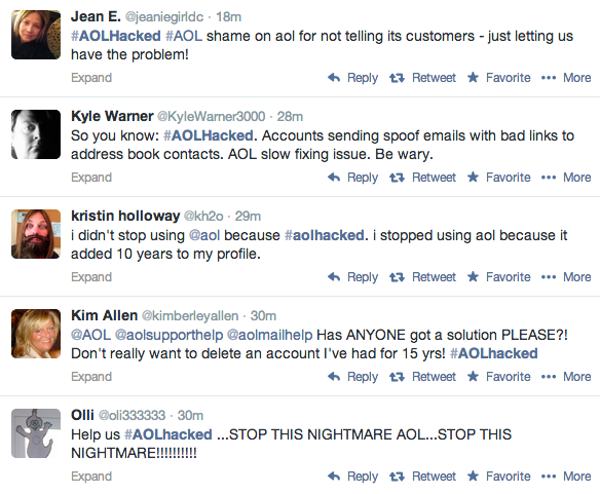
It seems there is a big spam problem involving AOL accounts right now.
You only have to check out the #AOLHacked hashtag on Twitter to see many people complaining.
I don’t have many friends who still have AOL addresses, but a few (less technical) chums of mine are still saddled with them.
Which means, in the last few days, I’ve been getting spam from them too.
Here’s an example:
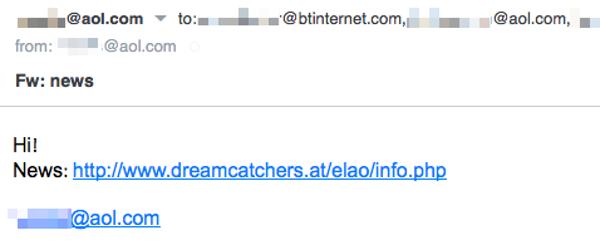
Subject: Fw: news
Message body:
Hi!
News: [LINK]
If you receive a spam email like this and click on the link you will be taken to a bogus news website, peddling a Garcinia Cambogia miracle diet, purportedly being backed by TV celebrities such as Dr Oz.
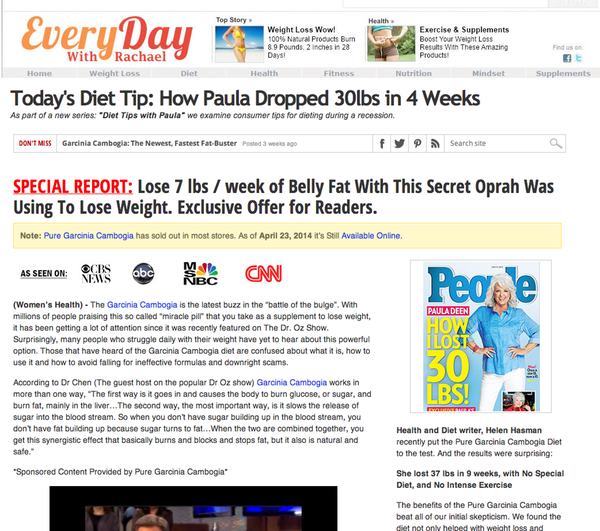
No one is suggesting that Dr Oz, Oprah, and other celebrities mentioned on the webpage are in anyway associated with the spam campaign of course. The spammers are simply trying to drive as much traffic as possible to their diet-pushing website, in the hope that a small percentage of people will be lured into purchasing.
And, of course, the spammers will earn cash the more sales that are made.
In the past the people selling the miracle diets have disguised their sites as BBC News pages and hijacked Twitter accounts, Pinterest, Facebook and Tumblr to spread their ads.
But be wary if you are visiting the sites from an Android device. As Martijn Grooten from Virus Bulletin reports, you could be hit by a variant of the NotCompatible Android Trojan horse.
