
There are multiple reports from countries around the world that their computers have been hit by ransomware.
Part of the ransom message reads as follows, in red letters on a black background:
Ooops, your important files are encrypted.
If you see this text, then your files are no longer accessible, because they have been encrypted. Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.
We guarantee that you can recover all your files safely and easily. All you need to do is submit the payment and purchase the decryption key.

Security experts have confirmed that the ransomware, named by various anti-virus firms as NotPetya, Petrwap, or a variant of Petya, is spreading in part through the exploitation of an NSA-built Windows-based SMB exploit known as “Eternal Blue”.
 Eternal Blue was developed by the United States’ National Security Agency for the purpose of infecting the computers of those it wished to spy upon. As a consequence, the NSA didn’t tell Microsoft about the vulnerability it had discovered in Windows *until* details were stolen from the agency by a mysterious group of hackers known as the Shadow Brokers.
Eternal Blue was developed by the United States’ National Security Agency for the purpose of infecting the computers of those it wished to spy upon. As a consequence, the NSA didn’t tell Microsoft about the vulnerability it had discovered in Windows *until* details were stolen from the agency by a mysterious group of hackers known as the Shadow Brokers.
The fact that the NSA initially hoarded details of the security holes in Microsoft’s code has put organisations around the world at risk.
Eternal Blue was a key part of how the WannaCry ransomware spread so quickly earlier this year, and *has* now been patched by Microsoft for some months. Clearly, however, many organisations have still failed to put those security patches in place.
The malware attempts to gain administrator access on infected computers, scouring memory for domain admin credentials and looking for other systems to infect in the organisation.
Some of the earliest reports of affected computers came from government offices and energy companies in Ukraine, as well as the airport of the country’s capital Kiev where BBC News reports that flights may be delayed as a consequence.
Meanwhile, the media inevitably ran chilling headlines about the fact that the infamous Chernobyl nuclear power plant was counted amongst the victims of the ransomware attack, disrupting the site’s automatic radiation monitoring systems.

Some, however, didn’t seem too flustered.
For instance, Pavlo Rozenko, deputy prime minister of Ukraine, tweeted a photograph of his computer – seemingly mid-way through being encrypted by the ransomware.

His caption?
“Ta-daaa! Network is down at the Cabinet of Minister’s secretariat.”
However, it’s incorrect to think that the attack limited itself to Ukraine.
For instance, there have been additional reports that the Spanish offices of multinational companies such as law firm DLA Piper have been hit by a malware attack that is encrypting files on their computers and demanding a ransom of US $300 in Bitcoin be paid to the extortionists.
Meanwhile marketing giant WPP says that several of its companies have suffered as a result of a “suspected cyber attack”.

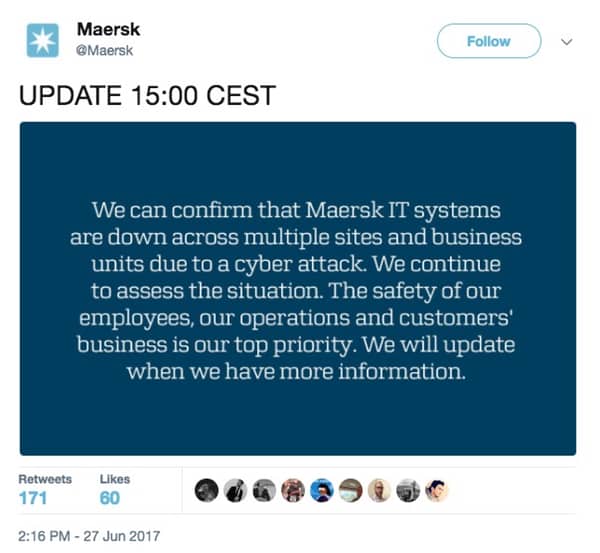
Other victims include Maersk, the international shipping logistics company, which confirmed via Twitter that it had fallen victim to a cyber attack.
There have also been reports of infections in Russia, India and the UK, and it seems unlikely that that will be the end of it.
I really hope you learnt a lesson from the WannaCry ransomware outbreak and put some secure backup systems in place…
Hey folks, just wanted to check on something…
You did do backups, right? pic.twitter.com/QeO3N7vtHN
— Graham Cluley 🇺🇦 (@gcluley) June 27, 2017
Finally, a big question you’re likely to have if you were unlucky enough to have fallen victim to this ransomware attack: should you pay the ransom?
The answer to that is unequivocally “no.” Even if you get past the ethical debate of paying money to extortionists, it’s worth bearing in mind that email service Posteo has blocked an email address being used by the criminals – meaning that you can no longer get in contact with them, and they can’t get back to you.
Whether that was a sensible action by Posteo is, of course, open to debate… One hopes that it was at least done after consulting with law enforcement agencies.
For more discussion of this topic be sure to listen to this episode of the “Smashing Security” podcast:
Smashing Security #031: 'Petya (don't know the name of this ransomware)'
Listen on Apple Podcasts | Spotify | Pocket Casts | Other... | RSS
More episodes...



"Well NSA, here's another nice mess you've gotten us into."
Why Why and why don't these companies have offline backups? I'm sure they have spare hard drives laying around, and for less than $20.00 you can buy a hard drive reader. Plug your spare hard drive into the reader Back your important data up to the spare hard drive, then unplug it. It's not rocket science just lazy IT people.
I really hope you learnt a lesson from the WannaCry ransomware outbreak and put some secure backup systems in place…
Should read
I really hope you learnt a lesson from the WannaCry ransomware outbreak and switched to a Mac.
I know you're trying to be funny, but let's not forget that Mac users need a secure backup strategy just as much as Windows users.
And, of course, there is ransomware for the Mac. Albeit not as much – by a long way – as there is for Windows. :)
I would love to see a article on this as well as how many users were effected, please.
Darn! The NSA is so addicted to this stuff that they just couldn't let go, could they?
"Eternal Blue" almost sounds like "Crystal Meth" to my ears :o)
What a mess…
7:09 A.M. EDT (UT – 4)
LOL at the crystal meth/eternal blue remark.
WIN 10 "Update Tuesday," didn't happen. I got the updates today. Maybe the ransomare caused MS. to hold off to double check?
It is a mess. Thanks to Cluley, at least we know people r hard at work going after the bad guys. Ditto for the folks at Malwarebytes.
Apparently, if you place a small file containing anything you like, into your c:\windows directory, and call it "perfc", if you get infected with this one, it will think it has already encrypted your files, so it won't mess your disk up. You'll still be infected and pass it on to others, but you won't get your hard disk clobbered. Link is https://www.bleepingcomputer.com/news/security/vaccine-not-killswitch-found-for-petya-notpetya-ransomware-outbreak/
Oh, well. you didn't want those files anyway, did ya ❄️. ????
https://thehackernews.com/2017/06/petya-ransomware-wiper-malware.html