 I’ll be honest with you. LinkedIn scares me.
I’ll be honest with you. LinkedIn scares me.
For any criminal interested in targeting senior staff in an organisation, it’s a goldmine of information.
With just a few clicks they can find out who has what job, who they are connected with, and often their contact information. Even if their contact information isn’t visible, it’s often just a simple case of .
With that kind of information it’s not too hard to rustle up a convincing-looking phishing email or send over a poisoned PDF attachment that drops malware onto the recipient’s PC.
But hopefully your CEO and other senior members of staff have received security awareness training. Fingers crossed, they’ve been warned of the risks and the danger of targeted attacks, and are on the lookout for unexpected messages they might receive and the risks of the internet.
So far, so good.
 But there’s someone on your company’s payroll who has access to your CEO’s email, may know the boss’s credit card number, their passwords… someone who organises the CEO’s travel arrangements on his or her behalf, remembers the wedding anniversary and arranges the flower delivery to their home.
But there’s someone on your company’s payroll who has access to your CEO’s email, may know the boss’s credit card number, their passwords… someone who organises the CEO’s travel arrangements on his or her behalf, remembers the wedding anniversary and arranges the flower delivery to their home.
Someone who sees the minutes of the board meetings, and knows probably as much as it’s possible to know about what the CEO is thinking and what the business is up to, without being the CEO themselves.
And that person is the PA to the CEO.
Yesterday, at the annual Project Honeynet workshop in Stavanger, Norway, security expert Per Thorsheim gave a presentation where he discussed the dangers posed by the CEO’s personal assistant.
Thorsheim described how he went onto LinkedIn and searched for “PA to CEO”. In London alone there were over 800 results.
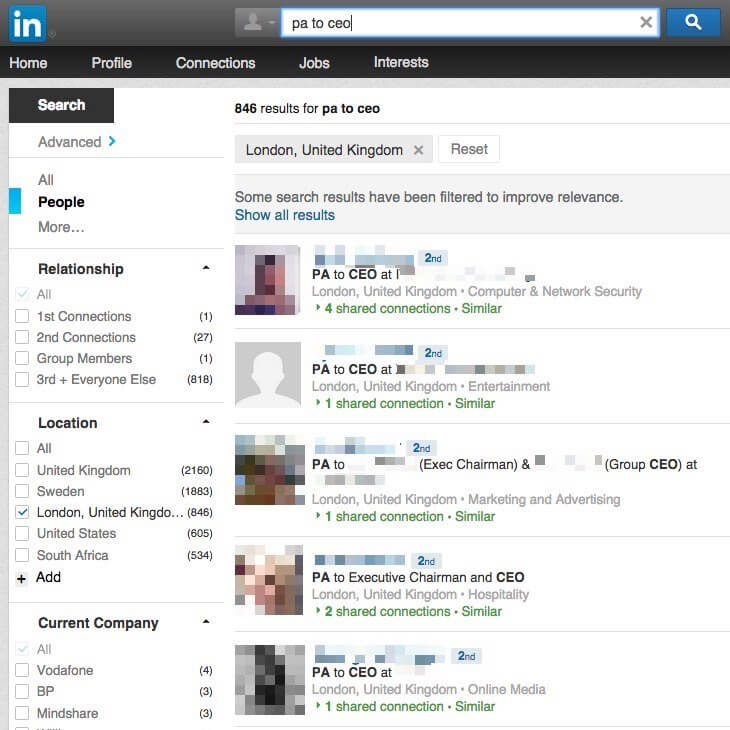
So, what are the risks?
Well, one danger is that your company may not have been as diligent in training the PA about information security risks as others in the organisation.
And, because the PA may have access to senior staff’s calendars, email and sensitive documents they could be viewed as a soft target for a determined hacker.
Last year’s hack against Sony Pictures revealed the sloppy security practices at the upper tiers of the company, with the CEO sharing a terrifying amount of personal and sensitive information with his personal assistant:
The emails show CEO Michael Lynton routinely received copies of his passwords in unsecure emails for his and his family’s mail, banking, travel and shopping accounts, from his executive assistant, David Diamond. Other emails included photocopies of U.S. passports and driver’s licenses and attachments with banking statements. The stolen files made clear that Diamond was deeply trusted to remember passwords for Lynton and his family and provide them whenever needed.
“I still need the password to your Amazon account,” Diamond wrote to Lynton in August.
 Another risk is perhaps highlighted by the skewed demographic found in the LinkedIn profiles of personal assistants.
Another risk is perhaps highlighted by the skewed demographic found in the LinkedIn profiles of personal assistants.
Of the first 100 results displayed, there was only one man to 99 women. You’ll no doubt be shocked to hear that the typically male CEO tends to hire attractive young women in their twenties and thirties to be their personal assistant.