Quite what the problem is at AOL is currently unclear, but the site has just published a blog post acknowledging that there is an issue:
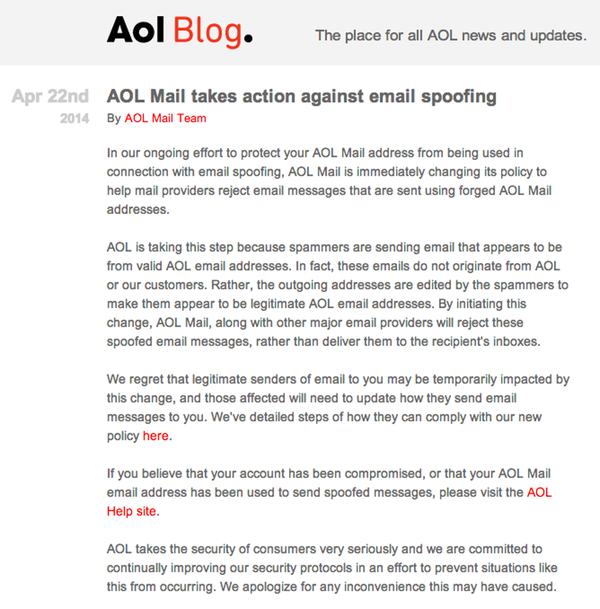
In our ongoing effort to protect your AOL Mail address from being used in connection with email spoofing, AOL Mail is immediately changing its policy to help mail providers reject email messages that are sent using forged AOL Mail addresses.
AOL is taking this step because spammers are sending email that appears to be from valid AOL email addresses. In fact, these emails do not originate from AOL or our customers. Rather, the outgoing addresses are edited by the spammers to make them appear to be legitimate AOL email addresses. By initiating this change, AOL Mail, along with other major email providers will reject these spoofed email messages, rather than deliver them to the recipient’s inboxes.
We regret that legitimate senders of email to you may be temporarily impacted by this change, and those affected will need to update how they send email messages to you. We’ve detailed steps of how they can comply with our new policy here.
If you believe that your account has been compromised, or that your AOL Mail email address has been used to send spoofed messages, please visit the AOL Help site.
AOL takes the security of consumers very seriously and we are committed to continually improving our security protocols in an effort to prevent situations like this from occurring. We apologize for any inconvenience this may have caused.
My reading of AOL’s statement is that they are claiming that their site has not been hacked itself, but instead spammers are forging email addresses to pretend that they come from legitimate AOL users.
Of course, this doesn’t explain how the emails are being sent to genuine contacts of those particular AOL users – have the address books of AOL users or AOL’s mail logs somehow fallen into the hands of malicious third parties?
Lets hope more details emerge soon about what’s going on, before I have to tell the few AOL-using friends I still have to upgrade to another email service.
(And no, I’m not recommending Yahoo. Sorry Marissa.)



It's happening to me. Emails are being sent not only to people in my contact list, but also (to judge from the undeliverable return emails I have been receiving) a lot of other, bogus emails.
I've checked my sent folder… nothing. I've changed my password and run the most thorough virus scan of my computer that I can run (it's clean), and it still hasn't stopped it from happening.
I hope it stops soon. Thanks for posting this information.
Ah, the oh so lovely 'required' DSN (delivery status notification) with emails and mail bouncing (which can end up spamming others as you've noticed*). Personally, on my server, if I am rejecting mail for no-such address I just silently discard it (just like with spam, malware, etc.). Anyone having a problem with that can run their own mail server their own way (and not try to send mail to some supposed account in the first place and/or think I would be an open relay): I'm not about to become a backscatter of any kind (or anything like that) and I'm not going to put any other effort into filtering (so that I can send to 'legit' mailers the failure… it is 99.9999% of the time a spam attempt anyway.. and by way of maillog I can know if it is a friend of old who is trying to contact me and then I can contact them) it. If the mail doesn't exist well too bad; not a corporation, and only people I know have mails there and frankly if I haven't told them about the change in address then there's a reason for it (and the 'RFC non compliant' sites can ridicule me if they so choose just like I can ridicule them for being naive, arrogant and biased to the point of stupidity)! I sadly see so much seemingly pseudo-randomly generated account names that it would be ridiculous to even consider much else, nowadays, anyway (and the false positive is still a chance and I don't find anything like that acceptable… if there is an account I change and specifically want others to know about then and only then will I add a has moved mail).
