 Adobe has released a new version of Flash Player, and it’s important that everyone with a vulnerable computer applies the update at the earliest opportunity.
Adobe has released a new version of Flash Player, and it’s important that everyone with a vulnerable computer applies the update at the earliest opportunity.
Adobe Flash Player 14.0.0.145 helps mitigate a security threat highlighted by Michele Spagnuolo, a security engineer at Google.
In a blog post published today, Spagnuolo describes Rosetta Flash – a tool which he says can convert any .SWF Adobe Flash file into one composed entirely of alphanumeric characters.
Normally, of course, .SWF Flash files are binary. So, a working Flash file which consists only of alphanumeric characters (A..Z, a..z, 0..9, etc) might not be properly intercepted.
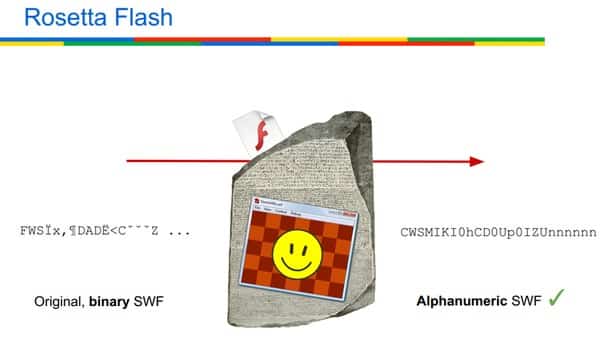
Spagnuolo sums up the threat as follows:
To better understand the attack scenario it is important to take into account the combination of three factors:
1. With Flash, a SWF file can perform cookie-carrying GET and POST requests to the domain that hosts it, with no crossdomain.xml check. This is why allowing users to upload a SWF file on a sensitive domain is dangerous: by uploading a carefully crafted SWF, an attacker can make the victim perform requests that have side effects and exfiltrate sensitive data to an external, attacker-controlled, domain.
2. JSONP, by design, allows an attacker to control the first bytes of the output of an endpoint by specifying the callback parameter in the request URL. Since most JSONP callbacks restrict the allowed charset to [a-zA-Z], _ and ., my tool focuses on this very restrictive charset, but it is general enough to work with different user-specified allowed charsets.
3. SWF files can be embedded on an attacker-controlled domain using a Content-Type forcing <object> tag, and will be executed as Flash as long as the content looks like a valid Flash file.
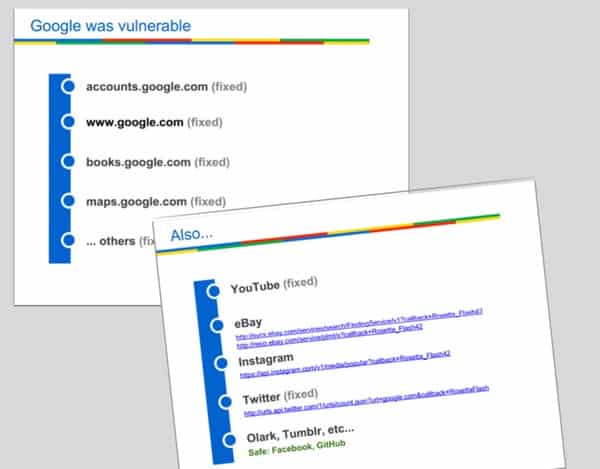
According to Spagnuolo, many popular websites were vulnerable to exploitation using the method including Google sites (who he initially informed) as well as the likes of Twitter and Instagram.
As well as informing Google of the threat (and helping them co-ordinate a fix on their own vulnerable sites), Spagnuolo also informed Adobe’s security team who have now released an updated version of Adobe Flash Player which performs stricter validation checks to reject malicious content from vulnerable JSONP callback APIs.
One of the websites which was found to be at risk was Twitter, one of whose security engineers ruefully admitted that their weekend had been ruined as they had rolled out their own fix for the problem.
@mikispag @twittersecurity yeah you kinda ruined our weekend tho :)
— berk d. demir (@bd) July 5, 2014
Instagram, eBay and Tumblr are said to still be vulnerable, although another website that many would be concerned about – Facebook – is said not to be at risk.
The latest version of Adobe Flash Player can be downloaded from Adobe’s website or – depending on your setup – you might be automatically notified that the update is ready to install.
By the way, be careful not to download McAfee Security Suite which Adobe’s website attempts to foist on you at the same time as you download Flash Player. It’s the kind of dirty trick that you would expect from a scam site, and it’s always disappointing to see the likes of Adobe and McAfee attempting it too.
Users should always have to opt IN to downloading additional software – even if it is from a reputable security firm like McAfee – not have to opt OUT.
Spagnuolo, who has previously found security holes in Google, Twitter, Yahoo, Nokia, Opera, eBay and the Dropbox-owned Mailbox app, will present his Rosetta Flash research in October at the Hack In The Box conference in Malaysia.



Ok, this explains my problem. I am trying to publish to a .swf to Flash Player 14, but in my export settings the latest version I can target is 11.8. Crap!