UK Prime Minister Boris Johnson announced on Twitter this afternoon that he was chairing the first ever digital Cabinet, while he self-isolated himself at Downing Street after revealing he was suffering “mild symptoms” of Coronavirus.
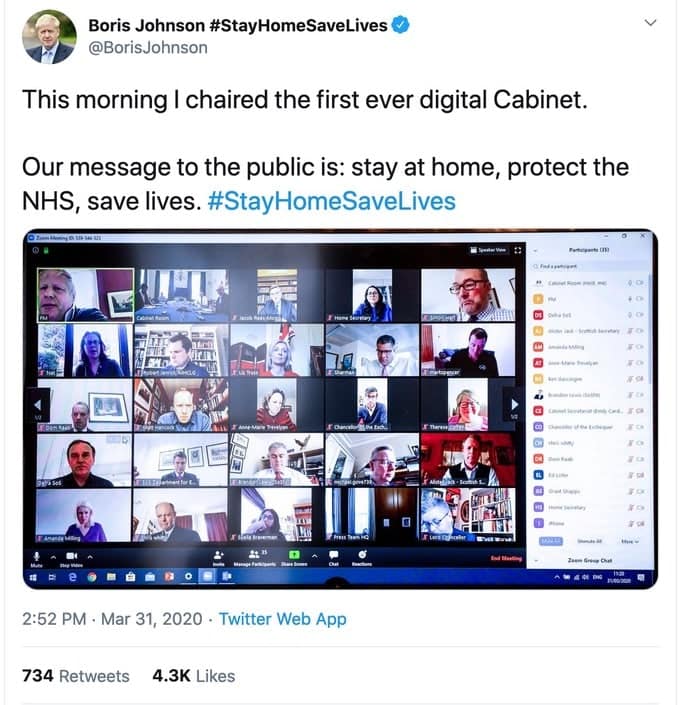
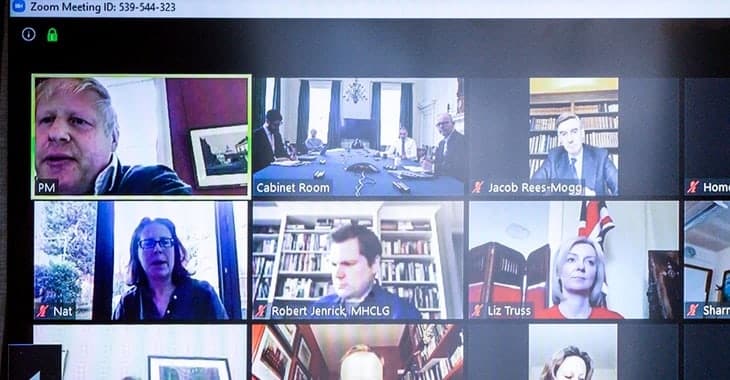
Johnson included in the tweet a screenshot of his desktop, showing there were 35 participants on the Zoom meeting.
But the screenshot also revealed some details it probably wasn’t so wise to share.
Because a close examination of the screenshot reveals the meeting ID of the Zoom call.
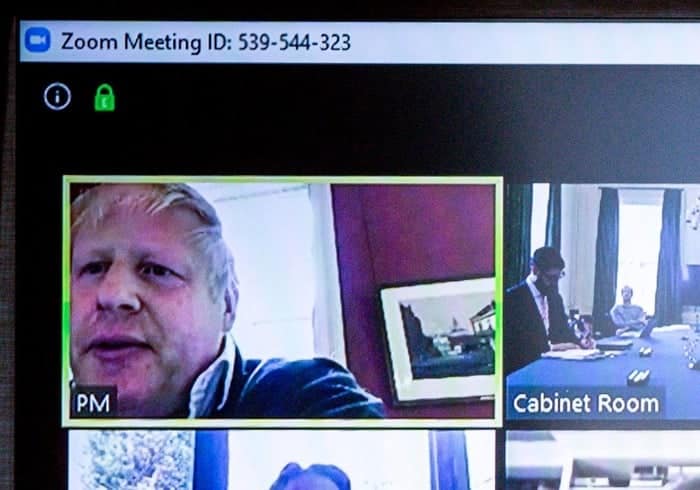
Good news for anyone who was hoping to join the meeting but had mislaid the Zoom meeting ID.
But bad news for any mischief makers hoping to take advantage – the Zoom meeting is password-protected. Thank heavens for that.
Let’s hope it’s a strong password, that’s hard to guess.
h/t @newschambers



What a loser!
Well, it had ended. So what’s the harm. Nothing. Just a click bait headline
Phil – You've missed the point my a New York mile! The harm is that broader awareness is needed around proper security measures when using conferencing platforms. Individuals have been guessing URLs, spying on sensitive meetings, and using common passwords to jump onto calls.
Agree! Not to mention several zero-day vulns exist for the MacOS client for Zoom. Zoom has had several critical vulns in the past for Windows clients. I'm wondering how many companies are learning that Zoom is being used on their network without authorization?
The Press Team HQ seem to have got the security message and hidden in the cupboard!
Probably safer than the limited social distancing around the Cabinet Room.