Am I surprised by the suggestion that Russia might have hacked into the DNC to mess with Hillary Clinton’s chances of becoming US president? No, of course not. That would be entirely plausible.
Just as you wouldn’t be surprised to uncover that the United States might have tried to meddle with elections in other countries.
All that’s changed is that we’re all trusting our sensitive information to computers these days.
No, what surprises and disappoints me is the FBI’s failure to warn the DNC effectively of the seriousness of just what was going on.
As the New York Times reported earlier this month, the FBI initially reached out to the DNC via telephone:
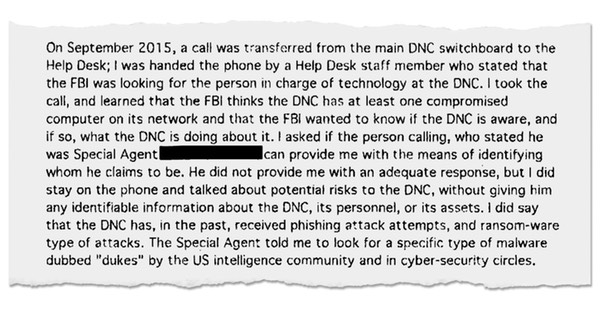
Mr. Tamene, who reports to Mr. Brown and fielded the call from the FBI agent, was not a full-time DNC employee; he works for a Chicago-based contracting firm called The MIS Department. He was left to figure out, largely on his own, how to respond — and even whether the man who had called in to the DNC switchboard was really an FBI agent.
“The FBI thinks the DNC has at least one compromised computer on its network and the FBI wanted to know if the DNC is aware, and if so, what the DNC is doing about it,” Mr. Tamene wrote in an internal memo about his contacts with the FBI He added that “the Special Agent told me to look for a specific type of malware dubbed ‘Dukes’ by the U.S. intelligence community and in cybersecurity circles.”
Part of the problem was that Special Agent Hawkins did not show up in person at the DNC. Nor could he email anyone there, as that risked alerting the hackers that the FBI knew they were in the system.
Mr. Tamene’s initial scan of the DNC system — using his less-than-optimal tools and incomplete targeting information from the FBI — found nothing. So when Special Agent Hawkins called repeatedly in October, leaving voice mail messages for Mr. Tamene, urging him to call back, “I did not return his calls, as I had nothing to report,” Mr. Tamene explained in his memo.
Yup, the DNC stopped returning the FBI agent’s calls.
At that point, wouldn’t it have been worth the FBI popping around to the DNC’s offices if they weren’t returning their calls? How much effort would that have been? One imagines that they would have been able to convince the DNC pretty quickly that they really were the FBI then…
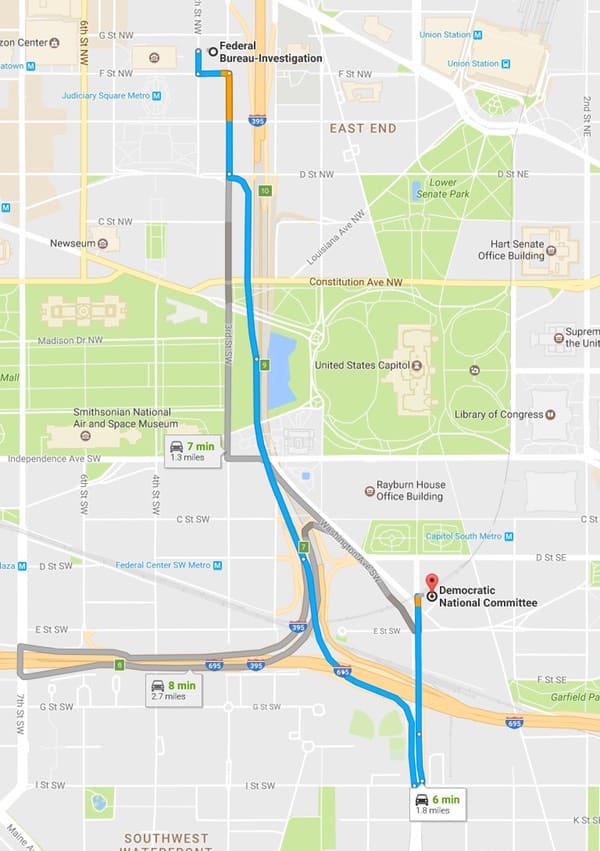
According to Google Maps, it’s about a six minute drive from the FBI to the DNC’s Washington DC headquarters. Or 25 minutes (just over a mile) if you fancy a gentle stroll, which would leave you enough time to pick up some donuts on the way.
