Researchers have spotted some new ransomware that comes with a Live Chat feature and a somewhat useless uninstaller program.
Yet another ransomware: PadCrypt – It apparently even comes with an uninstaller "padcryptUninstaller.exe" pic.twitter.com/5FM0DXrdD7
— abuse.ch (@abuse_ch) February 14, 2016
First detected by the folks at the abuse.ch security blog, the ransomware dubbed “PadCrypt,” is being spread via spam email campaigns, explains Lawrence Abrams of Bleeping Computer.
Each email comes with a .ZIP attachment that contains an executable file with the double extension of .pdf.scr.
The use of a double extension is a deliberate attempt by attackers to fool users into believing that the file might be a legitimate PDF file, but when executed the file downloads the PadCrypt ransomware onto a victim’s machine.
At that point in time, PadCrypt encrypts any and all files it locates in a series of target folders:
- C:Users[login_name]Downloads
- C:Users[login_name]Documents
- C:Users[login_name]Pictures
- C:Users[login_name]
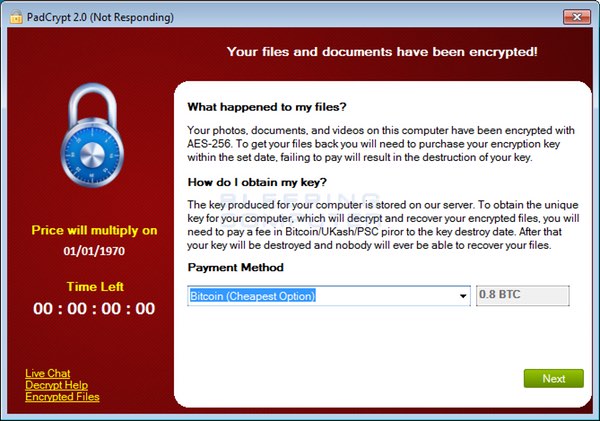
After finishing encrypting those folders, the malware encrypts more files found on the C: drive and any available removable media before displaying the following ransom message:
As is seen above, the ransomware authors demand that the victim penny up 0.8 BTC (approximately US $350) for the decryption key to their now encrypted files.
This is considerably less than what the hackers behind the recent attack against the Hollywood Presbyterian Memorial Center have asked for.
But here’s where it gets interesting. In the bottom-left corner the ransom screen is a “Live Feature” option which, when clicked, opens up a screen where the victim can speak in real-time with the malware’s developers, as Bleeping Computer’s Abrams comments:
“A feature like this could potentially increase the amount of payments as the victim can receive “support” and be guided on the confusing process of making a payment.
At this time, however, the ransomware’s command and control (C&C) servers are offline, so both the malware’s encryption process and live feature are currently unavailable.
PadCrypt also comes with an uninstaller that is loaded upon initial execution. But this feature is misleading. The uninstaller only removes the files that PadCrypt installs on a victim’s computer. It does not deter or reverse the encryption process.
Clearly, ransomware authors are developing increasingly more sophisticated malware samples every day. These malicious programs come equipped with features such as Live Chat options to ensure that victims know how to submit a payment, thereby affirming the end-goal of their criminal scheme.
Don’t give them the satisfaction.
Rolling-out software patches on a regular basis, refraining from clicking on suspicious links, and maintaining an anti-virus solution on your computer will go a long way towards preventing a ransomware infection.
Also, should ransomware ever execute on your computer, make sure you have several data back-ups on hand that you can load up once an expert has wiped the malware off of your computer.


All the fuckers should be locked up for 20-30 years
More will take their place. More techniques will be created and additional types of malware (and other exploits) will crop up. It's unfortunate but this isn't restricted to computer security; laws might deter some people but not everyone – and more will take the risk.
Yet they're really only profiting off of human stupidity and laziness. I don't condone this but it's actually quite smart (even though unethical, immoral etc.). People really need to take more care with their own data, assets and ultimately take responsibility for themselves.
'The use of a double extension is a deliberate attempt by attackers to fool users into believing that the file might be a legitimate PDF file'
When Microsoft initially implemented this years ago I was horribly dismayed. It was always a stupid idea and I seriously doubt (but I also can't prove otherwise off hand) this is the first time it's been abused. This won't be the last time. (Whenever I set up a Windows computer for someone I disable this feature and explain it to the person.)
'But this feature is misleading.'
Actually my initial thought was that it indeed is only removing the malicious code so as to deceive (people and/or software); obviously they wouldn't restore the data as that's the point of these campaigns.