*Similar is when a person uses an open relay to send spam at the same time spoofing the from address to their target. But instead of the mail being sent to the recipient, it bounces and now you get a bounced mail for a mail you didn't send in the first place. This is much like some DoS (denial of service) attacks that spoof the sender to be the victim so that the victim gets traffic in response to what they supposedly sent to the third party that is implicated. Many examples from over the years… Actually, I would argue that this IS a DoS in many senses of the word because you fill up someone’s inbox to the point of being more difficult to go through.
As an aside to your remark about your sent/outgoing mails: that would be more of an indication that it could be spoofing (unlike I described about hotmail). That or whatever is causing it – problem on their servers or a person or program – is also deleting outgoing mail that they send. Unfortunately, until AOL fixes their screwup you'll probably not know which it is (at least without breaking the law… which I would never suggest someone do, not in the past past nor present but especially post 2001/09/11). That is assuming they even mention what it is or was.
Hey Coyote:
Have you been out in the general population and tried to explain something this complex lately.
Most can't find thier ass with both hands..
Aon
Re:"Of course, this doesn’t explain how the emails are being sent to genuine contacts of those particular AOL users – have the address books of AOL users or AOL’s mail logs somehow fallen into the hands of malicious third parties?"
This was my first thought minus the contacts getting into the wrong hands (directly, will elaborate). Of course, that is possible TOO. Anyway, my thinking similar is because it is one thing for them to naively (okay, stupidly and shamefully) run an open relay or have some issue otherwise allowing "spoofing" (I don't buy this here! Not with the contacts and not widespread and not if it is coming from their server directly — which would indicate they have a configuration or some other more serious problem[s], wouldn't it? Yes, it would. They should be looking at analysing the headers of the mails either from afflicted victims OR better yet – not that this is really hard to think of – checking their mail log! ) of mail. However it is an entirely different issue for the contacts of the users to be sent mail from those so called spoofed addresses. My guess is it is similar to what MS (hotmail) had in the past (maybe still so ?). It was very similar and it was nothing to do with the user account in question. Because despite what MS claimed about it being malware, I had the same problem – I had a throwaway hotmail account – and they more or less suggested I go get a Windows antivirus – they were nice enough to "send me a link of Windows antiviruses" – to clean up my infected Fedora Core system (!!). Sadly I had told them in advance that I don't use Windows (admittedly I didn't elaborate much more because I knew it would be beyond their understanding) and yet they _still_ did that. It also should be noted I wasn't even logged in (I rarely did log in to hotmail) at the time of it being sent AND others had the same issue (who DID use Windows and I am sure at least ONE of them had a clean system and it was not an issue of Java or the like, either!). I also guess this is happening here with AOL. In my case I used that email for MSN (which certain contacts from over the years, were using.. again I don't use MS software but there is obviously open source clients for services… notwithstanding skype, at least for skype not a client in the usual sense – more like a backend) and since they were so brilliant I decided to take it into my own hands: I analysed the traffic between MS and me and luckily I discovered 'passport.com' (no email account) and then I abandoned use of MSN via hotmail.com – problem solved in my situation anyway.
I can only guess they were clueless (wait, we're talking about Microsoft – of course they were and still ARE clueless. What was I thinking?) and decided to not admit it like so many do out of fear of not knowing every thing in the world. Others had the same problem though (as noted) which is what raises the suspicion more so. Other evidence is I had a friend who was sent this crap supposedly from me, send me the full headers. Well, big surprise (not) when X-Originating-IP was not my (static) IP. Whether it is something like this, well, one can hope not but I wouldn't really be surprised with the so-called ISP AOL…
So either: AOL is ignorant as everyone else on the situation (in which case their staff should be working around the clock to sort their issue out) or they are full of it (like some other company I won't bother mentioning. Okay, that is because I mentioned them already, admittedly…). Possibly both (I will error on the side of most likely and suggest that it is indeed both).