If an organised criminal gang wants to scoop up sensitive information from a particular company, do you imagine that some of them won’t consider flirting with the CEO’s PA? Maybe finding them online and then seeking them out in real life for romance, or maybe conducting an internet love affair?
Of course, this is far from a problem that only impacts female victims. When it comes to making poor decisions, men are just as capable as women. But with the majority of attackers believed to be male, and the propensity for females to hold the targeted position of personal assistant, there may be more opportunities for a “real-life” fake romance to be instigated.
We’re all human and we all want love, and it’s all too easy to imagine how hurriedly someone who thought they were falling in love with “Mr/Miss Perfect” would click on a dangerous link or open a malicious ecard.
Thorsheim raised another sinister danger. During the troubles in Northern Ireland, the IRA engaged in what became known as “tiger kidnapping” where an innocent person would be abducted.
However, rather than demanding a ransom be paid the kidnappers would coerce a family member or loved one of the abductee to commit a crime (such as robbery or planting a bomb) to ensure their safe return.
Just imagine, explained Thorsheim, how a poorly-paid personal assistant might be persuaded by organised criminals into infecting a laptop with a USB stick carrying malware, handing over a social media password, or opening an dangerous email attachment.
So, what can we learn from all this?
According to Thorsheim, it’s time to think outside the box and look further than your own responsibilities if you want to see the big perspective.
Chances are that your organisation has information or resources which have a commercial value to today’s cybercriminal. Sites like LinkedIn provide a valuable stepping stone in helping criminals determine who to target inside your organisation, and how to reach them.
If you leave users uneducated about the risks and the dangers to look out for, if you continue to act sloppily with your sensitive data and passwords, you’re playing a very dangerous game.
For more information, watch this video from the Project Honeynet workshop which contains Per Thorsheim’s talk (he starts discussing the Personal Assistant risk at about 3 hours 31 minutes into the video)



As someone involved in fighting this largely invisible war, I see thousands of sleepless predators constantly looking for any weakness to exploit in company defences.
I have come to realize, that if your company is still trading and solvent at the end of every day, then your system administrators have earned their pay!
In this information age, it is inexcusable for any employee not to have some understanding of IT security practices, and CEOs must take it seriously and not override nor ignore the advice of the security personnel they employ.
Mailing an infected USB stick to that person at the company is probably a lot simpler than making them fall in love with you.
Also Graham, it's quite hard to see the text that is hyper-linked at times, perhaps consider bolding it up or using a different color.
Thanks anonymous. Let me take a look at the CSS and see what I can do
Much better!
Graham, just a suggestion for this part:
"Even if their contact information isn't visible, it's often just a simple case of firstname.lastname@…"
Maybe use one of the for-documentation domains – example.com for example (what to say there, I guess 'for instance' ?). Because even though it isn't a mailto, and even though there might not be an address (probably isn't and probably never would exactly that – if someone does have an address called firstname.lastname[1] I'd be perplexed) as such, if company.com exists (and haven't checked) then there's the risk of someone eventually having to deal with it (even if it being bounced). In either case, it seems more appropriate (but I admit I'm a very literal thinker, and given that it isn't a mailto this fact is probably more obvious) in that this is documentation (even if not strictly technical it is still documenting associated risks of social media). Just a random thought that probably isn't all that important.
[1] Don't forget wildcard addresses though.
I don't have any other comments here about the article but I do have a remark for Andy: Yes, it is unfortunate there is a lack of training, and yes it is unfortunate that some don't realise just how serious the problem is. But lack of awareness leads to this condition and because of this basic training will not reach everyone, ever, unfortunate as it is. I agree CEOs – and this goes for everyone – shouldn't dismiss advice (but not everyone is given advice). But it is, I fear, quite excusable (of themselves, that is) that the regular employees don't have this training or aren't aware of the risks/practises/etc.; it would be nice if that wasn't the case but if they're not paid for it – which is to say they're not given training on company time – or if they don't know there are risks at all (see first part), it really isn't inexcusable (of the employees specifically). It is rather unfortunate, however, that those who can make the changes in the corporation do not try or do not have enough authority if they do try (like you suggest should be done but isn't). And indeed yes, that is rather inexcusable (but there will always be corporations/organisations/individuals that won't change here or anywhere else, for that matter).
Changed to example.com. Thanks Coyote!
(previously accidentally posted in response to a different comment on a different article!)
My experience has always been the worst breaches are the bosses fault, at two previous companies the CEO infected the company with a virus and another idiot boss got the cryptolocker virus and encrypted the support docs. Typically the bosses are so full of themselves they won't listen to warnings. Neither boss was even reprimanded nor fired as they should have been so the security problem continued.