Seems to me that I go to more effort when I fix relatives’ computers than the FBI goes to protect a front runner in the US presidential election.



So the FBI calls you tells you've been hacked and that you're at risk. You run your norton antivirus and determine that it's a big waist of time? Then when he calls you back your ignore him. And then you want to blame the FBI for this?
I'll accept that Russia hacked into DNC, and anywhere else they can get into.
The FBI's response was inexcusable, so was the DNC's… didn't they call the FBI and ask for the individual for confirmation?
How does hacking influence the election?
I don't care who hacked (I suspect many hacked DNC, Hillary, Trump, etc.). I want to know who leaked the information!
What is, or should be, of concern is that the FBI is monitoring the DNC. How else would the FBI know?
But what is troubling is: "If the FBI is monitoring the DNC why did it not take action for illegal actions by the DNC".
Our concern shouldn't stop there. What other organizations and businesses has the FBI invaded?
George Orwell would have been proud. His 1949 prediction was off by a mere 30 years.
There is no inference to be made here that the FBI was monitoring the DNC. It is much more likely that they were monitoring known attackers (or the NSA was and referred the incident to the FBI).
There is no inference to be made here that the FBI was monitoring the DNC. It is much more likely that they were monitoring known attackers (or the NSA was and referred the incident to the FBI).
You could rename this article "DNC takes no action after being warned of Hacks". Additionally you could include the entire body of the article and I would suggest the FBI did all that they would be expected to do in those circumstances.
This report fits nicely with the Comey last-minute revelations about emails they from Clinton that they found in the Anthony Weiner investigation, e-mails, incidentally, which amounted to nothing. At that time, at least one commentator asked why Comey did this, intimating that he was given bad information by some of his staff, who in turn, got bad info and lousy advice from various agents, who the commentator said specifially, hate the Clintons. Thus, this lackadaisical approach to telling the DNC that it had been hacked doesn't surprise me in the least.
Comey more or less had to do something to prevent the worse case, which almost certainly would have occurred, in which the fact that Anthony Weiner's laptop contained thousands of Huma Abedin's email messages, some of them related to State Department business and probably some of them to or from Clinton's unauthorized email server. His first memo made no "revelations" at all beyond the bare facts, and the second cleared the air, or should have, as far as Clinton was concerned. Abedin, however, might have trouble with any future clearance, as the messages concerned never should have been on her equipment, let alone that of her husband, who had no authorization at all.
From what I can tell, there was a failure on both ends of this issue. It is not at all unusual for IT departments in Federal agencies to receive communications from people claiming to work for law enforcement, intelligence, or a vendor. You cannot simply take them at their word and engage them in detailed conversation. Even doing something as seemingly innocuous as verifying an OS or the existence of a particular host on a network can assist illegitimate callers in footprinting and enumerating your infrastructure in preparation for an attack. So, shame on the FBI for attempting to alert the DNC via a phone call and some voicemails.
That being said, the contractor failed at performing a proper follow-up. Even without confirmation of the caller's identity, any report received regarding a threat to your systems should be taken seriously and escalated to the proper personnel. From the NY Times article, it appeared the contractor took some cursory steps to verify the FBI's claims, but dropped it when he found no evidence of an intrusion. However, the article also noted that the contractor was not a security expert, so he wouldn't have known if his scans were thorough enough to uncover the suspected malware.
Ultimately, the blame still lies with the FBI. They should have realized they were dealing with someone who was either unknowledgeable in cybersecurity or simply unwilling to pursue the issue – an incredibly common occurrence in the world of IT – and they should have sent a representative to the DNC to initiate an investigation through someone willing to take the threat seriously.
Sometimes Password Boss doesn't work for certain apps, or at least, I can't get it to work. In that case an easy way to generate unique passwords is to steal numbers, symbols, and letters from my bar coded snail mail or purchased products and change something around.
I'm really struggling to understand why the IT guy didn't just phone the FBI's publicly listed switchboard number from a trusted phone (e.g. his own mobile) and asked to be transferred to the Special Agent.
Seems like the IT support team have quite a few questions to answer.