 The frustrated researcher, who failed to get an adequate response from Facebook’s security team and so hacked Mark Zuckerberg’s page to get their attention, is not going to receive a bug bounty for his discovery the social network has confirmed.
The frustrated researcher, who failed to get an adequate response from Facebook’s security team and so hacked Mark Zuckerberg’s page to get their attention, is not going to receive a bug bounty for his discovery the social network has confirmed.
In a posting made last night on the social network’s security page, Facebook chief security officer Joe Sullivan admitted that his team made mistakes in its interactions with Palestinian researcher Khalil Shreateh and failed in its communication with him.
As a result, the site is going to make some changes in how it responds to potential vulnerability reports.
“We should have explained to this researcher that his initial messages to us did not give us enough detail to allow us to replicate the problem. The breakdown here was not about a language barrier or a lack of interest — it was purely because the absence of detail made it look like yet another misrouted user report.”
“We will make two changes as a result of this case: (1) We will improve our email messaging to make sure we clearly articulate what we need to validate a bug, and (2) we will update our whitehat page with more information on the best ways to submit a bug report.”
From the looks of things, it’s true that Facebook didn’t really try very hard to explain the level of detail it required from Shreateh to confirm that a flaw existed on its social network.
He made two attempts to tell Facebook about the flaw, pointing them to a URL where he had managed to post a message containing a link to an Enrique Iglesias video on the wall of Sarah Goodin, a woman who had gone to college with Zuckerberg.
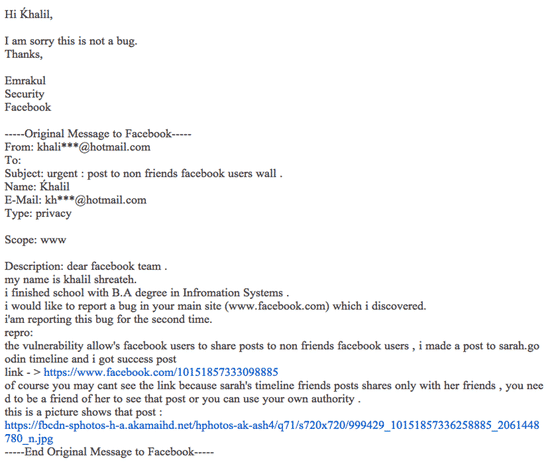
Facebook’s security team clearly failed to understand the scope of what Shreateh was attempting to report, but that should have been the cue for them to point him towards detailed directions of the type of information they required to properly investigate a report of a bug or vulnerability.
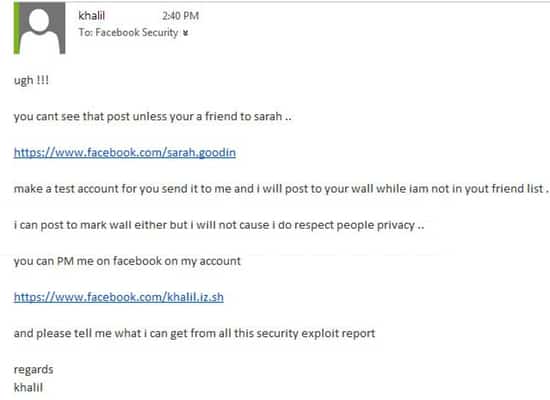
Instead, Facebook’s curt unhelpful response to Shreateh left him vaguely threatening to post on Mark Zuckerberg’s wall.
(Something he said he would not do because he “respected people’s privacy”, but did actually do in the end.
Joe Sullivan says, however, that Facebook will not change its policy of refusing to pay rewards to security researchers who test vulnerabilities against real Facebook users:
“It is never acceptable to compromise the security or privacy of other people. In this case, the researcher could have sent a more detailed report (like the video he later published), and he could have used one of our test accounts to confirm the bug.”
And you know what? I agree with Facebook. Shreateh shouldn’t have messed with anyone’s Facebook page without their permission. Yes, we should be grateful that he didn’t abuse the flaw in a malicious way, or sell details of the bug to online criminals who could certainly have used it to their advantage.
But it would have been better if he had only used test accounts to show how the flaw worked, and if he was frustrated by Facebook’s less-than-great way of dealing with him sought the assistance of the media or other researchers to underline the importance of what he was trying to report.
Does that mean Shreateh shouldn’t receive a reward? Well, although many will feel he does deserve to receive a bounty for finding a bug – it doesn’t look like Facebook is prepared to make an exception and shift on this one.
Let’s hope that this unfortunate interaction doesn’t prevent Shreateh from responsibly reporting flaws to Facebook in future, and – if he does – let’s hope that he receives the bug bounty reward that he will deserve.
If you are on Facebook, and want to be kept updated with news about security and privacy risks, and tips on how to protect yourself online, join the Graham Cluley Security News Facebook page.
If you’re thinking of leaving Facebook, why not listen to this “Smashing Security” podcast we recorded:





I would probably review "Enrakul"'s other responses to see if any other non-bug reports have been waylaid with curt responses or otherwise dismissed.
I don't agree – how many times did the guy have to try to get them to listen by doing things *their* way?
Once should be enough.
Funny how they realized he was right once he posted on Z's page?
He followed their rules until they stopped listening.
While ethically (and legally) it might not be best to explicitly exploit a system/network/his page, this is a perfect example of how 0-day exploits are (or can be) good. Yes, it is best to try to work with the vendor but if they refuse to fix (as often is the case) then you have two choices:
– stay quiet about it and hope no one with malicious intent finds it (which is security through obscurity and just because the vendor thinks it is a good idea – obviously – does not mean it is. Indeed it is very stupid and dangerous).
– write an exploit and releasing it to (example) an advisory list, or actually exploit something (legally and ethically do the former, but obviously the latter is done by some, despite the risks) and force the vendor to fix it. If it isn't fixed one day someone who wishes to cause much more harm will eventually find it and take advantage of it _without_ the vendor knowing about it (it = taking advantage of the hole) until it is too late. Need an example? Target's POS (the irony…) being infected with malware leading to many compromised customer accounts…. Even if that was not something previously discussed with Target (I suspect it was not but I don't know) the point is that it should be fixed as soon as possible to prevent abuse by those with malicious intent who happen to find a hole.
If Facebook were smart they would offer Khalil a job.
Finally, He was lucky I think. A user on gofundme.com has created a funding campaign to rise 10,000 $ reward to Khalil and he has gotten more than 11,000 $.
www.gofundme.com/3znhjs