Hackers have attacked LastPass, the popular online password management service, and stolen data.
In a blog post the company went public with limited details of the security incident:
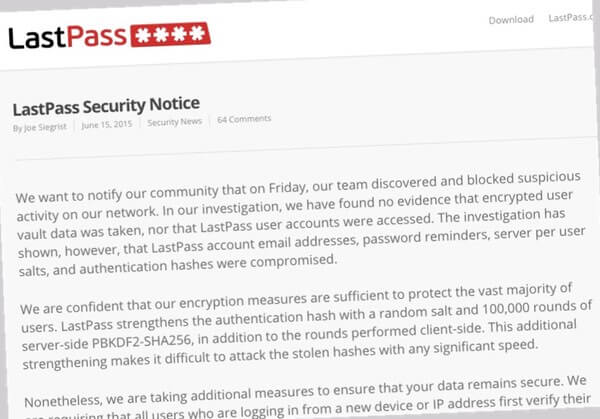
We want to notify our community that on Friday, our team discovered and blocked suspicious activity on our network. In our investigation, we have found no evidence that encrypted user vault data was taken, nor that LastPass user accounts were accessed. The investigation has shown, however, that LastPass account email addresses, password reminders, server per user salts, and authentication hashes were compromised.
We are confident that our encryption measures are sufficient to protect the vast majority of users. LastPass strengthens the authentication hash with a random salt and 100,000 rounds of server-side PBKDF2-SHA256, in addition to the rounds performed client-side. This additional strengthening makes it difficult to attack the stolen hashes with any significant speed.
It’s important to understand that the hackers have not stolen LastPass users’ master passwords. Instead, they have managed to get their hands on the authentication hashes (or checksums) used by LastPass to verify your master password is correct when you try to access the service.
If you chose a weak master password, or if it isn’t very long, then it might be possible for an attacker to crack it through brute force.
 LastPass says that because the hackers do not appear to have accessed password vaults (which users store in encrypted form on the company’s servers) there should be no need to change passwords on other online sites. Which is obviously a huge relief.
LastPass says that because the hackers do not appear to have accessed password vaults (which users store in encrypted form on the company’s servers) there should be no need to change passwords on other online sites. Which is obviously a huge relief.
However, it is advising users to immediately change their master password if it is weak or if the same password has been used on other websites. (If you are reusing passwords then you need to get out of that bad habit at once, of course).
Unfortunately, right now LastPass appears to be overloaded with folks trying to reset their master passwords. If it doesn’t work for you, try again in a little while.
Furthermore, if you are not already doing so you really should enable multi-factor authentication on your LastPass account.
As a further precaution, LastPass says it is requiring that all users logging in from a new device or IP address to first verify their account by email, unless multi-factor authentication is enabled. As a further precaution, users will also be prompted to update their master password.
The company says it will be emailing users to advise them about the security incident.
Do be careful if you receive an email from LastPass, of course. Amongst the stolen information appears to have been a database of account email addresses – an opportunity for phishers and identity thieves to commit email-based attacks posing as the password management company.
As always, don’t panic. The sky is not falling. Take sensible steps to better secure your account – LastPass’s advice is good.
Hopefully, in due course, they will be ready to share more information about precisely what happened and reassure customers that it won’t happen again.
Of course, hacks against LastPass *have* happened before. In 2011, I was impressed with how LastPass responded when it noticed that hackers had managed to access data on its servers.



Password Managers – the digital way to put all your eggs in one basket!
(also line 1, *maangement -a)
Sorry, but I just don't buy that argument.
YES – all eggs are in one basket, but in the end, provided that one takes really good care about a strong master password, anti-malware/keylogging solutions, avoiding ANY open Wifi unless through a proper VPN-connection… then (and only then) the odds are definitely in favour of using a password manager.
