Passwords are ubiquitous in the information age. We use them every day to sign into our web accounts and devices. As such, passwords help secure our digital lives.
Well… sort of.
Notwithstanding their widespread use, passwords are inherently insecure because they are only information. They are not tied to any physical object. Attackers can therefore steal a password from a vulnerable database (or from the Post-It note on your desktop), or they can purchase a tool that allows them to brute force their way into your account.
It is in response to the shortcomings of password security that we have discussed in recent articles how to add an extra layer of protection to your web accounts.
After covering the difference between two-factor authentication (2FA) and two-step verification (2SV), we explored how to protect a Google account with 2SV, including via the use of the Google Authenticator app.
We then moved on to protecting Twitter and Facebook accounts with two-step verification.
 For argument’s sake, let’s say you access your online accounts from a MacBook Pro or an iPhone. Those devices require an Apple ID to use iTunes and other features, to install updates, and to unlock the screen, if you so choose. That single set of credentials is central to a user’s experience across all Apple devices.
For argument’s sake, let’s say you access your online accounts from a MacBook Pro or an iPhone. Those devices require an Apple ID to use iTunes and other features, to install updates, and to unlock the screen, if you so choose. That single set of credentials is central to a user’s experience across all Apple devices.
I think, therefore, that your Apple ID deserves an added layer of protection. Don’t you?
In this guide, I will show you how you can protect your Apple ID against brute force attacks.
1. Use a web browser to sign into your Apple ID.
On your Apple ID homepage, you will see some basic information about your account, including your email and birthday. You will also see a “Security” section that allows you to change your password, change your security questions, add a rescue email, and activate “Two-Step Verification.” Click on the hyperlinked text “Get Started” beneath that lattermost feature.

2. Apple will prompt you to answer two of your three security questions. Submit the proper answers and click “Continue.”
3. A dialog box explaining how two-step verification works and how it changes your Apple experience will pop up. Click on the “Continue” button.

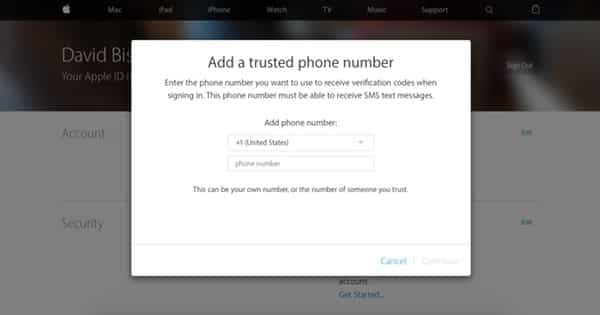
4. Another dialog box will appear and prompt you to enter in your mobile number. Do so and press “Continue.”
5. Apple will send a verification code via SMS to your mobile device. Enter the code into the web browser and click “Verify.”

6. Once you have verified your mobile number, Apple will ask you if you would like to enable verification codes on any device with which you have enabled Find My iPhone, iPod, or iPad. If you would like to activate two-step verification on any of those devices, select the desired devices and go through the setup process. Otherwise click “Continue.”
7. Apple will present you with a recovery key that you can use to access your account in the event you lose your device or you temporarily cannot receive codes to your device. Make sure you write down or print that code and store it somewhere safe before clicking “Continue.”

8. Enter in your recovery key and click “Confirm.”
9. To complete the process, Apple will alert you to several conditions of enabling two-step verification on your account. These include what you will need in the future to unlock your account.
When you have finished reading over the conditions, check the box next to the text that reads, “I understand the conditions” and click “Enable Two-Step Verification.”

10. And just like that, you’re done!

On your Apple ID homepage, you will now see under the “Security” section that Two-Step Verification is labeled “On.” You will also see trusted numbers/devices clearly displayed.
Whenever you attempt to sign into your account from now on, you’ll now come across a screen similar to this one.

Click on a trusted device on which you would like to receive a verification code. This will lead you to a new screen.

In the meantime, you should have received a verification code on the device you selected. Enter that code into your web browser. Apple will automatically verify the code (if correct) and will direct you to your Apple ID account home page. From there, you can enjoy all the benefits your Apple ID affords.
Read more:
- Two-factor authentication (2FA) versus two-step verification (2SV)
- How to better protect your Facebook account from hackers
- How to better protect your Twitter account from hackers
- How to enable two-step verification (2SV) on your WhatsApp Account
- How to protect your Amazon account with two-step verification (2SV)
- How to better protect your Google account with two-step Verification (2SV)
- How to protect your Dropbox account with two-step verification (2SV)
- How to protect your Office 365 users with multi-factor authentication
- How to protect your Microsoft account with two-step verification (2SV)
- How to better protect your Tumblr account from hackers with 2SV
- How to protect your LinkedIn account from hackers with two-step verification (2SV)
- How to protect your PayPal account with two-step verification (2SV)
- How to protect your Yahoo account with two-step verification (2SV)
- How to protect your Apple ID account against hackers
- How to better protect your Google account with two-step verification and Google Authenticator
- How to protect your Hootsuite account from hackers
- How to better protect your Instagram account with two-step verification (2SV)
- Instagram finally supports third-party 2FA apps for greater account security
- How to protect your Nintendo account from hackers with two-step verification (2SV)
- How to better protect your Roblox account from hackers with two-step verification (2SV)



