 Normally you can only post on someone else’s Facebook wall if you are “friends”. That’s the way that Facebook designed it.
Normally you can only post on someone else’s Facebook wall if you are “friends”. That’s the way that Facebook designed it.
But Palestinian researcher Khalil Shreateh found a security vulnerability on the social network that meant he could post messages and photographs to *any* of Facebook’s 1,000,000,000+ users’ walls – something which in the wrong hands could be a very effective way of spreading malware, scams or spammy links.
But when Shreateh felt Facebook’s Security team weren’t taking him seriously, he “escalated” the problem in the most dramatic way possible. He posted a message on Facebook CEO Mark Zuckerberg’s own page.
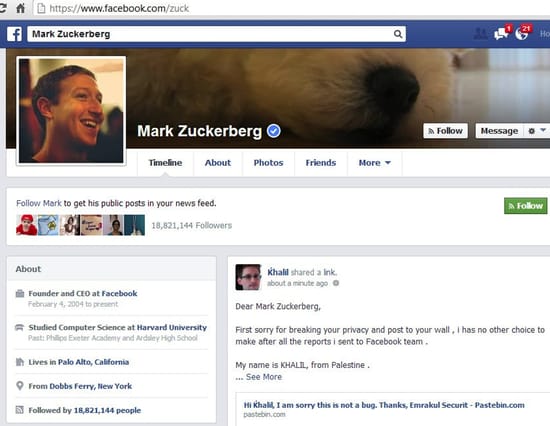
Dear Mark Zuckerberg,
First sorry for breaking your privacy and post to your wall, i has no other choice to make after all the reports i sent to Facebook team.
My name is KHALIL, from Palestine.
couple days ago i discovered a serious Facebook exploit that allow users to post to other Facebook users timeline while they are not in friend list.
i report that exploit twice, first time i got a replay that my link has an error while opening, other replay i got was “sorry this is not a bug”. both reports i sent from www.facebook.com/whitehat, and as you see iam not in your friend list and yet i can post to your timeline.
You can imagine how quickly that got Facebook’s attention. Sure enough, the post was removed and Shreateh’s account was suspended while the social network investigated the flaw.
Shreateh also made a YouTube video, demonstrating how he was able to use the exploit he discovered post on strangers’ Facebook walls.
http://www.youtube.com/watch?v=F9J8U9ZpEnw&rel=0
I have to admit that I have some sympathy with Facebook on this issue. Although he was frustrated by the response from Facebook’s security team, Shreateh did the wrong thing by using the flaw to post a message on Mark Zuckerberg’s wall.
Instead, he might have been wiser to go back (again) to Facebook’s Security team with more evidence of the flaw, explaining the problem more clearly and perhaps including more information as to its impact. If he was still not happy with their response, a technology journalist should perhaps have been his next port of call.
Because of what Facebook considers Shreateh’s irresponsible behaviour, the social network has said he does not qualify for a bug bounty reward.
If you are on Facebook, and want to be kept updated with news about security and privacy risks, and tips on how to protect yourself online, join the Graham Cluley Security News Facebook page.
Further reading: Facebook admits mistakes, but still won’t pay out to researcher who hacked Zuckerberg’s page



I have to disagree with you Graham. If Facebook claimed that the technical details of the flaw were amiss they should have taken the extra time to respond to him fast and promptly. It's great that Facebook gets more negative media attention in regards to privacy, they may actually wake up.
I agree with Jeremy. Getting through the red tape of not caring at most big online companies is almost impossible at times, a company I work for has been trying for MONTHS to get assistance from Facebook and they PAY for advertising all the time. A public slap in the face is sometimes the best way to get the big wheels turning in the right direction.
I would advise extreme caution before doing anything which might be construed as a hack.
Remember the case of Glenn Mangham? He was the "ethical hacker" who bypassed Facebook security and ended-up in jail:
http://nakedsecurity.sophos.com/2012/02/20/jail-facebook-ethical-hacker/
You sympathize with Facebook? He saved them potentially millions of dollars with this and they won't even give him any money. After two attempts of contacting FB, he viewed it as futile. Hats off to him; black hats on for you Graham.
I said I had "some" sympathy for Facebook.
I can understand the researcher's irritation about Facebook's lack of comprehension at the exploit he was trying to report – but that doesn't excuse how he did eventually grab the company's attention.
BTW, it's not just the way he disclosed the vuln that caused him to miss out on his bounty. It seems he was also not using one of the "whitehat researcher" accounts that Facebook offers folks who are looking for flaws in the social network.
I think … bypassing security is 'cracking'.
'Hacking' is what we do, to keep MS Windows running …
or, at least, to keep it running the way we like it.
Good article, other than the terminology.
I'm another who agrees with Jeremy. The man did not post anything "irresponsible," though he could have. He proved his case, period, something "the team," should have welcomed. They also could have avoided it, but pride and arrogance are never very attractive, and refusing to honor their contract with the world is one more evidence of those traits.
Yes, Facebook's security team could have handled this better. No doubt about that. They dropped the ball.
But I don't agree that that excuses what Shreateh did next. I think it would have been better if he had tried again with Facebook Security or, failing that, found a responsible journalist to demonstrate the flaw to who could have embarrassed Facebook into action.