On the other hand… maybe it is that darn Attrition again… they must be getting hell, seeing as how so many think they are AOL. Ha, that HAS to be it! (Brian – if I recall, that was your first name, I feel for you very much in that… of course, the fun you get with going postal maybe makes it more okay).
It's not the email account that's being hacked it's the person! They will have filled in some sort of form purportedly from their ISP or been sent to a spoof version of their ISP's site where they have entered their email address and password.
The spammer then accesses their email account, obtains the contacts but does not send from that account. They spoof the person's email address, sending a stream of emails to their contacts.
As the recipient is likely to know the sender, the theory is that there is a greater chance of the message arriving (maybe even whitelisted), being opened, read and clicked upon.
The most common type of these emails is the "I'm stranded in a foreign country, please send me some money" message, but many can contain just a URL as in the case above.
This is not limited to AOL accounts but to a whole host of other ISP accounts too.
>>>It's not the email account that's being hacked it's the person! They will have filled in some sort of form purportedly from their ISP or been sent to a spoof version of their ISP's site where they have entered their email address and password.<<<
I have never done this, nor has my ISP ever asked me for this information (I wouldn't give it to them if they did).
You're making the assumption it is a phishing attack. That isn't necessarily the case (see also the example I gave with how hotmail had something like this in the past, too). If it were a phishing attack that would be fine for you to write "not limited to AOL accounts but to a whole host of other ISP accounts too" but only partly because phishing is not ISP specific (that being noted, nice pun in there)! Phishing can be any service (or not a service – does the fact some groups have used phishing to gain access to a corporation's network ring a bell? Something like some news sites for instance?). Hell, if you want to go further, you can consider what Kevin Mitnick did a form of phishing (minus the "fake" pages; instead he would be the fake "page" himself): he would call up the company, convince (i.e., lie about being someone important – something he has yet to prove to me, but that's another issue entirely – who would need account details… knowing full well that social engineering – which is what it is – would be easier and that was and is his speciality) them of giving out account credentials and then he'd log in to their network, as if he was some brilliant person finding some new kind of exploit. No, no, he was only abusing the weakest chain in the security link: humans. He's admitted it too. Example companies he compromised: Sun Microsystems, AT&T (actually, no, it was Pacific Bell at the time, come to think of it, because he did it after the Ma Bell breakup but before they started getting back together – i.e., he did it the first time in the 80s). I know for sure they – like all – are told not to give out that kind of information but people ARE GULLIBLE and those with limited experience are NAIVE at best. The sad thing with Mitnick is he was busted and then the fool did it again. He's very lucky to have been in to trouble before 2001/9/11 because the US has made examples of people (e.g., the amount of time suggested for the British man who some years back broke into NASA.. some several decades) and _he_ was made of an example of and a very big example (FREE KEVIN and similar messages were all over the web and other things – like the magazine 2600 Hacker Quarterly – not so much because he was innocent [he wasn't] but because they didn't allow him any evidence prior to the trial, i.e., denied him the right) yet he only got 5 years in federal prison, back then. He was busted the second time in the mid 90s and if I recall he got out of prison in either 2000 or 2001. But that was the example of those days… much much more these days. Even worse is he now teaches others about social engineering and therefore makes money off his lies by teaching others how to convince others of being someone else and needing account info (be honest: how hard is that to do? Exactly: not at all).
Something else you fail to account for: your example of 'stranded in a foreign country' – have you personally seen the FULL mail headers of these mails? If not then you should know that most of those (or many of them) come from Nigeria and yes you can get that information by the headers (because well, they're just scammers, they aren't exactly doing anything brilliant unless you consider taking advantage of others brilliant). I've seen phishing attacks and I've had others forward headers to me because they wanted me to give them more info on the origin. So yes, I know that you can trace scammers. Many of the mails claiming to be from US agencies are in another country. Further, and perhaps ironically, many of the ones where they want your bank info (so they can give you money you supposedly are being given) can be traced to Nigera in some form another (not only by full headers but also by including contact information that refers to Nigera or whatever country – usually Nigera though – in the mail itself!).