For me, the problem with two-step verification is the addition of a mobile number. I realise there may not be many in my situation, but I do not possess a mobile phone – where I live there is no signal! So what do I do?
One thing you missed when detailing inherent risks with passwords was social engineering. For example when someone rings up apple and they give them the information required. For example Matt Honan.
In this case the target would just be the recovery key.
Tying to a physical device it's possible to take from your posession isn't entirely wise. Something readily spoofable isn't too clever either.
Each device should be independant of access and authentication so compromise of any single device doesn't lead to compromise of all devices. Case in point, Matt Honan. When (cr)apple gave his auth dets to a random third party the first thing they did is wipe his devices and backups – shining example of trust – to keep him distracted and impotent worring about his wifes tablet and all the photo's of the kids whilst the attacker leveraged the fact this apple ID counts as auth on 2FA and then breached non-related systems that had no rights being linked in the slightest.
What are the "benefits" of having an apple ID in the first place again?
That's another set of auth details held by a third party with previous history of dishing it out to randoms?
There's still no true measure of control held by the individual?
It pretends to promote upstream flexability in order to encourage dependance on a system that tracks what what it is used to log into, when, and why?
There's a massive problem with Apple's two-step verification and one I'm surprised wasn't covered in the article. Hidden away in Apple's documentation, which most people don't bother to read, is this:
'If you've permanently lost any two of these items (your Apple ID password, access to one of your trusted devices or your Recovery Key) you can't sign in or regain access to your account. You'll need to create a new Apple ID.'
Put another way: imagine you forget your password and you can't find your recovery key (or trusted device) then you can kiss your Apple account goodbye – permanently! That's right, you lose your whole Apple ID, everything on iCloud, all your purchases and much more.
Activating Apple 2SV can cause you a major headache because it can constantly prompt you to access your trusted device/enter your recovery key. Even more seriously hackers (or anybody with very little knowledge) can remotely lock your account!
"The fact that an attacked account is locked means that a malicious party could even weaponize that behavior into you losing your account access forever if you don’t know where you stashed your Recovery Key. "
http://www.macworld.com/article/2858347/without-your-recovery-key-your-apple-id-could-be-lost-forever.html
THINK VERY CAREFULLY before activating Apple's 2SV; it's not like other companies 2SV.
I agree completely. I used Apple's first version (2FA, IIRC) and that was problem enough. I have computers serving as connection points for IP cameras at properties on three continents. Updating to 2SV would require me to make a trip to each location and change details (or tunnel in, if I left that open).
Like many, I have at least a dozen Apple devices still "live". Old iPads, iPods, etc. I only realize this when Apple tells me I can't access some media *that I have paid for* on a new device because I have *too many*. So I have to figure out which ones to delete. Can't delete all because several of them are geographically remote. Apple *knows* what I have, but won't bother to list them for me
As far as a "trusted device" this always confuses me. Is that my iPad, my iPhone or one of my two Apple laptops? What if none of them are logged in? What if there's no wifi or mobile signal? Pretty shoddy. And *which* one – because the message does not always propagate to all.
Then there is Apple's fast-and-loose terminology. Password, passcode, pin, recovery code. Just stop.
I recently got a new laptop. I tried to "ghost" my old one to the new one but it didn't work (anyone remember when Apple stuff "just worked"? No – too young?) Anyway, I had to reset my single-factor Apple ID *twice* – no doubt Apple saw the failed ghosting as a security issue.
Finally, this had forced me to migrate away from using Apple's Mail platform. I can use Google and Yahoo (through which I access other accounts) via 2SV on many platforms. But Apple will not allow access without 2FA except on their own platform. They *could* write an Android app for Mail, but they appear to be short of resources for such customer service
Careful with http://applesms.co.uk … a new phishing scheme. It's an attempt to hack into your Apple ID to obtain personal information including credit card payment details.
I have reported it to Apple and spoken to an Apple Care advisor.
change your password immediately on http://appleid.apple.com.
Hope this helps.