 A security researcher has developed a phishing attack that tricks users of the online password manager LastPass into forfeiting their email addresses, master passwords, and even two-factor authentication (2FA) codes.
A security researcher has developed a phishing attack that tricks users of the online password manager LastPass into forfeiting their email addresses, master passwords, and even two-factor authentication (2FA) codes.
Sean Cassidy, CTO of Praesidio Inc., recently presented on his so-called “LostPass” phishing attack, the code of which is available via GitHub, at the ShmooCon 2016 conference. The researcher has also provided a complete overview of the attack in a blog post on his website.
Cassidy’s research dates back to a few months ago, when the researcher first noticed that the password manager displays a session time-out notification via what is called a browser viewpoint, as shown below:

After noticing that both the login and 2FA prompts also appear in separate browser viewpoints, Cassidy formulated an attack by which he could phish for users’ credentials by steering victims to either a malicious website or a legitimate website that is vulnerable to cross-site scripting (XSS).
“Unlike most phishing attacks, users won’t be on their guard because this isn’t supposed to be a secure website. It could be a funny video or image, even.”
If the victim has LastPass installed, the attacker can exploit a cross-site request forgery (CSRF) request in the password manager to log the user out of their account and show the expired session notification. This viewpoint comes with a link to an attacker-controlled login page, where the user is asked to enter in their username and password.
If they have 2FA enabled on their account, they are then directed to a fake verification code prompt, as shown here:
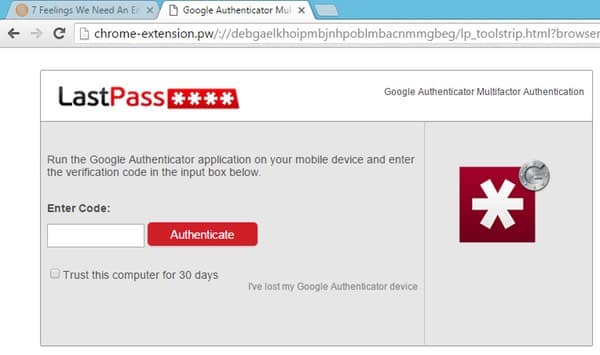
“Once the attacker has the correct username and password (and two-factor token), download all of the victim’s information from the LastPass API. We can install a backdoor in their account via the emergency contact feature, disable two-factor authentication, add the attacker’s server as a ‘trusted device’. Anything we want, really.”
Cassidy reported to LastPass the attack, which has been shown to work for the Chrome and Firefox browsers, back in November of last year.
As Fast Company reports, LastPass has confirmed this fact:
“We did work directly with Sean Cassidy, and can confirm this is a phishing attack, not a vulnerability in LastPass. However, we’ve released an update that will prevent a user from being logged out by the phishing tool, thereby mitigating the risk of the phishing attack.”
This update (available here) includes the announcement that all users, including those who have 2FA enabled, will from now on need to verify their accounts whenever they log in from an unknown device or location.
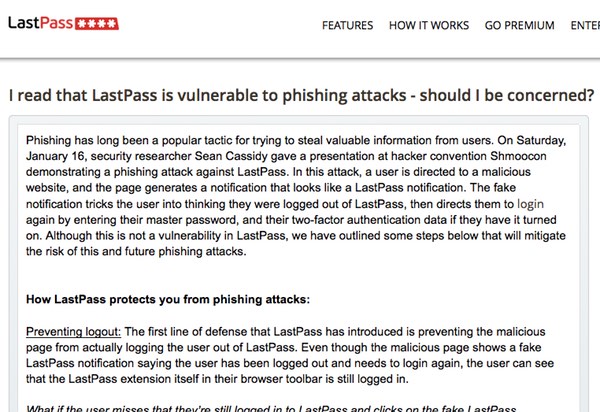
Cassidy agrees that LastPass’s update has helped mitigate the risk, but he is careful to point out that the attack has not been eliminated.
Ultimately, Cassidy feels that the LostPass threat persists in part because of poor handling of phishing attacks, a tendency which marks the security industry more generally:
“We as an industry do not respond to phishing attacks well. I do not blame LastPass for this, they are like everyone else. We need to take a long look at phishing and figure out what to do about it. In my view, it’s just as bad, if not worse than, many remote code execution vulnerabilities, and should be treated as such.”
Citing “the public has the right to know” as the reasoning behind publishing his findings, the researcher recommends that companies pentest themselves against this tool to determine whether they are vulnerable.
Individual users of LastPass should avoid logging in from a browser viewpoint and should instead always log in from the native application. This will help to avoid most web-based LastPass phishing attacks.



How about third-party phishing attacks? As in, "we have been retained by [legitimate company] to survey you on your experiences with [legitmate company] (or to bill you on behalf of [legitmate company])".
This seems to be how some LegitCos. actually do business. It would seem rather trivial to fake.
By the way, I think it's mean to be "browser viewport" not "browser viewpoint".