The bottom line is you should be questioned about "what does assuming do?" because this is quite widespread and even though some _could_ be victims of phishing attacks, it is unlikely all are and besides that, unless you personally have the full story (and I would suggest even AOL doesn't have the full story, as sad as that may be) then you're only making an assumption that it is phishing. Even my post about hotmail having a similar issue is not to suggest it IS that (especially absolutely) but more of similar problems have happened to other companies before. Also, I do wonder (but again I cannot know since I'm fortunate enough to not know anyone on AOL) how different the headers and more specifically the X-Originating-IP (and similar) headers are per mail (by account and overall).
This has been a nightmare! We've run every anti-virus program several times, paid to upgrade our anti-virus programs, changed my password several times and still having problems!! I also receive several undeliverable notices to accounts I'm not familiar with. I thought it was interesting that I deleted several people from my contact list after several emails were sent to my contacts, and then the next day another spam went out to my contacts and INCLUDED THE DELETED CONTACTS FROM THE DAY BEFORE! Since I have another one of my email addresses listed in my AOL contacts, I can see who all receives these emails. Someone has my contacts and they're sending these!! I did disable my AOL account on my iPhone, and I'll see if that helps.
Just a tip to hopefully help you be less 'frantic' (whatever word you feel fits you, use that): My guess is that some of these mails are sent out while none of your devices are connected and logged in. Is this correct? Even if not, read this, if nothing else for your own sense of morality/whatever. Otherwise, if it is the case that none of your devices are on (I won't get into checking mail per device…), then it is not likely (think about it: how could it be related to your system if it's not even on and logged in?) malware (and even if you have a device connected and logged in, it does not mean it IS a problem on your end) and so while it is good to keep up to date, – and this is REALLY IMPORTANT – you are to be commended for trying to stop it (and very much so: you are just a user and yet there are administrators who do not care one iota about it and in fact allow mail to be sent from their server[s] by anyone without authentication… knowingly, even, and this is one of the ways – not the only – spam is so widespread.. I mean as to say, open relays are a problem for the issue of spam. Unfortunately, yes, you're right: malware is also a problem but not necessarily directly – botnets… still, notwithstanding sending from a user's mail account, they are ultimately relaying mail and I wouldn't be surprised if spammers with huge botnets actually run such a server for this very purpose.. would be more surprised if they did not – but this is besides the point of you are to be commended for your effort). That being noted, and I hate to suggest this, but this is likely out of your hands especially as you have most likely ruled out other things (and others have too). It is nasty, it is infuriating (I'm sure.. for me I make fun with it when I see how many idiots try to send spam my way or try to use my server to send spam elsewhere.. and it just makes me laugh how idiotic they are… that they succeed elsewhere is bad but nothing I can help) but it isn't your fault (and even if it was malware or your system or … it isn't necessarily your fault but even then you trying to resolve it basically – at least on my behalf as an administrator – redeems that and I don't find falling victim to it such a crime anyway… security is a very complicated thing with so many variables.. even security websites have fallen victim to being compromised).
I have an email address that is currently (as in, forat least a year) being used as the "from" address for lots of spam… Nothing I can do at my end stops it – SPF, DKIM, etc. I just get endless bounces, "out of office", bad-mailing-list-command messages etc. Currently running around ~3900 emails a month…and that's just the bounces! Goodness knows how many are being sent. It even pushed my DNS off a free plan onto a paid service due to the number of lookups. So spam I never even see is costing me real money!
