 What’s happened?
What’s happened?
Computer hardware giant Dell is shipping PCs and laptops with a security hole that could make it easy for online criminals to spy upon your online activity – including intercepting your web email, your purchases and your online banking.
Woah! That sounds bad. How are they doing that?
Yes. It is bad. The issue, which first became well known via a Reddit post, affected Dell computers are being shipped with a pre-installed trusted root certificate – called eDellRoot – that can intercept HTTPS encrypted traffic for each and every website you visit.
In this way supposedly secure communications can be eavesdropped upon, and passwords, usernames, session cookies and other sensitive information could fall into the hands of malicious hackers.
And how would an online criminal exploit this issue?
Well, one possibility is that criminally-minded hackers could hang out in hotel lobbies, coffee shops and airport lounges, and exploit the flaw through a silent man-in-the-middle attack, decrypting Wi-Fi communications without the knowledge of the victim.

This all sounds familiar. Didn’t some other PC manufacturer do something equally dumb?
You’re thinking of Lenovo, which in February 2015 found itself in the most awful mess over the SuperFish debacle, a security hole that it introduced onto its shipping PCs to inject unwanted adverts.
Didn’t all the PC manufacturers see that Lenovo was dragged over the coals for that one?
They certainly did. In fact, Dell still has a section on many of its product pages reassuring its customers that it would never do anything so silly as pre-loading software that might impact security and privacy…

Dell is serious about your privacy
Worried about Superfish? Dell limits its pre-loaded software to a small number of high-value applications on all of our computers. Each application we pre-load undergoes security, privacy and usability testing to ensure that our customers experience the best possible computing performance, faster set-up and reduced privacy and security concerns
When did Dell start rolling eDellRoot out?
Dell has claimed in statements issued to the press that it began to load the current version of eDellRoot onto “consumer and commercial devices in August to make servicing PC issues faster and easier for customers.”
It seems it only took six months for Dell to forget about the Lenovo Superfish furore.
In a blog post, programmer Joe Nord shared a screenshot of how the eDellRoot certificate appears in the Microsoft Management Console on the Dell Inspiron 5000 laptop he bought last month.
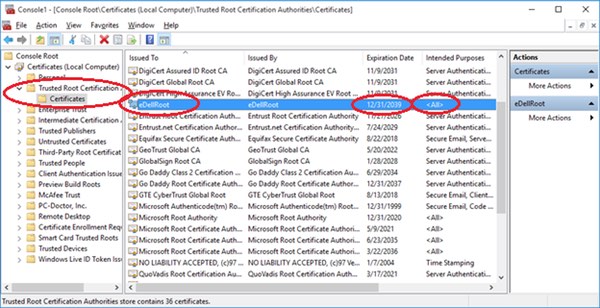
The certificate isn’t set to expire until the end of 2039.
As Nord explains, if you dig a little deeper you will find that your computer is also in possession of the controversial certificate’s private key:
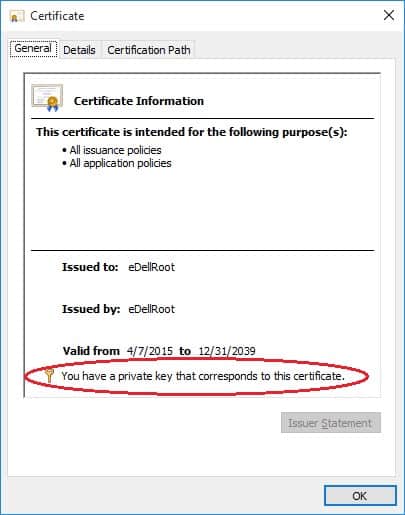
And it’s that private key that a moderately nerdy computer user could extract, and use to sign fraudulent certificates for any website using HTTPS.
What Dell computers are affected?
According to a report in The Register, owners of the following Dell models have reported issues: the XPS 15, Latitude E7450, Inspirion 5548, Inspirion 5000, Inspiron 3647, and the Precision M4800.
How can I tell if my PC is vulnerable?
Fortunately, some kind-hearted souls on the net have created sites that will easily tell you if your PC is at risk from the eDellRoot flaw.
Visit https://edell.tlsfun.de/ – if your browser is safe you should see a green box, if not you’ll get a red warning message.
https://twitter.com/markloman/status/668842464913006592/photo/1
How do I remove eDellRoot?
Frustratingly, Dell’s dangerous root certificate will reinstall itself after being deleted from the root and personal certificate stores
A detailed analysis by researchers at Duo Security, however, explains that unless you also erase the Dell.Foundation.Agent.Plugins.eDell.dll module from affected systems, the security vulnerability will continue to be present.
You may also wish to use the Firefox browser, which waltz past the rogue certificate by because it uses its own set of trusted certificates instead.
Dell, meanwhile, says that it will be advising customers on action to take and removing the offending certificate in future:
“The recent situation raised is related to an on-the-box support certificate intended to provide a better, faster and easier customer support experience. Unfortunately, the certificate introduced an unintended security vulnerability. To address this, we are providing our customers with instructions to permanently remove the certificate from their systems via direct email, on our support site and Technical Support. We are also removing the certificate from all Dell systems moving forward.”
Dell is about to learn an important lesson: it takes years to earn your customers’ trust, but only seconds to lose it.


Thanks for the detail Graham. I just ran my brand new Dell PC through the tool, and it immediately came up red. In my case it's a desktop model, Dell XPS 8700, shipped less than two weeks ago directly from Dell. That isn't in your list of models above, so I'm guessing they've shipped it on every production machine, not just a few models :(
Wow, this wreaks of Lenovo SuperFish as mentioned earlier…
You'd hope those deploying them in the corporate space have replaced the shipped build with their own image.
Here's a tip manufactures: Stop injecting crud, dodgy certs and other bloatware on your preinstalled images. Most people don't care for it.
Reeks, not 'wreaks', as is rapt, not wrapped. Thank you for plz lurn Onglish wif me, welcome iz you.
Ah oh, here come the Grammar Police. Please, Sir… stop trolling and let the professionals handle this.
Kind regards,
Grammar Police
Anti-Trolling Division
https://www.youtube.com/watch?v=u9_kahA_wQo
Strange, I own and use a Dell Inspiron 17 5000 but this mysterious eDell certificate is nowhere to be found. Seems it's only present in certain select but not all dell Inspiron computers.
Instructions for all those that may have the dangerous Dell certificate of how to get rid of it:
https://dellupdater.dell.com/Downloads/APP009/eDellRootCertRemovalInstructions.docx
All new systems out will come without it now, according to Dell.
Hi Bob,
As per my reply below this fix is incomplete
Unfortunately it doesn't remove if from the Personal Certificate store so it's still insecure.
Dell have published their 'fix' below. Unfortunately it doesn't remove if from the Personal Certificate store so it's still insecure:
http://en.community.dell.com/dell-blogs/direct2dell/b/direct2dell/archive/2015/11/23/response-to-concerns-regarding-edellroot-certificate
Good to waste my time executing this via Group Policy only for it to fail to fix the issue!
Here's the original blog post that has some more updated details than the PDF whitepaper:
https://www.duosecurity.com/blog/dude-you-got-dell-d-publishing-your-privates
I'm not sure I get the issue! If Microsoft's root certificate is considered OK (in the same screenshot where Dell is highlighted), then why not Dell?
Please disregard my previous post. I just went to the Reddit and noticed in the first paragraph that the private key was easily retrievable. Bummer – what a shame!