of the “man-in-the-disk” security hole.
We asked Google to hold the disclosure until the update was more widely installed. They refused, creating an unnecessary risk for Android users in order to score cheap PR points.
— Tim Sweeney (@TimSweeneyEpic) August 25, 2018
In summary:
- Epic Games doesn’t want its game to be in the Google Play store because they don’t like to give Google such a big percentage of the game’s revenue.
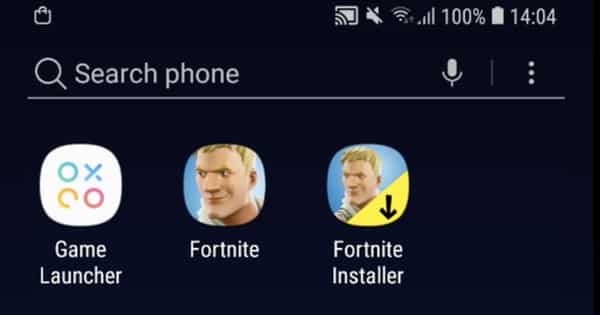
- Epic Games announces that it will release Fortnite outside of the Google Play store, and devises its own installer (which on many devices, requires for a security setting to be disabled).
- Legions of security-savvy folks say that this is bad from the security point of view. I chimed in with my own article and discussed the issue on a recent edition of the “Smashing Security” podcast.
- Epic Games shoots itself in the foot, by releasing an insecure Android installer for Fortnite.
- Google, at no charge to Epic Games, puts some of its most skilful security researchers to work – and uncovers a serious security hole in the Fortnite installer for Android. They tell Epic Games about it.
- Epic Games fixes the vulnerability, and asks Google to keep quiet about it for three months.
- Google says ‘no dice’, and goes public about Epic Games’s failure after a week.
- Epic Games gets upset.
In the past I’ve been critical of how keen Google is to make public details of vulnerabilities in other vendors’ software, which has sometimes occurred before patches are available.
Microsoft too has, in the past, been left fuming after Google disclosed details of unpatched zero-day vulnerabilities in Windows before there has been a decent amount of time to fix them and roll out the fixes to vulnerable users.
I can understand why some may feel that Google has acted inappropriately again on this occasion. But lets not forget some key points:
It was Epic Games which decided not to distribute its software in the (safer) Google Play store against the advice of security experts. It was Epic Games which failed to properly quality control one of the world’s most popular video games and allow its vulnerable code to be installed on tens of millions of devices.
If Google hadn’t found the security hole there is a chance that a malicious hacker would have done, and potentially could have put a large number of Android users at risk because of Epic Games’s utter failure to do its job properly.
One side note:
Google’s self-written vulnerability disclosure rules dictate that it will publicly reveal details of bugs 90 days after reporting them to software developers if they have not been addressed. But if a patch has been made “broadly available” then it will only wait one week before releasing details.
When Epic Games said it had released a patch, Google started the clock for disclosure.
However, Epic Games boss Tim Sweeney argues that their installer only updates itself if players runs it or runs the game.
There’s a technical detail here that’s important. The Fortnite installer only updates when you run it or run the game. So if a user only runs it every N days, then the update won’t be installed for N days. We felt N=90 would be much safer than N=7.
— Tim Sweeney (@TimSweeneyEpic) August 26, 2018
In other words, Epic Games is concerned that not all installations of Fortnite will have received the update yet.
Huh. Isn’t that an argument for being in the Google Play store? That way the vulnerable code would have been updated automatically rather than hopefully waiting for a user to click on an icon.



you're just licking google's ass
Google's donkey??
Anyway, if you care to read some of my numerous other articles about Google's disclosure of other software vendors’ vulnerabilities you'll find your analysis is unlikely.
For instance, https://grahamcluley.com/google-discloses-microsoft-windows-vulnerability/