
A severe security vulnerability has placed millions of LG G3 smartphone users at risk of data theft, phishing attacks, and denial of service (DoS) on their devices.
Threat detection provider Cynet explains in a blog post that the ‘SNAP’ vulnerability, which was discovered by BugSec researchers Liran Segal and Shachar Korot, is a flaw found in LG’s Smart Notice notification app that allows an attacker to run arbitrary JavaScript code on new LG devices.
Haven’t heard of the Smart Notice app before? Here is LG’s promotional video:
If it seems neat to you, then wait until you read what the security researchers had to say about it:
“The root cause for the security problem is the fact that Smart Notice does not validate the data presented to the users. Data can be taken from the phone contacts and manipulated.”
In particular, the two researchers noticed that a number of Smart Notice’s functionalities, including the New contact suggestion, Callback reminder, Birthday notification, and Memo reminder, could be exploited to successfully execute an attack using ‘SNAP’.
To investigate further, Segal and Korot assembled a security research team and inserted a “malicious” contact (with a malicious script embedded in the contact’s first name) that was triggered by Smart Notice’s Callback reminder and Birthday notification functionalities.
This allowed the team to run code from the WebView context to the phone and to achieve active command and control over the device necessary for sending new payloads.
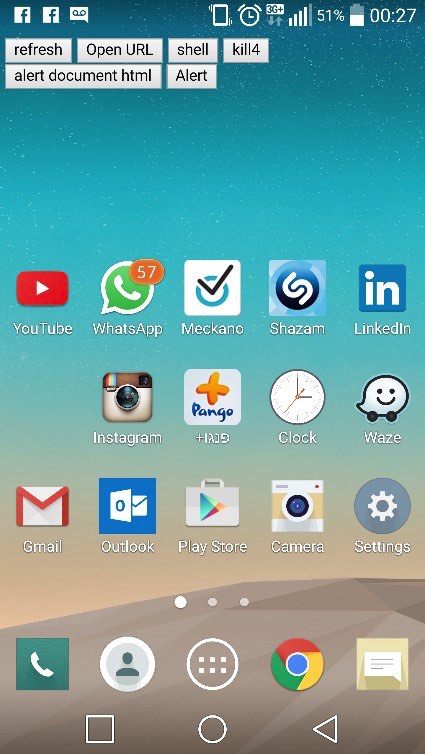
The researchers created several easy-to-use payloads over the course of their trial exploitation, including harvesting data from the phone’s SD card, using an “open_url” function to open any webpage (including a malicious third-party website or phishing page), and creating an infinite loop that could effectively place the phone out of commission until the victim executed a hard-reset.
The team also found that just as many attack vectors could initiate the exploitation. Some work around the user, such as surreptitiously inserting a contact with malicious code embedded into the first name onto a user’s device. Others social engineer the user into scanning a QR code or MMS, both of which would prompt the user to save the contact with just one click.
You can watch a YouTube video of the ‘SNAP’ vulnerability below:
The research team contacted LG, who responded quickly by issuing a new Smart Notice release containing a patch for ‘SNAP’.
In a press release, BugSec’s Chief Technology Officer Idan Cohen thanked LG for their prompt response:
“LG reacted immediately, which we appreciate. This is a major potential security breach into the personal data of millions of LG users worldwide.”
With the severity of the ‘SNAP’ vulnerability in mind, all vulnerable users are urged to update their copy of the LG Smart Notice app as soon as possible.
In the meantime, vendors can prevent vulnerabilities that are similar to ‘SNAP’ by using input validation.



And how exactly does one update or patch their smart notice app?
I don't have an affected LG smartphone, so I haven't been able to test it for myself, but I read online that this is how it's done:
"Go into your apps and search for "Update Center". It is a blue android character icon. You should see a number in a red circle on the icon if you have an update available."
Let me know how you get on.
Good question!
Hope to see the reply
Thanks very for the heads up.
Of course I now need to accept LG's lovely EULA agreement before updating :-(