 Two security researchers have discovered a number of bugs, bad practices, and design issues in the popular LastPass password manager.
Two security researchers have discovered a number of bugs, bad practices, and design issues in the popular LastPass password manager.
Martin Vigo and Alberto Garcia Illera, both security engineers at Salesforce.com, recently presented their analysis of LastPass at Black Hat Europe 2015.
In a blog post describing their findings, Vigo and Garcia say that after conducting some preliminary research, the duo decided to see if they could attack LastPass’s password vault directly and obtain access to LastPass credentials via three different techniques: client-side attacks, LastPass-side attacks, and attacks from the outside.
Regarding the first method of attack, the researchers found a way to exploit session cookies, allowing them to gain access to the encrypted vault key.
“We can use the session cookie to query LastPass and obtain the pwdeckey value,” the duo explained. “Once we have that, we can derive a key by doing SHA256(pwdeckey). Now we just need to extract the encrypted vault key from the SQLite DB and decrypt it using the key we just derived.”

After unearthing some weaknesses in the way LastPass configured its two-factor authentication protocols, Vigo and Garcia eventually found a way to recover a disabled One Time Password (known as a dOTP, and which the researchers describe as a “master password on steroids”) that is stored locally on a user’s machine.
“This is key to understand the advantage of this attack versus stealing the master password which needs the victim to have previously clicked ‘Remember Password’,” the researchers note.
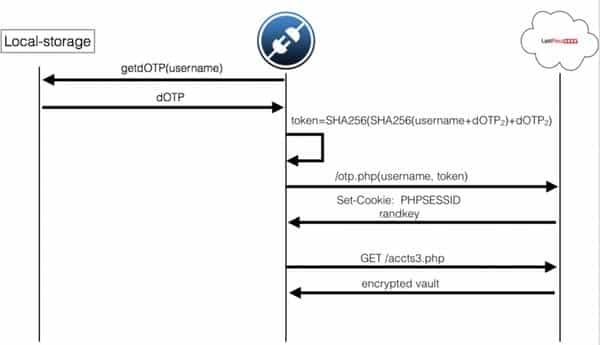
The duo finally used the dOTP to obtain the session cookie and the encrypted vault key, which they decrypted using the dOTP.
Moving on to LastPass-side attacks, Vigo and Garcia found that the vault itself was not encrypted per se but instead presented cleartext metadata with encrypted values. (The URLs/icons were only encoded, whereas credentials were encrypted using a weak method.)
They also found that LastPass added a “custom_js” parameter to every Account node:
“Javascript code that will be injected and run in every page load in the domain’s context. While this is a legitimate feature, it gives LastPass the possibility of stealing all your credentials.”
For outside attacks, the researchers do not go into too much detail in the blog post, and instead direct readers to view the slides of their talk.
At first glance, these bugs with LastPass might seem to endorse the actions of those who – against the advice of some – immediately decided to migrate away from LastPass after the company was bought by LogMeIn.
But, as Vigo and Garcia note, LastPass may not be the only password manager with vulnerabilities, and its development team have at least responded to the findings in what seems to be a responsible and timely manner:
We found a number of bugs, bad practices and design issues and used them to obtain the vault key and decrypt all passwords in different scenarios.
There is no bug-free software and any future research on other password managers would likely have similar results.
LastPass has responded and fixed most of the issues in less than 72 hours.
“We want to point out that the security team at LastPass responded very quickly to all our reports and lot of the issues were fixed in just a couple days,” the pair explain. “It was very easy to communicate and work with them.”
Password managers can have their weaknesses, but as pointed out by Bob Covello on Tripwire’s The State of Security blog, even faulty password managers are a good choice versus users storing their passwords in local files.
LastPass has taken responsibility for its bugs; it stands to reason that many of these issues will therefore not resurface going forward.



All products, even 1Password and so on are going to have vulnerabilities – the main thing here really is how quickly and responsive is the company's attitude to fixing the issues and it's a good thing that LastPass was easy to work with for the researchers and have fixed the issues in a short space of time – that's the kind of thing you want to see from a product that basically hold your crown jewels.
Mind you, it IS in LastPass' interest to have this – if they denied it, didn't bother to fix etc, they'll lose customers. Fast.
What? You mean LastPass charge you for keeping your passwords safe? OMG! It should be a free service for everyone, since it is in the best interests of the internet to have a certain level of security for people's details. A less secure internet equates to less business transacted upon that internet.
You obviously haven't followed the news. LastPass was bought by LogMeIn. I wish it was the other way around.
