
As the New York Times reports, the United States is kicking out 35 Russian intelligence operatives (a more diplomatic way of saying “spies”), seemingly in retaliation to Russia’s alleged involvement in election-related hacking.
Nobody seems to be suggesting that the 35 people being expelled were involved in the hacks themselves, or that two “recreational facilities” allegedly used for Russian intelligence activities and now being shut down were control centres for the attacks, but I guess in the international world of diplomatic skullduggery that doesn’t matter very much.
This is just another sign that relations between the United States and Russia have become ever more frosty since Hillary Clinton’s campaign for the White House was seemingly disrupted by overseas actors.
Unsurprisingly, the Russians are less than impressed by the decision in the dying days of the Obama administration. Russia’s embassy in the UK, for instance, didn’t mince its words.
President Obama expels 35 ???????? diplomats in Cold War deja vu. As everybody, incl ???????? people, will be glad to see the last of this hapless Adm. pic.twitter.com/mleqA16H8D
— Russian Embassy, UK (@RussianEmbassy) December 29, 2016
Miaow!
In parallel with the expulsions, the FBI and US Department of Homeland Security has released a joint analysis report into “Russian military cyber activity”.

The report implicates the Fancy Bear (also known as APT28, Sednit, Sofacy or Pawn Storm) and Cozy Bear (also known as APT29 or The Dukes) hacking groups, who are widely believed to have close links to the Russian authorities, for a series of attacks that used spear-phishing techniques to grab the login credentials of unsuspecting targets or tricked victims into clicking on links in malicious emails which have infected computers with spyware.
But if you were looking for the smoking gun that directly links the political hack attacks to Moscow, you’ll be disappointed. Reliably attributing an internet crime to a particular country, let alone an individual or hacking group is notoriously complicated.
For instance, an infected computer might be commanded to upload stolen data to a server based in Russia. But what’s to say that that Russian server isn’t itself under the control of hackers in an entirely different country who are covering their tracks? It’s hard to put a water-tight case together unless you have the “boots-on-the-ground” willing assistance of local law enforcement to properly investigate if an overseas computer is itself acting as a proxy for someone else or not.
Now, I’m not naive.
If you ask me do I believe the Russians hacked the DNC or duped Hillary Clinton’s campaign chief John Podesta into handing over his Gmail password, I would have to answer yes, I think they probably did.
But that’s a very different thing from proving it.
So, if we can’t use the released report as evidence that Russia was keen to use hackers to meddle in the US election, what can we learn from it?
Well, there is still useful information and advice in there – both for regular users and organisations who might find themselves unwitting participants in a cybercriminal plot.
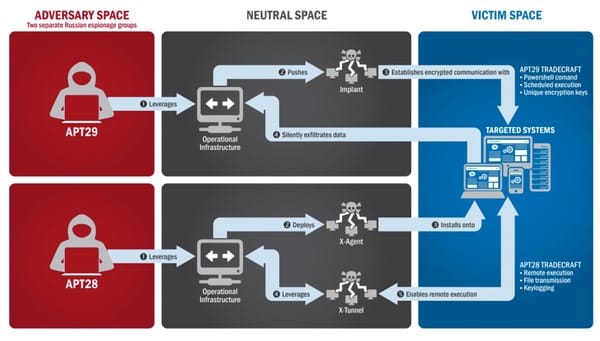
As the report explains, Fancy Bear/APT28 and Cozy Bear/APT29 have well-established modus operandi:
In summer 2015, an APT29 spearphishing campaign directed emails containing a malicious link to over 1,000 recipients, including multiple U.S. Government victims. APT29 used legitimate domains, to include domains associated with U.S. organizations and educational institutions, to host malware and send spearphishing emails. In the course of that campaign, APT29 successfully compromised a U.S. political party. At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware. APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.
In spring 2016, APT28 compromised the same political party, again via targeted spearphishing. This time, the spearphishing email tricked recipients into changing their passwords through a fake webmail domain hosted on APT28 operational infrastructure. Using the harvested credentials, APT28 was able to gain access and steal content, likely leading to the exfiltration of information from multiple senior party members. The U.S. Government assesses that information was leaked to the press and publicly disclosed.
In short, the hackers were helped by weak security on legitimate websites. If your web server, and the software running on it, is not properly secured and patched then there is a danger that a hacker will plant a malicious file on it and then direct their targets to visit what appears – to most users – to be a completely trustworthy legitimate site.
In other words – you and your company may not be the target of the hackers, but hackers could still be exploiting your poorly maintained website to dupe and steal from others. Be a responsible member of the internet community and ensure that your website and servers have the best security possible to prevent you from unknowingly assisting criminals from hacking others.
Furthermore, the report makes clear that too many people continue to fall for phishing attacks which trick you into clicking on a link to reset your login credentials, only to take you to a bogus lookalike site designed to steal them from you.
That’s precisely what happened to John Podesta, leaving his Gmail account wide upon to hackers, who subsequently shared the archive with Julian Assange’s WikiLeaks to publish for the world to peruse.

The US government’s report may not contain convincing incontrovertible evidence that the election-meddling hacks were orchestrated by Vladimir Putin’s Kremlin, but it does offer some sensible advice about steps that can be taken to reduce the chances that you will be helping APT28 and APT29 orchestrate their next hacking attack.


Graham, First let me begin by saying I almost always love and agree with most of what you publish. The headline of this article however, looks suspiciously like a typical liberal rag here in the United States.
First off, there is no hard evidence that the DNC was compromised, whether or not by the Russians. That information certainly could have been leaked by anyone within the DNC. The liberal media as well as government offices currently friendly to the Obama administration are suggesting there was a "hack" of the DNC and our election. This just isn't the truth. The truth is that information was leaked regarding the Clinton's that suggests improprieties at the least and criminal activities at the worst. THIS was the reason the election was not won by Hillary Clinton, not any supposed meddling / phishing activities by the Russians to garner information. And again, there is zero evidence supporting the Russians did anything at all.
Let's be clear here. There was NO "hack" of the USA election process. I'm tired of our majority liberal media suggesting this, and I'm appalled you have joined the headline grabbing group by doing the same, Graham.
Dave, please state what qualifies you specifically to know that there was "NO" hack. What inside knowledge do you possess to back up your statement?
It's head in the sand, people like yourself Dave that make it easy for hackers. You deny that this is possible, and that it is made up by the media. Well Dave what makes you an expert? What's your background in security?
He didn't deny that it was possible, only that the story being told is untrue. The relevant expert knowledge here is that of formal logic, which says contentions must be proven by evidence, not maintained to be true until they are disproven. As Graham says, the evidence doesn't prove anything. There is also evidence to the contrary, Julian Assange and others involved have said that the Democratic party emails were leaked by a disgruntled staff member.
The more important issue is that the propagandists are blurring the line for those who don't understand hacking. The statement that "the Russians hacked the election" is understood by many in the USA to mean that they interfered with the voting machines themselves, directly falsifying the tallies. There is no evidence that anything like that occurred, but the propaganda effect of "Russia hacked" is working well. If Russia did anything, they only made public some damaging emails. The real damage was done by the Democrats who wrote the emails and didn't secure them.