 Welcome back. I hope you had fun over the Christmas/New Year/Winterval (delete as appropriate) break.
Welcome back. I hope you had fun over the Christmas/New Year/Winterval (delete as appropriate) break.
If you’re lucky, you’re not returning to a mountain of email that less considerate internet users and spammers sent you while you were neglecting your inbox.
But chances are that many of you, after a couple of weeks away from the office, will find yourselves desperately trying to recall a password to access a work-related service or account.
Wouldn’t life have been easier if all of your passwords were “Password1”? How much simpler would that have been?
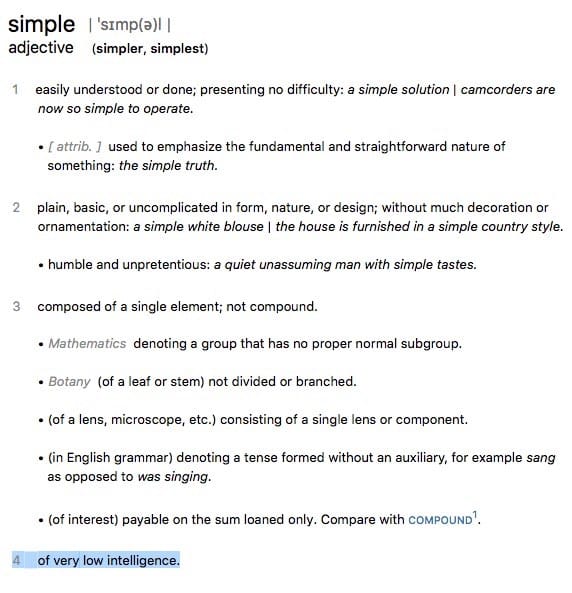
Well, simple is definitely the right word. But safe it most certainly would not be.
Make one of your 2016 security resolutions to get a proper handle on passwords. You should never reuse passwords, and your passwords should not be predictable or easy to crack.
In fact, in my opinion, if you can remember all of your passwords you’re doing things the wrong way.
If you find passwords a burden – simply use password management software like 1Password, LastPass, Dashlane, and KeePassX to make passwords safer and to do all the tricky remembering for you.
PS. Never mind about passwords, I once had a colleague who forgot how to turn on her computer after several weeks away. Hilarious… :)



Which password management software do you recommend, Graham?. Isn't one of the above no longer maintained?
Presently I'm using 1Password.
Which of the above password managers is no longer being maintained?
I think I'm confusing that with LastPass getting bought.
Ah, ok.
Yes, a fair number of LastPass users seem to be nervous about the firm being acquired by LogMeIn. I guess we'll have to see how that impacts the LasPass service (if at all)
For those who don't want to wait and find out, Troy Hunt has put together a guide to migrating to 1Password: http://www.troyhunt.com/2015/10/logmein-now-owns-lastpass-heres-how-to.html
Hi Graham,
I'm Eva and I work for AgileBits, the makers of 1Password.
I wanted to thank you for taking the time to educate your readers on the importance of online security and for recommending 1Password in your discussion!
In this day and age, it is so important that we all use strong and unique passwords for every site that we visit, and password managers can help make it much more convenient to be secure.
Keep sharing the secure word!
Eva Schweber
Good Witch of the Pacific Northwest @ AgileBits
support.1password.com
Chris,
I'd steer clear from LastPass simply because the consensus is that their new parent company (LogMeIn) have proven themselves to be untrustworthy. You can find evidence of this in news articles (see their previous acquisitions) and they are moving towards a more corporate based solution – think OneLogin.
Keepass is the best solution as it's 100% open source and has stood the test of time. It's available on a number of platforms. Did I mention it's also free?
Failing that then 1Password is your next best bet however bear in mind that their free Android version is somewhat limited unlike their free iOS version. Also if you use 1Password on a number of platforms they expect you to buy a licence PER PLATFORM! They also don't support Limux and are not open source.
RoboForm is fantastic password manager that I'd highly recommend. Their Everywhere software is extremeley secure and convenient, and it's free for up to 10 logins. After that it's only $9.95 and they routinely offer discounts. www.roboform.com
Problem with RoboForm is that they don't allow you to export your data. They've intentionally removed at feature to lock you into their product. Plus, it's a yearly subscription!
