
Before you ask the question in your head, let us answer it for you. Yes, you definitely need multi-factor authentication for your Office 365 account.
The sad truth of the matter is that today’s cybercriminals are getting more persistent, crafty, and just too good at what they do. They have adjusted their hacks from trying to directly access your device or system using phishing attacks, Trojans or direct hacks, onto something subtler.
These days the plethora of apps that we use (both mobile and desktop) means that we open ourselves to a greater risk of attack. After all, in the olden days (circa 15 years ago) we only had to worry about one to two points of intrusion. Now we have multiple sources of intrusion due to the number of connected devices we own and the apps installed upon them.
Take Office 365 for example, which is now available on desktops, tablets, and smartphones.
Thanks to a recent Office 365 update you can seamlessly share content, data and information between these devices as well as anyone else you deem necessary (using Outlook), and it can all be done in real time. This makes it really convenient when you are trying to meet deadlines, or working on a project with your team or sharing media with your significant other.
Cybercriminals also find it convenient and irresistible as they can essentially access all of your files and then spread out to your network. The tool to combat this threat is nothing new and you already probably know about it.
Microsoft’s built-in multi-factor authentication security system, named Azure Multi-Factor Auth, requires a user to not just enter their password, but also pass a verification process through one of several options:
- Phone Call – a security rep or automated voice message will call their phone to authenticate they are who they say they are using a series of questions and command prompts
- Text Message – will essentially do the same as the phone call but in text form only
- Mobile App Notification – installing the Authenticator app (aptly named Azure Authenticator) from the various mobile app marketplaces to receive command prompts from Azure MFA
- Mobile App Verification Code – enter a code through the mobile app
- 3rd party OATH tokens – if you’ve ever had to carry around an RSA token which can remotely generate an access code, this is basically the same thing
So, is the hassle worth it? That all depends on how much data you have on your device or within your email mailbox that needs protection? If you have a cloned or “throwaway” laptop (or device) that is basically used for work as a dumb terminal or basic leisure browsing and contains very little data on it, has very limited access to your network or Office 365 environment and mailboxes, then it may not be necessary to build a multi-layer fortress around your Office 365 platform.
However, if you are like the majority of users who use their mobile devices essentially as their primary communication and productivity tool, that do have significant access to network and Office 365 resources, then most likely you are keeping a significant amount of your personal and work information on your devices, network and in the cloud on Microsoft’s Office 365 data centres.
Here are some key questions that can help you decide on enabling Office 365 MFA:
- Do you email important, confidential and highly sensitive documents and files to clients, contacts and suppliers?
- Do you email important, confidential and highly sensitive data, passwords and files from your Office 365 email account to either a personal email, another work email or even back to your Office 365 email address?
- Do you do this to remind yourself to get that work done or to enable you to work outside of the office?
- Do you do this as your own personal work filing system, like so many of us do?
The answer whether to setup Office 365 multi-factor authentication or not is now hopefully obvious.
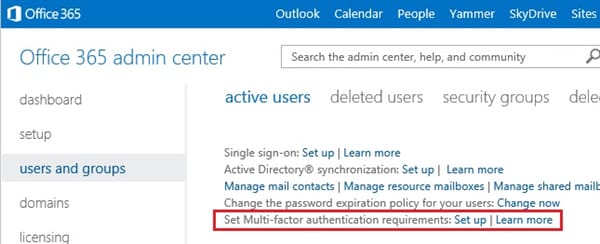
The next time you login to your Office 365 account, if you’re an administrator, click on the “Set up” or “Learn More” links next to the “Set Multi-factor authentication requirements” in the Active Users list, or contact your IT administrator to get them to look into it for you.
Note that Microsoft has started rolling out a new look portal for Office 365 admins in recent weeks.
If you have the new version, you will see a screen like this:

If you are still using the classic version of the admin center, it will look more like this:
More details of enabling multi-factor authentication for your Office 365 users can be found here.
In my opinion, it’s well worth enabling.