I'd appreciate suggestions on how to stop this …
This is something I wrote about above: how bounces can become an attack themselves, simply by spoofing. Unfortunately you are correct that SPF and DKIM won't stop it if they aren't sending the mail from your mail server (which if they were, you have a problem as an open relay – or equilvalently another problem – allowing it…). Even then, I seem to think that (I'm cloudy here by the way… very tired and been a while since I've seen in my server logs reference to SPF failures), unfortunately also SPF and DKIM are more useful as policies for the receiving server (rather than your own); indeed if a connected party sends mail from host X and host X has a SPF policy that flat out denies (not soft fail but hard fail) the variables, you can then reject (example). If it was soft fail or pass then it is up to what you configure (of course you could also allow hard fail, I suppose). Reason of course this is this way is well, what can you do about spoofing? Very little with email when the person has a server allowing the crap. However, there's some things that come to mind that might be able to help you:
1. Next time you get a bounced mail, check the headers (full) of the mail (note: if it has attachments make sure absolutely that nothing can be run on your computer, from mail). You're looking for either X-Originating-IP or the bottom Received by line. The main point is you're trying to find the origin (IP or network) and see how small or large it is. If you can sort that out (or have someone help you do it – I would offer if you put it on pastebin or something, obviously masking the email addresses first, but I have a lot going on right now so I cannot promise it.. sorry) then you can proceed to the next step.
2. You refer to DNS which makes me think they're in fact querying your DNS server(s). Okay, so firstly, make sure your SPF policy is correct (and no soft-fail). But let's go with the possibility everything IS OK (and keep in mind with SPF: any A [IPv4] and any AAAA [IPv6] records that should not be sending mail – or in general actually – should have an SPF policy. And keep in mind also that MX records as well as NS records do need A/AAAA records so that means they should have SPF policy too! So do check this as depending on the target/sending server that the spam attempt is going to/from, if something isn't right, this could help mitigate it some). Then, look at 3 as something else to consider (continuation of 1).
3. If you have full access to the zones on your DNS server, what you can do is make use of (I'm using BIND's terminology.. if you use some other DNS software you'll need to find its equivalent) of views. Which is to say: depending on your source IP you can give different information. This is useful in that you can also have internal hosts resolve to different (whether that is internal or not is up to you…) different IPs. It is essentially different access control lists, each with its own rules. You can even have it so you have a PTR record in one view (where authority does not matter) and another view (let's say world view) which does not (because you do not have authority). But here's the trick: IF they are in fact querying your DNS (which it seems to be yes, given you mention SPF and also you updated your DNS plan) you create a view for the abusive IPs (if it is multiple IPs and in a netblock, you can add the block instead of a single IP. referring to CIDR notation). Now, while they may still be doing look ups, you can simply return nothing (so they get NXDOMAIN). That has the implication of if they cannot look up the domain (they get no IP) they cannot connect by name, to your server (or check for any hosts etc). If you wanted you could return 127.0.0.1 for their own machine, as an example. Up to you how to do this.
So recap is this:
1. Do make sure SPF is set up correctly, 100%, as that is important too.
2. If you can find the IPs sending spam, you can – assuming they are querying your DNS server – make their requests return nothing (alternatively you can add a blackhole route or add the network to your firewall, and that could be dropping everything from them, no matter what, and not even send a response back). This is of course only part of it (just like 1) and unfortunately there is no fool proof solution (notwithstanding the item after this list, which may or may not work for you).
3. Also make sure it is NOT coming from your mail server. Check the mail log for this. If they are in fact doing this, then if you fix that, then of course the problem is mitigated (at least some of it, potentially a lot of it). This one is really important, actually.
There is one other thing you can do (well, that comes to my tired mind) and this would actually resolve the issue of you getting many mails: change your email address. If this cannot be done then of course that's another issue (and in future: be careful letting mails like postmaster@ being readily grabbed and added to spam lists and also don't use them where you can have something else). You can also (for future) make use of forwarding/aliasing so that if one mail turns bad instead of changing your 'real' mail you change the alias (and now the old alias will not get mail). Of course, this doesn't solve every problem but it is one way to avoid some spam (and you still have to 'send' from the alias rather than the target mail, but that's another issue).
