The FBI is currently investigating hundreds of infections tied to a mysterious family of Mac-based malware called “FruitFly.”
When asked about the threat, a spokesperson for the Bureau told Motherboard that “as a matter of longstanding policy, the FBI neither confirms nor denies the existence of investigations.” But two security researchers say the FBI is indeed investigating the malware.
One of the researchers, Malwarebytes’s Thomas Reed, discovered the first variant of FruitFly back in January 2017. At the time, he described the threat as “a piece of malware unlike anything I’ve seen before, which appears to have actually been in existence, undetected, for some time.”
FruitFly 1 is “extremely simplistic on the surface,” in Reed’s estimation. But it distinguishes itself by its use of “ancient” functions to capture screenshots and obtain webcam access. The malware’s binary also contains libjpeg, open source code which hasn’t received an update since 1998.
None of this necessarily means FruitFly is an old threat. But it certainly could have been around for decades. If that is the case, the question is how it could have survived that long while evading detection.
Reed has an answer:
“The only reason I can think of that this malware hasn’t been spotted before now is that it is being used in very tightly targeted attacks, limiting its exposure. There have been a number of stories over the past few years about Chinese and Russian hackers targeting and stealing US and European scientific research. Although there is no evidence at this point linking this malware to a specific group, the fact that it’s been seen specifically at biomedical research institutions certainly seems like it could be the result of exactly that kind of espionage.”
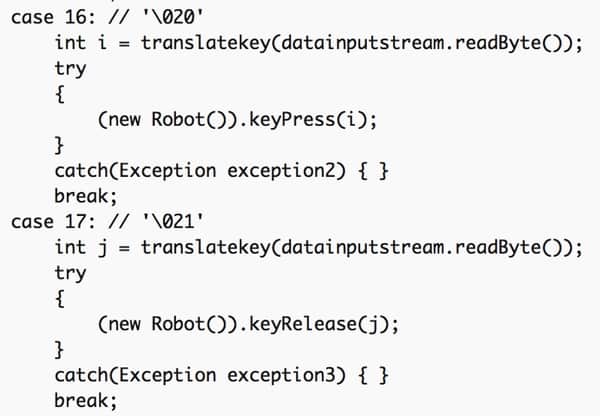
Reed ultimately told Apple about FruitFly 1, which issued a patch for the malware and told the Malwarebytes researcher that the FBI was investigating.
Patrick Wardle, a developer of Mac-based security tools, came across FruitFly 2 and quickly learned that the malware was using backup servers to send victims’ stolen information back to its creators. Wardle therefore decided to register one of those backup domains. When he fired up the command and control (C&C) server, he received information on 400 Mac users who had fallen victim to the malware.

Unlike the victims of FruitFly 1, those ensnared by FruitFly 2 mainly consisted of average users living in the United States and Canada. Wardle made a note of these infections and reported them to the FBI.
Given the variations between FruitFly 1 and FruitFly 2, neither Wardle nor Reed know how the malware gets onto a victim’s computer or who’s behind it. But they do know one thing: it demonstrates the extent to which EVERYONE, including Mac users, is vulnerable to malware. As Wardle told Motherboard:
“If there are hackers out there who are specifically targeting families or individual Mac users, that kinda makes my stomach turn. People need to be really cautious when they use their computers, when their kids use their computers. Just because they have a Mac, it doesn’t mean that they’re safe.”
With that in mind, Mac users should make sure they follow security best practices on their machines. Those measures include installing an anti-virus solution onto their computers, updating their systems on a regular basis, and exercising caution around suspicious links and email attachments. For more targeted security protection against threats like ransomware and webcam-piggybacking malware, check out Wardle’s security tools here.



It's too bad that when Johnathan Zdziarski went to work for Apple recently, in the security division, he sold a program he developed, called
"little Flicker" to F-Secure, who incorporated it into their AV products for Mac. You can do a search to get more information on it.
Sorry "Little Flocker" was the name of the program.