Wish I was in that room. I was talking in the Business and missed this one. Would have been fun to watch.
Really? Why should they have to make a free software that they aren't compensated for? Who died and made LastPass the Elder Guardian of the Internet? They are providing a valuable service, and they should be paid for it. I am a paying customer of LastPass, and this ensures that my interests are protected. I will continue being a customer as long as they continue doing what they are doing.
I am sorry, but I do my bit as a programmer – I write and maintain MJ Registry Watcher (http://www.jacobsm.com/mjsoft.htm#rgwtchr) to safeguard PCs everywhere whilst being as unobtrusive as possible in terms of alerts and resource usage. It is free, as is all my hobby software. If I ever get round to hosting a 24/7 up server, I will write a password manager that is both secure and F.O.C. and post a link to it on my software page at http://www.jacobsm.com/mjsoft.htm
Did I miss something here? I'm a LastPass (extension) user in both Firefox and Chrome and it's free for the non-premium user. I've looked at the extra features for the premium version and I simply don't require them. Now I've read and re-read the article and nowhere does it state, that I can find, the you have to pay to keep your passwords secure. The security is the same for the free and premium versions as far as I can tell.
So…what did I miss here?
I started very anxious reading the article, and the end is comforting me.
The human management of a software is the most important.
You are right, if LP was not responding quickly, they would lose customers.
LP is on a market of security aware people, so they have to be careful on that.
Hi,
I hate to tell lastpass fans,,but the Android version is vulnerable,and they have known for years now,but sacrifice usability for security. They use the world readable clipboard to facilitate loading user name and passwords. This vulnerability has been known for years now,and the only password manager to do this in a secure way is Keepass 2 for Android. They incorporated a stand alone keyboard inside the app. Almost every other well known PWM for Android can be spied on. I have the research papers to back this up if anyone is interested.
Hate to tell you, but LastPass has had a standalone keyboard for years. Also on Android 5.0 and later, it can autofill many apps directly, without using the clipboard, and without using the custom keyboard.
Hi, here is lastpass blog statement:
When you tap the helper, LastPass displays matching logins for the web site or app. In the cases where the web site or app doesn’t allow LastPass to autofill, as we sometimes see with financial apps, the app fill helper will offer convenient copy-paste options instead.
https://blog.lastpass.com/2014/11/lastpass-app-fill-on-android-gets-update.html/
They are still using the clipboard to copy and paste for convenience. Do you have anything newer to disprove?
And here is research on lastpass done not long ago. This explains how they were still using vulnerable approaches to fill. Read this,then tell me how lastpass overcame the vulns.
http://blog.xbc.nz/2014/12/how-android-password-managers-fall-prey.html?m=1
I'm not sure I see a significant difference. Unless it has recently been removed, Keepass for Android is also able to copy passwords to clipboard.
So both Keepass and LastPass have soft keyboards, and both have clipboard copy/paste. The primary way of filling in LastPass is autofill, which doesn't use the clipboard and so is more secure.
Since this article only mentions vulnerabilities and not exploited or in the wild vulnerabilities, I'd consider LastPass still one of the best password managers available. No users were affected so everyone is still safe using LastPass.
Hi Norbert,
Do you use lastpass on Android? See my reply above. The majority can be spied on when using clipboard,either by you or the manager app. And lastpass DOES use it,and has left this in place without warnings to users,unless that changed in the past year?
Google Spies on everyone and everything you do. All iPhones and Android devices have backdoors from their OEM so anything is hackable and viewable. Accessing from your mobile device is much less secure than accessing it from a Box.
Anybody who reads the full research, and understands it, will appreciate the severity of the vulnerabilities. Now that LastPass has been bought by LogMeIn it remains to be seen whether they will rectify them.
The attack surface against LastPass is not insignificant; mobile users are at the greatest risk overall. Everything with security is a compromise: whether LastPass fits in to your threat model is a decision for the individual user. The unwillingness of LastPass to make all of their source code open-source doesn't engender trust.
Right on,right on!
"We want to point out that the security team at LastPass responded very quickly to all our reports and lot of the issues were fixed in just a couple days," the pair explain. "It was very easy to communicate and work with them."
ID federations (single-sign-on services and password managers) create a single point of failure, not unlike putting all the eggs in a basket. It remembers all my passwords when un-hacked and loses all my passwords to criminals when hacked. It should be operated in a decentralized formation or should be considered mainly for low-security accounts, not for high-security business which should desirably be protected by all different strong passwords unique to each account.