Shreateh is a saint…anyone else would have gone to the otherside and sold this exploit for money…all this story shows us is that the big corporate company does not care unless the it starts to suffer. For Facebook not to even offer the bounty that just goes to show everyone else not to bother with doing the right thing and try to get compensated the wrong way.
Facebook's White Hat program has rules and guidelines which it asks vulnerability researchers to abide by. Why should Shreateh be allowed to breach them?
For instance, Facebook provides researchers with test accounts to explore possible security problems. I know this because they gave me some for my own research purposes.
These accounts give researchers a "safe playground" to experiment and try out things. Shreateh on the other hand, posted an Enrique Iglesias video onto the timeline of Sarah Goodin (who, incidentally, was a Harvard college friend of Zuckerberg).
*If* Facebook did award the bounty, might that not open the doors for others to abuse innocent users of Facebook with their experiments and tests of exploits?
It's unfortunate that Facebook goofed up – and didn't understand what Shreateh was trying to tell them. But that doesn't make Shreateh a saint.
The nationality of Shreateh was the real issue.
Facebook owes Shreateh big time. He could have used the flaw without saying a word.
I definitely disagree with you, in fact I would have done much worse and to add insult to injury the FB team in disgrace suspended his account. Silly tactics for monkey actions. They got caught with their pants down and they showed bullying tactics.
If Facebook discovers that an account is posting messages to other users' walls without their permission isn't the /only/ safe course of action for FB to (temporarily, while it investigates) suspend the offending account?
I agree that Facebook handed this badly. But seems to me they were stuck between a rock and a hard place, and are doing their best to make it clearer to researchers what they require in a vulnerability report in future.
Who cares. No harm, no foul. Obviously Shreateh could have done much more damage, but he responsibly didn’t….As long as facebook resolves the flaw….that’s all that matters…
"But I don't agree that that excuses what Shreateh did next. I think it would have been better if he had tried again with Facebook Security or, failing that, found a responsible journalist to demonstrate the flaw to who could have embarrassed Facebook into action."
Maybe, but figuring out how to push the right combination of bureaucratic and/or political buttons can be a huge challenge for anyone, much less a person in his position.
I've had a number of security researchers contact me in the past, asking me to act as a go-between if – for whatever reason – they want assistance contacting Facebook's security team.
I'm always happy to help if I can. Similarly, if Shreateh felt he had found a serious flaw I'm sure the likes of The Verge, The Next Web, The Register, and a hundred other publications would have been happy to publicise it and managed to get Facebook's attention without him having to break the site's security and post to innocent users' timelines.
Cluley is clueless and a Facebook shill at that.
I've been called many things, but never imagined I would be described as a shill for Facebook…
You *have* seen what I’ve had to say about Facebook in the past, haven’t you?
Graham,
You are dead wrong and need to just own that, in this instance.
Stop being a pedantic head-of-knuckle. You know that progress in the security sector does not work the way you are suggesting (just keep knocking politely on door until answered….tripe).
He tried to get a receptive ear, what he got instead was bureaucracy and red-tape.
From an organization that is supposed to be forward thinking and responsive to input.
I have some years on you in forensics and security, and even I would be frustrated by such an 'ivory tower' mentality as FBs security displayed in this matter.
You come off sounding somewhat as a shill for FB because you are defending their indefensible stance and choice. So people are calling you on it. As am I.
MZ needs to instruct FB workers in the security team to:
1. Pay this young man what is owed, rightfully.
2. Thank this young man for his efforts.
3. Have the security team trained in proper process and protocol in accepting candidate flaws for analysis and reporting.
I didn't say that security researchers have to "keep knocking politely on the door until answered"
In fact, I've said that if a researcher is frustrated that Facebook isn't listening, they should take details of their discovery to a friendly journalist who can report the issue responsibly and will *definitely* get the attention of the team at Facebook.
Having said that, Facebook did screw up in this instance. It's just that I don't believe that their screw-up excuses what Shreateh did next.
Shame on Facebook. They should thank this man for being honest. Mr Zuckerberg should thank him in person and offer him a Job. Graham you are dead wrong.
Shreateh said the following in an email to Facebook Security:
"I can post to mark wall either but i will not cause i do respect people privacy.." (sic)
And then he *did* post to Mark Zuckerberg's wall. So, what happened to respecting people's privacy?
Yes. It's good that Shreateh found the bug, and informed Facebook rather than sell details onto bad guys.
Yes. Facebook messed up its handling of Shreateh's initial reports of the vulnerability.
No. That doesn't excuse him posting messages on the walls of users (Sarah Goodin and Mark Zuckerberg)
Totally disagree with you. You are an example of bullcrap red tape. This guy went straight to the source when needing escalation. Good for him. Time saved for many people and for good service. Disgusted that facebook didn't pay him and used the terms of service as a reason. Shows they're now a typical corporation. If they suspended his account too then that's sad. This is how you turn good intentions into bad ones. The guy could've easily done harm with this knowledge but chose not to. Shame on facebook. And graham this is the first and last time I read your info. Saw you quoted on CNN so checked it out and I am astonished at your proposed handling of this. What crap advice.
Seriously???? HAHa come on now.
….a technology journalist should perhaps have been his next port of call.
Why should he have called a security journalist? Who's to say that he would even receive credit for what he found?