 Hopefully, by now, we all understand the threat posed by targeted attacks, and how online criminals might attempt to target specific individuals inside your organisation.
Hopefully, by now, we all understand the threat posed by targeted attacks, and how online criminals might attempt to target specific individuals inside your organisation.
Unlike the huge, mass-mailed attacks of yesteryear like the Sobig and MyDoom worms, targeted attacks don’t try to infect as many computers as possible as that would draw far too much attention to themselves.
No, they’re interested in compromising a small number of particular computers, in order to establish a beachhead inside your company through which data can be stolen, and from where potentially other attacks can be launched.
So, what is one of the key ways in which they might attempt to trick your staff into clicking on a dangerous link? The simple LinkedIn invitation to connect email.
On Thursday I was lucky enough to participate in a session at the “IT Leaders’ Forum”, held at the London Stock Exchange, which saw the IT chiefs and CSOs (Chief Scapegoat Officers) responsible for protecting some of the UK’s leading companies gather to share their experiences and learn how to convince the board to take security seriously.
The forum, run by the good guys at Computing magazine was well attended and informative, and I found one of the most interesting presentations to be that given by Proofpoint’s Mark Sparshott who discussed some of the security firm’s latest research.
And one of the factoids Mark revealed was that, according to Proofpoint’s research, bogus LinkedIn connection emails are remarkably successfully at tricking users into clicking.
The most effective email templates for attackers who want their victims to click are social network communications, financial account warnings and bogus order confirmations.
However, click rates on malicious campaigns pretending to come from LinkedIn are twice as high as those of other campaigns seen by Proofpoint in the recent past. Indeed, the click rate on bogus LinkedIn emails are four times that of campaigns that use other social networking brands.
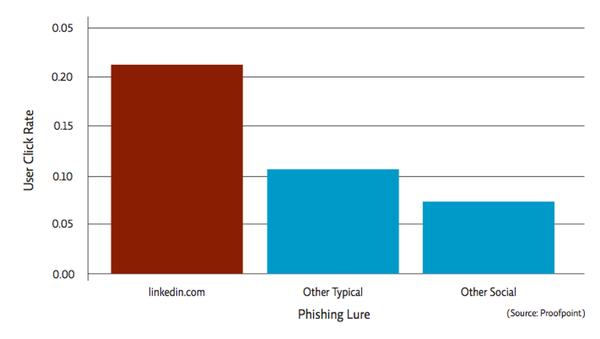
In a nutshell, users who receive emails which appear to be LinkedIn invitations to connect from others find it remarkably hard to resist clicking. Proofpoint says that users click on malicious LinkedIn invitation templates a staggering eight time more than they click on all types of LinkedIn emails and notification emails.
Users can tell apart spam annoyances from useful email, however, it is getting more and more difficult for users to tell apart phishing email as unsolicited email and notifications from popular services are common. Given the nature of professional social networking, and specifically the popularity and trust enjoyed by the LinkedIn brand, it is frequently used as a malware campaign template and serves its purpose in enticing users to click.
The attackers know that these disguises work, and will continue to disguise their malicious campaigns by using familiar brands. LinkedIn is clearly a brand that many users find irresistible to click upon when they receive what purports to be a connection invitation.
In my view it’s unrealistic to expect the average computer user to distinguish between genuine and bogus emails when they are professionally crafted. Although education can help protect your employees from malicious targeted attacks, it has to be combined with technology to lower the chances of a successful breach.
And don’t forget, if you receive an email claiming to come from LinkedIn, it might be best to visit the LinkedIn site directly to find out more rather than click on that link…
You can find out much more about the research, and other findings about how attackers exploit end-users’ psychology, in the Proofpoint paper “The Human Factor”.



How sad that browsers/OS's are so woefully written as to be so fragile even a single misclick will destroy them utterly…… I'm guessing if programmers were smart, that wouldn't happen….
Sad that after 30 yrs of personal computers the bad guys still always win 100% of the time.
Time for a new OS system not written by the lowest bidder.
An email system with generated encrypted keys that are given to authorized sites, if an email comes from a source without a key then all links are disabled…. it would even support anonymous users.
We've had SPF and DKIM for years, yet their policy appears to be lacking.
# dig spf linkedin.com
linkedin.com. 86388 IN SPF "v=spf1 ip4:8.18.31.21 ip4:8.18.31.22 ip4:69.28.149.0/24 ip4:199.101.160.0/25 ip4:199.101.162.0/25 ip4:108.174.3.0/24 ip6:2620:109:c006:104::/64 ip4:216.136.162.65 mx mx:docusign.net ~all"
Note ~all instead of -all.
Their mails actually come from e.linkedin.com
# dig spf e.linkedin.com
no record!
# dig txt e.linkedin.com
e.linkedin.com. 10800 IN TXT "v=spf1 ip4:199.7.200.0/21 ip4:12.130.135.0/24 -all"
e.linkedin.com. 10800 IN TXT "mailru-verification: d9d9bdd0974a4f0f"
and that does have a "-all" instruction for mail servers to reject if not originating from the address ranges specified, which is good, *if* those mail servers pay attention to it.
Note that mail from @linkedin.com can still be soft-failed and spoofed because of its "~all" policy.
How many people know that mail from "linkedin.com" may not be authentic and should be from "e.linkedin.com"?
Their DKIM policy uses "linkedin" as a selector
# dig txt linkedin._domainkey.e.linkedin.com
linkedin._domainkey.e.linkedin.com. 2874 IN TXT "g=*\; k=rsa\; n=" "Contact" "" "with" "any" "questions" "concerning" "this" "signing" "\; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDVkW7LjDP3u0
8zGz+mcRxmdA2HZmOvphGMP//0K7B11E9aWnIycV6Le0VhcjI/I/I5RYcc
iHEbTzrNK60FqLeeIp35jUtuD38AX28cwVh46i9fNmQJYajAWUXmuAhVP
0p2KYNCDCKC992N+9ieijO4jeabrDELoqavQ9JbCYxAxQIDAQAB\;"
Good so far.
# dig txt _adsp.linkedin._domainkey.e.linkedin.com
No record.
One would hope to find "dkim=discardable;" to tell mail servers to discard if a message from e.linkedin.com fails authentication.
linkedin.com itself does not have a DKIM record, no ADSP policy and a lax SPF record, which opens itself up for spoofing.
I could be mistaken, but it looks like they should revisit their mail policies and close any loopholes that they can to follow best practices.
Linked In can't do much against their users mail servers if those mail servers don't implement these checks, so we are still back to the possibility that mails may not be authentic.
In which case it's up to the user to be able to look at the ip address of the mail and make a decision whether it's authentic, and how many email clients, and mobile email clients make it easy for people to do that?
I've advocated for decades that displaying the originating ip address, domain and country of origin should be mandatory for any email client, even if the user is a 5 year old.
Any idiot ought to know that a mail from paypal with a Vietnamese address will be fake, yet on nearly every mail client, you still wouldn't know without a lot of digging.
Graham, what is Linkedin doing about eLinkedin.Can't they close them down, or at least warn members. A friend joined Linkedin using a new gmail acc only used for Linkedin – and received expertise request from eLinkedin. She noted elinked, and thought it sus.