I am VERY HAPPY to confirm that I do not know ANY of my at-least-100-characters-long-passwords anymore :)
PS: not all website/services will allow a 100-character long password. Some will not even go beyond 12 or 16 characters, even exclusive of special characters. Go figure how seriously those websites would take security in general :) Being able to weed out those websites, also serves as a red flag / way to avoid those possibly-first-to-be-hacked-sites IMHO.
>I am VERY HAPPY to confirm that I do not know ANY of my at-least-100-characters-long-passwords anymore :)
You have a single point of failure that would leave you utterly stranded if it ever did fail. You've put all your faith into a single system, one which you probably have little understanding about the inner workings of.
I'm glad that this system has made you feel safer and I hope it does continue to work for you, let's hope that basket never gets corrupted/erased or a flaw in the source code discovered etc.. etc…
Out of interest, which password manager do you use?
Using Keepass you get to keep the data in your own encrypted file which you store any way you want eg. in a restricted or encrypted folder on your hard drive, on a USB stick hidden at home etc. although I personally keep it on my hard drive with a copy on my Google drive for back-up. My pass phrase is over 20 characters long which is too much trouble for an attacker to break by brute force.
Trying to make up and remember unique passwords for 100+ websites is far more risky.
I use a similar tool – Sticky Password – they offer also offline approach which I prefer so I don't care if they're hacked or not, I'm safe since all my passwords are on my PC. Yes, I don't sync to mobile, I don't need it.
@Roboform Everywhere users — have you all noticed, that there is an additional "one time password" setting in your account settings? Please make sure to activate this. Although it is just a ONE TIME 2-factor-identification, it serves, to some degree, to prevent unauthorized access to your account.
Here's a quick screendump, where to look:
http://postimg.org/image/8x6i8nuxr/
(sure, going to that link is safe)
I know – it would be still better for Roboform to provide real 2FA instead, as one's email might get "pulled" anyway.
Maybe this is a naive question, but when the problem is LastPass not securing our data from invaders, why is the answer to impose additional operational burdens on the users (2-factor, authentication, email verification, whatever) rather than vendor fixing their security?
Basically, if you have 2 factor authentication enabled then even if your master password is stolen/calculated from the hash, there is still a barrier between the invader and your password vault.
I'm sorry but we don't know that at all. If they've managed to compromise the login list they may very well have access to the password database so they can use it for an OFFLINE attack. That would make any additional security redundant.
Or if they don't have access to the offline database they may have enough information (likely from the news reports) to generate the verification PIN themselves and then they can login online.
It's not actually 2FA with LastPass, it's 2SV. The difference is the latter is easier to crack (i.e. both 'steps' (not factors)) are done by the keyboard – unless you have a hardware factor. But even so with an offline attack both 2 factor and 2 step won't protect you.
That's a very good point – I wasn't aware that it was 2SV on offer, the article states "multi-factor authentication".
I maintain that there is still a barrier though if your master password has been identified, although not an unsurmountable one:
According to LastPass the Password vaults were not accessed (or at least there is no evidence that they were), so the value of an offline database is surely only the ability to (possibly) decipher passwords. You can add into the mix the ability to (possibly) decipher 2nd stage verification. It's been proven time and time again that the low hanging fruit is likely to be grabbed so IF any passwords are deciphered and accounts compromised then these would likelt be accounts with simple passwords and no 2SV enabled.
You can check out the different authentication options LastPass can offer here: https://helpdesk.lastpass.com/multifactor-authentication-options/
I know security professionals who use LastPass in combination with a Yubico USB wotsit, for instance
I've looked at all your points Stuart, Graham and Bob.
Yubico is an example of 2FV but the way that it's implemented makes it de facto 2SV as the other poster Bob has pointed out. Unless LastPass elect to use the Yubikey as it was designed to be used the security problems still exist and bypassing it is trivial.
Naturally decrypting the passwords is the bigger problem as their key derivation functions means it is only possible to search a minimum of 10,000 passwords per second. An array of password crackers would obviously expedite the process considerably but that's a lot of work unless the individual is a high-value target.
It doesn't bode well for insecure master passwords or if hackers find that the function isn't being used properly.