The problem is that you can use that logic with many more things (which all comes down to they made a mistake or mistakes) and if you were to fire people for making mistakes (which like it or not, ignoring warnings is a mistake) you'd have no one left but those who are perfect (which I'm afraid is no one). This is especially true if they didn't break corporate policy, though. But then the security problems won't go away anyway. All it takes is one person or one bad circumstance to break all that went in to preventing (or attempting to prevent) problems. Once a link ('person') breaks apart from the chain ('corporate policy') there is a problem, and everyone can make mistakes, even those that know better. For every boss that is an idiot (as you say) there's more employees that are also 'idiots'. It goes both ways, too (and this also goes for brilliant, dense, funny, cold, etc.). There's always someone to best you (and it doesn't have to be 'positive' things anymore than it does 'negative'). It doesn't matter which group you're in, though. Just like there are really foolish employees there are also very smart employees. The same goes for employers.
Edit: Oh, and yes. Some bosses are full of themselves. But it isn’t limited to bosses. It is a human trait.
I take great exception to this piece.
I've spent over two decades in administrative and Personal Assistant roles, and over the last five years I've built my own business training more than 2,500 Personal and Executive Assistants all over the world. In the whole of this time I have not yet met a single PA or EA who doesn't have far more technical knowledge or isn't more security conscious than their CEO.
Invariably it is the PA / EA who trains their boss to use their iPad, iPhone, Blackberry or computer – and who reminds them not to click dangerous email links or open dodgy website addresses. Personal and Executuve Assistants have far more intelligence and IT / security know-how than this piece gives them credit – and the mere idea that being chatted up by someone will make the average PA suddenly divulge private and confidential information is ludicrous. The role of secretary (from which the PA / EA role has developed) was named after all because we are the 'keeper of secrets'. Oh, and none of us are 'average' either – for the most part PAs and EAs are exceptional.
Just take a look at any of the PA / EA magazines, books, blogs, training websites and LinkedIn discussion groups out there – and you will see that PAs and EAs are campaigning worldwide for more recognition of what we have to offer in the workplace. Gone is the stereotype of the 1950s 'Miss Jones' who types up a few letters between filing her nails. PAs and EAs are becoming Business Partners with their CEOs and Executives – and articles such as this one do nothing to further our development or aid our cause.
In a 2012 survey by Reed.co.uk, CEOs and Chairmen attributed 40% of their productivity (and hence, their success) to their Assistant.
Please give credit where it's due, and stop perpetuating the myth that PAs and EAs are dumb dizzy gals (and guys) who haven't a clue what they are doing. Assistants are a force to be reckoned with.
Angela Garry –
Author: "Brave PAs"
Editor: National association of Headteachers' PAs magazine
The workd's most connected Personal Assistant and PA Trainer on LinkedIn
"In the whole of this time I have not yet met a single PA or EA who doesn't have far more technical knowledge or isn't more security conscious than their CEO."
I know you feel I am tarring all PAs with the same brush (which certainly wasn't my intention), but haven't you just done the very same to their bosses? How do you know what the technology knowledge and security awareness of those 2500 CEOs is?
By knowing my audience, Graham.
If you re-read my message, you'll see that I have worked with these PAs / EAs during my training courses, within which I encourage them to share their experiences.
As the major responsibilies of being a PA / EA include being able to maintain confidentiality and security for their bosses and being able to use technology, these are naturally topics which are included in my training courses.
Okay, so you're not saying that all 2500 PAs and executive assistants knew more than their CEOs about computer security and privacy, but that they told you they knew more…
Fair enough.
People, of course, are often less than honest when admitting their own shortcomings or indeed recognising when they may have goofed. It’s human instinct for many of us to think that we do a better job than others.
And maybe it’s true in the case of these PAs. I don’t know. I do know that there are plenty of senior executives who are terrible about following IT security rules and regulations, and some who are very good.
The point I was making (based upon Per Thorsheim's presentation) was that companies "may not have been as diligent in training the PA about information security risks as others in the organisation."
That's no slight on a PA's capabilities, it's a concern that not everyone might be receiving the right assistance to deepen their knowledge of the latest computer security threats.
With state-sponsored and targeted attacks, we're living in a very different world when it comes to infosecurity than we were even five years ago.
Please don't take it as an attack against people who are typically working long hours in a very hard job with often low recognition.
I'm re-posting this response – as it seems to have been removed, less than 50 minutes after I posted it.
I take great exception to this piece.
I've spent over two decades in administrative and Personal Assistant roles, and over the last five years I've built my own business training more than 2,500 Personal and Executive Assistants all over the world. In the whole of this time I have not yet met a single PA or EA who doesn't have far more technical knowledge or isn't more security conscious than their CEO.