Hope this helps and hope I did not write something incorrectly or leave something out (about to go rest, I'm really tired). I'll try to check this again but if you see this then maybe someone else can also help you with it (your host for example). Actually, that last bit is something to consider: you mention having a host for this. Ask them if they can help you with this. In fact, I would do that first, before the things I refer to (of course, changing your email might be a good idea but the other things might not be the first things to check, if your host can help you, especially if you are paying them, they should be willing to help where they can!).
It seems that I'm 'in luck' with regards to spf failures. Indeed it is a policy for recipients as I seemed to remember. Here is an example in my maillog, seen this morning. More specifically, I'll show the example description from spf's website about what happened (but note: I changed my server name to example.com – which is meant for documentation and similar – and the host involved I changed to example.org). I am _not_ changing the address of the sender (the ip/host address that is) since it doesn't matter and it is not a mail address and neither is it anyone who should be sending mail this way as should be seen as obvious below (I assume it is a customer of an ISP and nothing else). Otherwise, it should be clear as to why this would use DNS. Note also: certain optimisations can be done for SPF or rather stated depending on how you set up SPF you can cause more DNS traffic than necessary!
Anyway, with that noted, here is an example. Again, example.com is the server the user tried to send mail to (my server). I changed the email address (the envelope sender address) to where (note then that .com is me and .org is the supposed sender) the domain of the supposed sender (and I did that because if it in fact _WAS_ a valid email I am not about to allow it to be collected because of ME… that would be irresponsible! Yes, example.org is also used for documentation purposes.) and the rest should be clear:
example.com rejected a message that claimed an envelope sender address of .
example.com received a message from 93-97-107-162.zone5.bethere.co.uk (93.97.107.162) that claimed an envelope sender address of .
However, the domain example.org has declared using SPF that it does not send mail through 93-97-107-162.zone5.bethere.co.uk (93.97.107.162). That is why the message was rejected.
—
See also:
http://www.openspf.org/FAQ/Common_mistakes
Even if you think you know it, I would suggest looking it over again. I might have seen something that I could improve on my end (nothing that is wrong per se but something that isn't necessary, either, which is a waste, if in fact I did make the mistake – have to check my DNS zones).
AOL has had an AOL/AIM-specific email 'virus" since AOL was AOL (I used to work for them). All this is NOT new news. AOL has never cared, and this is part of what took the Mighty AOL down – 7-% of their accounts were compromised when I left that sinking ship way back before they crashed and burned. Your virus software is NOT ever going to find this as AOL is proprietary software. AOL KNOWS THIS and does not care. Repeat! This "virus" goes into your computer and grabs any and all emails off any and ALL your email on your computer, period. It does not have to be ON AOL or AOL addresses. These viruses look for anything with an @ in it. When you delete things off your comp (like some say here that they deleted their contact list…) it is NOT "gone" off your comp. Nothing is ever gone off your comp. It is always kept somewhere, deep in the code that you'd have no idea how to find and wouldn't even have access to unless you were a comp technician. AOL does NOT care and they can NOT fix this. These spam-mail-contact list- things have been out there since time began and there are millions of computer email accounts out there that have been abandoned, forgotten and hacked which will send out this stuff forever. It will never go away. If you are still using AOL you are an idiot. AOL is the trailer park of the Internet, and it is RUN by the hackers. All your info is in INDIA. Use a real ISP and get a real email address.
Hi all,
today I received two similar mails from a friends' yahoo account :)
Same procedure ….
guess you'd been better not to suggest yahoo to Marisa ;)
Verizon purchase AOL and Verizon. This is a legit link with an article explaining the new privacy agreement Verizon put in place. They basically own everything you do and they can keep it form photos to bank financial emails/statements they are selling our damn information.
https://www.komando.com/happening-now/455054/yahoo-aol-and-oaths-new-massive-email-privacy-policy-changes-you-need-to-know-about
Thank you for the guidance.