 When I speak to computer users about the worst malware threats they’ve encountered, many seem particularly rattled by ransomware.
When I speak to computer users about the worst malware threats they’ve encountered, many seem particularly rattled by ransomware.
Threats like CryptoLocker and CryptoWall hold your data hostage, encrypting them and demanding a ransom be paid for their safe return.
In CryptoLocker’s case there’s some good news. A free decryption service was recently launched by FireEye and Fox-IT to help you recover your files after you’re hit by that ransomware strain.
But in the case of other attacks like CryptoWall it will often be too late, as a message displayed by the malware itself makes all too clear:
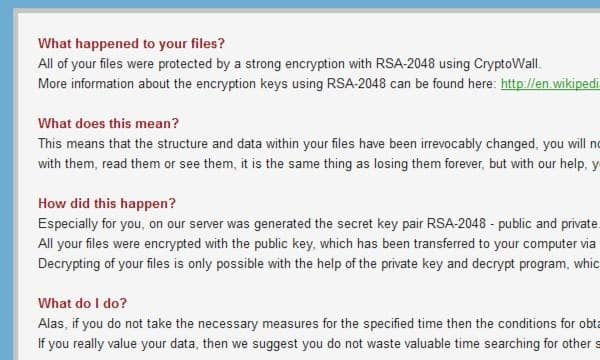
What happened to your files?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall. More information about the encryption keys using RSA-2048 can be found here: en.wikipedia.org/wiki/RSA_(crypto system)
What does this mean?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen?
Especially for you, on our server was generated the secret key pair RSA-2048 – public and private. All your files were encrypted with the public key, which has been transferred to your computer via the Internet. Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed. If you really value your data, then we suggest you do not waste valuable time searching for the solutions because they do not exist.
By the time you see this message, the CryptoWall malware has already encrypted your files and – unless you have a clean backup – you probably won’t be able to get your files back without paying up.
Now security researchers at Blue Coat say that they have seen CryptoWall being spread via ads.yahoo.com – a major online advertising network run by, yes you guessed it, Yahoo.
Innocent computer users click on an advert served up by ad networks, which takes their browser leapfrogging from website to website, until they eventually arrive at a server containing an exploit kit designed to infect the PC with CryptoWall.
“What looked like a minor malvertising attack quickly became more significant as the cybercriminals were successfully able to gain the trust of the major ad networks like ads.yahoo.com,” said Chris Larsen of Blue Coat Systems. “The interconnected nature of ad servers and the ease with which would-be-attackers can build trust to deliver malicious ads points to a broken security model that leaves users exposed to the types of ransomware and other malware that can steal personal, financial and credential information.”
Obviously it’s important to keep your computer protected with anti-virus software and web-filters, and ensure it is up-to-date and fresh with the latest security patches to reduce the chance of it carrying a vulnerability that can be exploited.
But another potential way to protect yourself is to install an ad blocker like AdBlock Plus in your browser so you don’t see any ads in the first place.
Of course, such an approach doesn’t necessarily help ad-supported websites, and means that you won’t see the vast majority of ads that are not designed to infect you.
 This isn’t the first time that Yahoo’s ads have been tainted by the stench of malvertising.
This isn’t the first time that Yahoo’s ads have been tainted by the stench of malvertising.
In January, for instance, Fox IT reported that visitors to Yahoo’s website were bombarded with malicious adverts that attempted to infect computers with a wide array of financially-motivated malware.
Later in the same month, there were claims made that Bitcoin-mining malware had been spread via Yahoo ads.



Another option is 'noscript' which also catches XSS, clickjacking and many other attack types. It isn't necessarily for those who are easily frustrated. The reason is that it absolutely will break many sites because unfortunately too many sites use scripts. It wouldn't be as big of a problem except that often times scripts refer to remote hosts which means you temporarily allow all scripts on the site, you then reload and you have to do it again. Sometimes this happens more than once. But it is worth it if you hate ads and don't want the risk of scripts (or don't like them, like me). At the same time, you add to the whitelist. If you for some reason want to enable scripts globally for a moment (but you should only do that temporarily) you can do that too. Caution here: think of text forms for posting a message. Be wary and save it in a text file temporarily until you are familiar with the scripts (this also goes for another source of lost input: logged out after idle time). Because that is indeed frustrating.
There's one other bonus here with this plugin: once your whitelist is created, what happens if there is a phishing attempt? You can catch it by the fact the site that SHOULD be whitelisted is now not. Granted a site change (scripts for instance) can make it more tricky (so you always have to be aware and do not take it as a 'the site no longer functions, it must be trickery' but I would argue the concern it might add to some isn't a bad thing as it makes them stop and think for a moment). It will show 'Scripts Partially Allowed' and similar messages, to know where you are with respect to the site. More options as well.
As for ads, Yahoo or not? The only surprising part is it isn't as frequent as it is.
Article states "Innocent computer users _click_ on an advert served up by ad networks"
Are you sure clicking is necessary? From what I've seen malvertisements exploit browser/plugin vulnerabilities automatically, with no user interaction required.
In terms of avoiding this problem, the browser addons AdBlockPlus/Edge are a good band-aid to block annoying/dangerous ads, but the only real solution is to use disposable environments to do one's web browsing, as Qubes OS achieves with its Disposable Virtual Machines (DVM) feature. Get infected as much as you want, as soon as the browser shuts down – poof! – the whole DVM is gone for good. Next click to launch Firefox creates a new DVM, from a clean slate.
Good point.
It wasn't clear from Blue Coat's press release, but if the adverts displayed by the Yahoo Ads network were – for instance – Flash-based then that would be another way to potentially infect computers with no clicking required.
Aside from your suggestion, users might choose to disable Flash or use a plugin like NoScript as an additional level of protection.
Yes, NoScript would stop it – and then some. But it isn't for the easily frustrated, as I pointed out. However, for those willing to go for it, it blocks a lot more than flash, javascript, java, … it blocks many other attacks: clickjacking, xss attacks, the list is quite large beyond that. I suggest that anyone willing to work on creating a white list (or even better is not having a problem with always temporarily allowing scripts from site site X, Y or Z) get it. It is a very nice plugin to Firefox. You could call it the inverse of a web application firewall: instead of server side it is client side. I admit that I don't like that use of firewall, but it is what they call it and it isn't exactly relevant. The only relevant thing is it stops scripts dead in their tracks. The breaking of scripts is a security gain but also can adversely affect websites that are safe. The real problem is that scripts refer to other scripts on remote hosts and unfortunately some remote scripts might do that themselves, which means you have to temporarily allow a script, reload, then notice another script is available if unblocked.
Thanks for the tip! Did not know of DVM. One of the machines on my local network could use this feature for sure. Others arguably could too but with noscript and other protections, I'm less concerned (specifically: one is a server = no gui or webbrowser and the other is my own which is quite restrictive as well).