Read more about enabling two-factor authentication and two-step verification on different services
- Two-factor authentication (2FA) versus two-step verification (2SV)
- How to better protect your Facebook account from hackers
- How to better protect your Twitter account from hackers
- How to enable two-step verification (2SV) on your WhatsApp Account
- How to protect your Amazon account with two-step verification (2SV)
- How to better protect your Google account with two-step Verification (2SV)
- How to protect your Dropbox account with two-step verification (2SV)
- How to protect your Office 365 users with multi-factor authentication
- How to protect your Microsoft account with two-step verification (2SV)
- How to better protect your Tumblr account from hackers with 2SV
- How to protect your LinkedIn account from hackers with two-step verification (2SV)
- How to protect your PayPal account with two-step verification (2SV)
- How to protect your Yahoo account with two-step verification (2SV)
- How to protect your Apple ID account against hackers
- How to better protect your Google account with two-step verification and Google Authenticator
- How to protect your Hootsuite account from hackers
- How to better protect your Instagram account with two-step verification (2SV)
- Instagram finally supports third-party 2FA apps for greater account security
- How to protect your Nintendo account from hackers with two-step verification (2SV)
- How to better protect your Roblox account from hackers with two-step verification (2SV)



If somebody is doing any of the things you've suggested then you're doing it wrong and MFA won't help you.
You should never be sending "confidential and highly sensitive documents" or "highly sensitive data, passwords and files" via un-encrypted email. Period.
People who need to do exchange such information already have secure methods available to them and email isn't one of them.
Recommend MFA for extra account security, yes.
Recommend MFA to keep confidential or highly sensitive information safe, no.
'Recommend MFA to keep confidential or highly sensitive information safe, no.'
I get your meaning from context (re don't send documents over unsafe mediums) but in my view (and maybe it's just me) you're (potentially?) simplifying it a bit too much; it's true you shouldn't send confidential data over traditional email but having additional account security in general has the potential to keep data safer (as long as you aren't sending it unsafely as you say but it still might be safer at other times). In the end there is no such thing as 100% secure so all parts help. I know you know this but I'm pointing it out for people who might misinterpret your meaning (and I know very well that more people misinterpret my meanings much more often but all comments can be misinterpreted at some point by some people). Just a FWIW.
'If you have a cloned or "throwaway" laptop (or device) that is basically used for work as a dumb terminal or basic leisure browsing and contains very little data on it, has very limited access to your network or Office 365 environment and mailboxes, then it may not be necessary to build a multi-layer fortress around your Office 365 platform.'
I'll not get into the accuracy of the 'dumb terminal' analogy other than reference it. But I do want to say that the above quote seems to me to somehow discourage layered defences. I would say it's not even a matter of necessity so much as it should be done; sometimes no protection is 'needed' but that can change and then what will you do? It's not need and it's not want but instead how something should be done. Should very often isn't reality but maybe when talking about additional layers it should be only encouraged (if it's being discussed). It's also very well worth remembering that if you're less careful one place you're more likely to be less careful another place (see also rebooting the wrong system when working on multiple systems as a similar mistake of many more).
I don't know anything about Office 365 so I can't comment on it specifically.
Office 365 is Microsoft's enterprise suite. It can include (you choose what you need):
Desktop Office suite of applications (Word, Excel etc.)
Online Office as well (Google Docs equivalent)
OneDrive
VOIP calling
PSTN calling
Exchange Mailboxes (for domain names)
Email encryption
hybrid solutions (on-premises and hosted)
spam defence and zero-day protection
anti-virus and malware protection
SharePoint
Calendaring
CRM
DLP
(Those are only a handful of the features. I think they have a Microsoft Certified Office Professional. Even that will only cover one area of Office 365 it's that big.)
They started off by primarily offering a subscription to Office (i.e. per monthly billing, always updated). Then they moved towards integrating all their other offerings hence the '365' moniker.
Granted – it IS a very powerful solution and far ahead of Google at the minute. It's used primarily by large businesses (whereas Google Apps for Work targets smaller companies).
Their MFA is different to traditional 2SV solutions in that MFA requires the user to press a 'verify' button in the app on their trusted device to confirm they wish to login. This is crucial if the organisation integrates Office 365 with Active Directory as whole systems could be compromised without it.
I agree with you about account security but I meet far too many people who believe that email IS secure. Secure zero-knowledge encrypted cloud services are in my opinion the way forward. You can set temporal links that expire after X downloads and/or Y days and (optionally) need a password to download.
Office 365 (as do Google) offer the ability to set-up trusted partners with whom emails will only be sent over TLS but because of flaws in the TLS standard even this isn't a guarantee of security. Only true end-to-end encryption will make email secure.
Office 365 are moving towards customer-controlled HSM's (Thales) to prevent even Microsoft from getting at the data but this comes with some usability issues.
I agree with you about his 'dumb terminal' analogy. Security should be encouraged. Anything that can access your Office 365 infrastructure is a potential threat. You can access webmail for example via Microsoft's hosted portal and without MFA you're leaving your email at risk. You'd also have to rely upon the system administrator having correctly configured access levels (e.g. administrator, user, manager etc.) For remote workers sysadmins might want to allow access to the corporate/user OneDrive… another potential leakage if MFA isn't enabled.