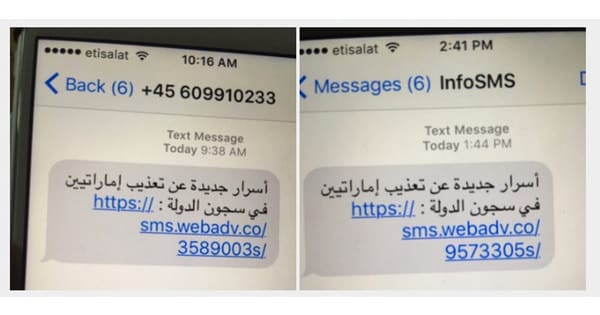
Remember the critical security holes that Apple patched in iOS last week after a human rights activist had his iPhone targeted in a seemingly state-sponsored attack?
Ahmed Mansoor received two suspicious SMS messages on his iPhone, directing him to websites containing a zero-day iOS exploit. Researchers connected the attack to Israeli-based firm NSO Group, and dubbed the vulnerabilities “Trident”.
Well, Apple has now quietly rolled-out a further security update revealing that the zero-day flaws are also present in Apple’s OS X desktop operating system, as well as the desktop version of their OS X Safari browser.
My advice to Apple users? Make sure that your Macs, MacBooks, iPhones and iPads are up-to-date.
On OS X the easiest way to update your computer is to open the App Store app on your Mac, then click Updates in the toolbar. If updates are available, click the Update buttons to download and install them.
On iOS go to Settings > General > Software Update.
You may not be a human rights activist, but the fact that it took Apple *days* to issue a fix for OS X users after patching the same vulnerabilities in iOS has opened an opportunity for others to potentially exploit them against desktop users.
In an ideal world, Apple would have patched its mobile and desktop operating systems at the same time.
What we don’t know is whether Apple didn’t know the vulnerability was also present in OS X when it issued the iOS fixes, or whether it made the difficult decision to urgently update iOS even though its equivalent OS X fixes weren’t yet ready.