You need to do both. The threats are evolving, so the defences need to as well. To give a real-world parallel – If there's increased burglaries in an area, the police may do more patrols, etc., but it's only sensible to increase the security on the houses too.
I've got to recommend KeePass Professional Edition (it's free!) as YOU control your data. You can also choose how many times your master password is iterated to make brute force more difficult. Other applications exist including 'Password Safe' by the famous cryptographer Bruce Schneier.
You can store your database locally or back it up onto a USB drive. There's nothing to stop you uploading it to the cloud although this would weaken your security negligibly (the database is still encrypted).
The problem with online password managers like LastPass and RoboForm is that they're a massive target to hackers. These sites will come under relentless attack as they're a central repository of highly confidential data.
Hackers are far less likely to target your personal cloud account (where you upload a KeePass backup) as they'd need to guess your cloud password and, if activated, bypass two-step verification. Then they'd need to crack the encryption on your database – highly improbable if secured correctly.
The only downside to local storage of passwords is you can't access it from another computer, unless you carry a copy around with you. But you shouldn't be doing this as their could be Trojans / Malware / Keyloggers installed. The same applies to online password storage – a 'foreign' computer could be capturing the data. So my argument stands, only use a trusted computer – which to me makes online password managers redundant.
What concerns me is that information like 'reminders' were also stolen from LastPass. If they haven't stored this correctly on their servers then, even if you change your password, your account can be breached if the reminders get cracked. So you'll have to change your password reminders too.
Stick to the tried and tested methods – offline storage of passwords. You can still interact with websites by using autofill but you don't need to worry about somebody else's security failing.
Autofill has its own failings and I really don't think you should be recommending it…
Consider this:
Connect to coffee shop wireless, open browser – redirected to a login page for Internet access.
Login for internet, connect to VPN – go about your broswing.
This seems fairly secure (as secure as it can be on login portal based WiFi), but you have no control over that login page – it could have multiple hidden iframes that load the login page to various popular services such as mail, social networking etc. and autofill just gave the page all your passwords in a matter of seconds.
Bobby, by autofill I was not referring to browser functionality rather KeePass functionality.
Once you're at the site you want to be you then double click on the username/password and 'paste' it into the field. This is what KeePass refer to as 'autofill'.
Or you can right click and allow it to 'autofill' and it will do the copy and paste for you, using obfuscation if you set it up.
What it doesn't do is reside in the browser and 'autofill' whenever it sees a password prompt. I can see where the confusion arose.
LastPass is the best of the best. I did change my Master Password, but I also have Yubikey 2-factor authentication enabled, so I'm not particularly concerned about this event. Even if someone got my password, they would have have to have the Yubikey to authenticate to the server.
I covered this above; having a Yubikey will NOT protect you from this hack as LastPass themselves admitted:
"The investigation has shown, however, that LastPass account email addresses, password reminders, server per user salts, and authentication hashes were compromised."
Therefore the hackers could "authenticate to the server" using the information stolen.
Don't get me wrong, I am in favour of multi-factor authentication because it makes hacking more difficult but it is not a magic bullet.
I have found Lastpass very useful for keeping track of many passwords (subscriptions, websites etc), but i've never entrusted it with access to my money.
I can remember (or write down in obfuscated form) my handful of banking and stockbroking passwords, and even there I use 2-factor verification if available (I really like the ones that send a 6-digit short-lived verification code to your mobile phone).
So the LastPass security breach has been for me an annoyance (had to change my master password – now a few characters longer :-) but not a cause for panic.
ID federations (single-sign-on services and password managers) create a single point of failure, not unlike putting all the eggs in a basket. It remembers all my passwords when un-hacked and loses all my passwords to criminals when hacked. It should be operated in a decentralized formation or should be considered mainly for low-security accounts, not for high-security business which should desirably be protected by all different strong passwords unique to each account.
It is too obvious, anyway, that the conventional alphanumeric password alone can no longer suffice and we urgently need a successor to it, which should be found from among the broader family of the passwords and the likes.