The issue I have with these password managers is that you have to trust them to keep your passwords safe. And there is a complex process when managing multiple devices. In the end it may be easier to keep an obfuscated paper record which is unhackable from the internet and not immediately identifiable when someone steals the paper and reads it.
Paper sounds fine until you find yourself trying to hand-type a randomly generated string of characters into a login box (anything insufficiently pseudo-random is subject to dictionary attack).
As for the trust issue the open-source products (like the KeePass derivatives) at least publish their code, which makes leakage much less likely. It's wise to cultivate a healthy level of paranoia when it comes to security software but you have have to practise spotting when you're going too far.
I see where you are coming from but I think your comment about dictionary attack isn't quite right. Any password based on words in a dictionary is subject to dictionary attack. If your password isn't dictionary-based then you are not subject to dictionary attack. If the password you pick is long enough, not-dictionary based and the servers storing it are properly using salting and hashing then there is no need for something unmemorable. The human brain can remember a lot of things. I remember nearly all the phone numbers I have had, are those pseudo-random? I guess maybe they are!
Ah. In that case you can forget about dictionary attacks but I'm afraid you're still vulnerable to a phone book attack.
You can have your password as "abc123" and yet be secure. If you lock the password to work only from your computer or device…
And how exactly do you do that?
Because IP address and MAC spoofing is very easy… as far as I'm aware there's no secure way to implement what you're suggesting.
Agreed.
A good password manager provides no third-party (SERVICE) dependence which is the case for LastPass or RoboForm. Furthermore, the intent of a password manager is to mitigate damage in the event that a service provider that you use is compromised. It does not guarantee that your accounts are secure. It provides YOU with the means to utilize strong / different passwords across all of your online accounts and in the event one provider is compromised, you don't fall victim to the "I use the same password or slight variation of the password across all of my accounts" scenario. You still have to protect your devices and you still need to use a really good, but memorable password to protect your vault.
I use 1password (This is not an endorsement), because of the security features and availability across all of my devices. Now, with that being said, I DID have to purchase a license per device, which sucked, but not the end of the world. I also opted to manually move my vault from device to device and not sync with DropBox (because then I would be relying on DropBox to not only protect my vault, but to also be available). Small hassle, but not by much. Just a few months ago there was a claim that the product leaked metadata (bogus), which was QUICKLY (as in same day) put to rest with explanation and an update shortly followed.
ID federations (single-sign-on services and password managers) create a single point of failure, not unlike putting all the eggs in a basket. It remembers all my passwords when un-hacked and loses all my passwords to criminals when hacked. It should be operated in a decentralized formation or should be considered mainly for low-security accounts, not for high-security business which should desirably be protected by all different strong passwords unique to each account.
Being able to create strong passwords is one thing. Being able to recall them is another. And, being able to recall the relations between the accounts and the corresponding passwords is yet another.
At the root of the password headache is the cognitive phenomena called “interference of memory”, by which we cannot firmly remember more than 5 text passwords on average. What worries us is not the password, but the textual password. The textual memory is only a small part of what we remember. We could think of making use of the larger part of our memory that is less subject to interference of memory. More attention could be paid to the efforts of expanding the password system to include images, particularly KNOWN images, as well as conventional texts.
James, that story about 1Password leaking metadata was NOT bogus… it was absolutely true and is relatively serious. 1Password down-played the serious nature of the vulnerability. They've not 'fixed' it because they don't consider it important enough. Your only hope is migrating to the new data format.
I've posted the link to the research at the end of this comment. 1Password actually designed their product like that (it dated back to when processors on mobile devices were less powerful). There are a number of reasons why that vulnerability was very serious including the fact 1Password would (and still will) leak what sites you're signed up to, links (which may be reset links etc.) You consciously have to use the new data format OR use a platform where the new format is on by default.
You can use Wifi Sync with 1Password which is probably the most secure but, providing you trust their encryption, then the database should be secure no matter where it's transferred over. However because they don't make all of their code open source you can't be certain that it's been implemented properly (or if it contains a backdoor, unlikely).
http://myers.io/2015/10/22/1password-leaks-your-data/