Invariably it is the PA / EA who trains their boss to use their iPad, iPhone, Blackberry or computer – and who reminds them not to click dangerous email links or open dodgy website addresses. Personal and Executuve Assistants have far more intelligence and IT / security know-how than this piece gives them credit – and the mere idea that being chatted up by someone will make the average PA suddenly divulge private and confidential information is ludicrous. The role of secretary (from which the PA / EA role has developed) was named after all because we are the 'keeper of secrets'. Oh, and none of us are 'average' either – for the most part PAs and EAs are exceptional.
Just take a look at any of the PA / EA magazines, books, blogs, training websites and LinkedIn discussion groups out there – and you will see that PAs and EAs are campaigning worldwide for more recognition of what we have to offer in the workplace. Gone is the stereotype of the 1950s 'Miss Jones' who types up a few letters between filing her nails. PAs and EAs are becoming Business Partners with their CEOs and Executives – and articles such as this one do nothing to further our development or aid our cause.
In a 2012 survey by Reed.co.uk, CEOs and Chairmen attributed 40% of their productivity (and hence, their success) to their Assistant.
Please give credit where it's due, and stop perpetuating the myth that PAs and EAs are dumb dizzy gals (and guys) who haven't a clue what they are doing. Assistants are a force to be reckoned with.
Angela Garry –
Author: "Brave PAs"
Editor: National association of Headteachers' PAs magazine
The workd's most connected Personal Assistant and PA Trainer on LinkedIn
"I'm re-posting this response – as it seems to have been removed, less than 50 minutes after I posted it."
Your post wasn't removed. Because it was your first comment on this site it was placed in a queue for pre-moderation.
I fully accept that there are many PAs who help their bosses with technology and may know about computer security and best practices. More power to them! I don't think my article was saying that they don't exist.
A former PA myself, I am a Microsoft Certified Trainer and CEO/Founder of RedCape, the global leader in engaging productivity and technology training for Executive Assistants and their teams. We have defined the 11 core skills and 5 specialty skills for The Tech Savvy Assistant and one of the workshops I teach is "LinkedIn for Assistants". There is not one valid point in here I would add to my workshop unless I wanted my session to be a comedy routine. We'll "no doubt be shocked to hear that the typically male CEO tends to hire attractive young women in their twenties and thirties to be their personal assistant." WHAAAAT? Where's the proof in that? That is ridiculous. You might as well change that to the "typically *narcissistic* male CEO tends to…" There's no proof in that either but it's more believable. And what REALLY irks me is the thought that PAs/EAs are love targets. This is laughable! And I just might quote you in my session for some comedy relief.
Here's what I know to be true.
1. PAs are WELL aware they are the gatekeepers and that many people want to get to their leader through them. That's a given.
2. PAs are highly intelligent business partners with their leader.
3. PAs are life-long learners and focus on relevant training for their roles. LinkedIn and privacy are definitely one of the many skills PAs keep an eye on.
Rather than insult the millions of PAs around the world, you should have simply provided some practical and valuable tips.
"We'll "no doubt be shocked to hear that the typically male CEO tends to hire attractive young women in their twenties and thirties to be their personal assistant." WHAAAAT? Where's the proof in that? That is ridiculous."
Firstly, it's actually a comment from Per Thorsheim (watch his presentation in the video link) that I'm reporting in the article.
Secondly, I did the search for "PA to the CEO" myself on LinkedIn. 99% were female, and overwhelmingly – to my eyes – young women in their twenties and thirties. I'm not saying that's a good thing.
In my experience, executive assistants and personal assistants do a great job of acting as a gatekeeper to their bosses. However, I've also seen C-level executives given security training that has not been shared with their assistants.
Well said Angela – I am also flabbergasted by the comments regarding Personal Assistants.
I have been in the profession for 20 years and have been a PA to two European Vice Presidents.
I can certainly testify to being more tech savvy than any boss I have ever had (male or female).
Any PA to a CEO is a strategic business partner and vital member of the executive management team.
There is so much more to us than tea and typing (& email exchanges with online suitors?!) but clearly the old school secretary paradigm still exists.
#adminproud
Jennifer – you sound like a great PA, and I wish you well in training your bosses to understand computer security and privacy better.
However, there's always an opportunity to learn more as attacks have become more sophisticated, and increasingly use advanced social engineering techniques and zero-day vulnerabilities to infect computers. I would love to see more people – at all tiers of the company – given deeper training to protect themselves and their company's sensitive data.
It sounds like we're on the same page. I agree that any PA to the CEO is an important and vital member of the team. I hope that they receive the same security training and resources to reflect that.
By the way, I don't think I mentioned tea or typing. We're all – male and female – potentially susceptible to romance scammers and fraudsters. It's a traditional method of social engineering that has worked time and time again.
What cannot be denied, however, is that most attackers appear to be male and (according to LinkedIn – try it yourself if you don't believe me) most PAs to the CEO happen to be female.