
Updated Researchers have spotted a new variant of Cerber ransomware that generates new hashes every 15 seconds.
Originally detected in late February/early March, Cerber is a form of crypto-ransomware that encrypts victims’ files using AES encryption and demands a payment of US $500 in return for handing over the decryption key.
Sounds pretty standard… apart from this ransomware also has the ability to recite its ransom message out loud to the poor victim via VBScript!
Since its initial discovery, analysts in the security community have spotted the Angler exploit kit dropping Cerber in at least one malvertising campaign.
They have also noticed Cerber’s authors are working to update the ransomware on an ongoing basis.
For instance, in late May, researchers at security vendor Invincea found the ransomware had adopted bot capabilities that allow Cerber to launch distributed denial-of-service (DDoS) attacks.
It would now appear the ransomware has evolved once again, only this time, it has done so with defense in mind.
In a report published last week, Invincea’s researchers reveal something interesting happened when they attempted to replicate the infection chain of one of Cerber’s newest variants:
“Invincea researchers see dozens of Cerber infection attempts every day. However, when we tried to duplicate the download for this variant, we noticed that the hash we received from the payload delivery server had a different hash than the one in the event above. When we downloaded it a third time, there was yet another hash. Fifteen seconds later, there was another, and then another. In all we downloaded over 40 uniquely hashed Cerber payloads – all with different hashes.”
This type of behavior is typical of what is known as a “malware factory,” or an automated malware assembly line by which malicious actors make small modifications to the internal structure of a malware payload to generate files with unique hashes.
Such a set-up is designed to make detection by traditional anti-virus solutions trickier.
The best defense is to avoid infection in the first place, of course. That means avoiding clicking on suspicious links and email attachments, and to roll-out security patches as soon as they become available.
It is also wise to backup your data, and keep it separate from your computer. Doing so won’t prevent a ransomware infection, but it will provide you with a second option in the event Cerber or another variant encrypts your files.
Update: After publishing this article, a veteran in the anti-virus field directed the site staff at Graham Cluley Security News to an article written by MalwareTech.
MalwareTech explains they used PE Explorer to explore how Cerber’s “malware factory” works. What they found came as a surprise:
“The sample is changing the file hash by writing random data after the end of the PE file[.] [T]his data is not part of the executable, does not exist inside the code which is mapped into memory, and will not fool even the stupidest of modern AV scanner….”
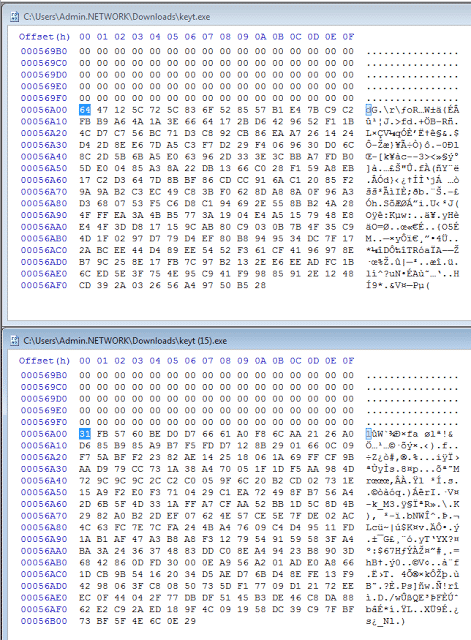
Technically, adding random data the end of a PE file could fool a scanner if it used the entire hash of the file, but MalwareTech notes that this isn’t how modern anti-virus solutions work, and that this method of detection would render any anti-virus solution “completely useless” against today’s threats.
The author goes on to explain that Cerber’s technique could “harm” cloud anti-virus providers, but only by wasting bandwidth until they realize what’s going on.



Is it possible to decrypt the files without paying?
Not yet, though security researchers are constantly developing decryption tools for ransomware. A utility could emerge in the next couple of weeks or months, but that's little help to someone who might have just gotten infected.
how to remove cerber from my system and how to recover infect file ???
At this time, you can only recover your infected files by paying the criminals and hoping they honor their word. Once they have provided you with the decryption key, you can then go about to remove the ransomware either via the use of anti-virus software or by manually removing the ransomware files from your computer.
You cannot decrypt files, do not pay to criminals! Reinstall system and get a good Antivirus (BitDefender, Kaspersky)