Just as a bit of a refresher, exploit kits are in essence packages that are designed to deliver malware, as articulated by Help Net Security.
They are distributed via the use of spam, phishing emails, infected websites, or malicious online ads. True to their name, they exploit vulnerabilities in popular software to deliver a malicious payload, which might include ransomware or other software designed to steal a victim’s banking details or sensitive data.
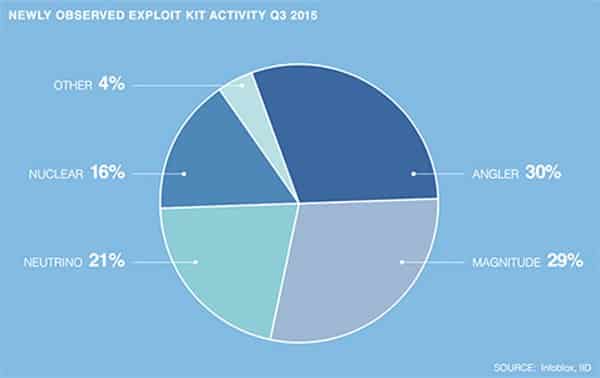
Chief among the exploit kits featured in the newly-published Infoblox DNS Threat Index is the Angler exploit kit.
A master of deception – the Angler exploit kit uses a technique known as “domain shadowing” to evade reputation-based blocking strategies – Angler is updated with the latest zero-day vulnerabilities for the purpose of infecting users’ machines.
In October, security researchers with Cisco’s Talos Security Intelligence and Research Group targeted some of the gangs who have in the past incorporated Angler into their malware campaigns. They even succeeded in blocking some redirects to the exploit kit’s proxy servers, effectively protecting users.
But Angler is still alive and kicking, reveals Infoblox.
“Recently, a major British newspaper, which has hundreds of millions of monthly visits to its website, was hit with the Angler exploit kit,” Infoblox writes in its report. “The attack resulted in malicious ads being displayed to its readers over the period of four to five days. This could have exposed many of the daily visitors to infection from clicking on the malicious ads.”
The incident being referred to is the Daily Mail malvertising attack of October 2015.
The firm’s researchers also detected spikes in activity for the Magnitude, Neutrino, and Nuclear exploit kits, which together with Angler account for 96% of the exploit kit activity observed for Q3 2015.
As reported by CSO Online, exploit kits have grown in sophistication in recent years. For example, they look for open DNS ports – Port 53 is a common choice through which they can leak an encrypted stream of data which they can then reassemble and decode in order to infect a machine.
Exploit kits also are commonly updated with the latest vulnerabilities in a matter of days or even hours, as is the case with Angler.
“Cybercriminals don’t stand still, and exploit kits are constantly evolving to take advantage of newly discovered vulnerabilities and to avoid traditional security systems,” Rod Rasmussen, chief technology officer at IID, tells Yahoo Finance. “Organizations need to protect themselves by plugging into reliable sources of threat intelligence, then use that intelligence to disrupt malware communications through protocols such as DNS.”
Craig Sanderson, Senior Director of Security Products at Infoblox, also recommends that organizations invest in proper security training as well as risk management and mitigation processes.
“Employees need to know what traps to avoid, such as emails that don’t seem quite right and dodgy websites,” Sanderson recommends. “Networking and security teams need to go beyond traditional perimeter defenses to address what happens once malware gets inside the network.”
Exploit kits prey upon the fact that most users are slow to update their machines. Implementing patches as soon as they become available and installing some form of security product on your machine can therefore go a long way towards protecting yourself against Angler and its buddies.