Researchers are warning of a spammed-out malicious attack that has added virtual machine (VM) evasion techniques, in a bid to avoid detection by anti-virus researchers.
As most of us know, spear phishing is a targeted version of a regular old phishing scam by which an attacker attempts to trick the user into doing something online they should ideally think twice about before doing, such as disclosing personal information, clicking on a link, and downloading an attachment.
Phishing is a form of social engineering. As such, it does not typically rely so much on technical skills as it does on an attacker’s ability to lull their target into making poor decisions.
That’s not to say, however, that attacks cannot incorporate sophisticated features.
Amit Dori, a security analyst with the Check Point Threat Intelligence & Research Team, explains in a blog post how one customer recently received a rather typical spear phishing email:
Like in most other targeted spear phishing campaigns, the attack email contains personal information relating to both the target and the “sender,” including their name and company.
It also has a malicious Microsoft Word document attached, that masquerades as an invoice. If the recipient agrees to enable content (macros), the document – which in actuality is a malware downloader – begins executing all commands within its grasp.
Nothing unusual so far. But here’s where it gets interesting.
When the downloader is first activated, it sets to work collecting information about the system on which it is running. There’s a method to this madness, as Dori notes:
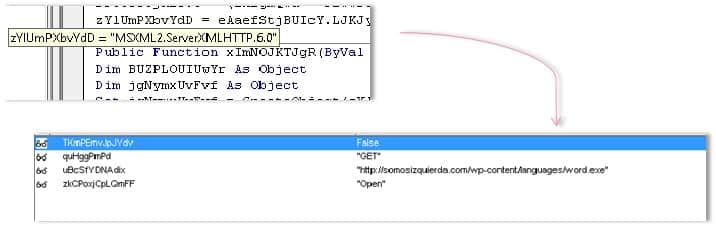
“The dropper tries to evaluate the state of the machine. In this case, the code below is used to check if the document was executed in a virtual environment (i.e. a sandbox) and whether it is running alongside well-known debugging programs.”
If the downloader comes across any strings suggesting VMware products are running on the machine, it shuts down and displays an error. It does the same thing if it detects a number of other processes security researchers might use to detect suspicious behaviour, including “FIDDLER” and “WIRESHARK.”
In this way the malware is attempting to avoid analysis by anti-virus experts. In short, if it believes it is being watched it refuses to perform.
Otherwise, the downloader will reveal its file: “word.exe”. That’s not the real Microsoft Word, of course. Instead, it carries a commonly encountered form of malware known to deliver Locky, CryptoWall, and other threats right to a user’s doorstep.
For Dori, this sophisticated spear phishing campaign serves as a harbinger of threats to come:
“The VM and debugging evasion techniques used are quite innovative. It is not surprising that spear phishing attacks have adopted these tricks, as malware often use such techniques to elude security researchers and fly-by detection of Anti-virus programs. We can only assume their methods will become even more complex and sophisticated in the future.”
Given the persistent threat of phishing campaigns, I’d like to urge users to remember some of the key anti-phishing fundamentals. Those include never clicking on a suspicious link or email attachment, never providing personal information to someone whom you don’t know, and disabling macros in Microsoft Office documents by default.
Be sure to commit those security measures to memory, and above all, if you receive a suspicious email, make sure you delete it and don’t click on anything.





I've seen multiple messages (ransomware attacks) of this type on one of my email accounts, which, for the most part, sets off an alarm in my virus protection software. What I'd really like to see on your site are some articles about how you can block this type of malware. Interestingly enough, I've never received this type of attack on my Gmail account, only on an account which I set up through HostGator.
So would it make sense for antivirus programs to include tasks that run on end user computers that look like the same tasks these attacks are trying to hide from? Either the attack would self abort because it thinks it is being watched or the attackers will stop using this approach since it would no longer be effective for telling the difference between a target machine and one being used by antivirus companies for detecting malware.
No, because not all viruses/malware work this way. It's easier, safer and more effective to just quarantine and delete the virus-ridden file instead of hoping there is code within the program that'll stop it working if it detects a specific user agent string.
Great article. A deeper layer of inbound content inspection and structural sanitization to strip out the macro malware triggers are proving to be the answer.
Commercial systems already use these inspection techniques; they detonate the file in a freshly spun virtual machine in order to analyse it for suspicious behaviour (e.g. macros, registry changes etc.)
https://technet.microsoft.com/en-us/library/mt148491(v=exchg.150).aspx
Yes, but a big theme of David's article is that new malware evades such detection methods that use virtual machines / sandboxes. In addition, the high costs and delay up to 30 minutes might not be acceptable to a number of organizations. Simply automating the removal of the macros and either blocking or letting the rest of the message/attachment to continue unhindered would be the most effective and present the least (if any at all) false positives.
I think you've misunderstood my comment Scott as this isn't how commercial threat detection systems work.
The solutions out there spin a new machine each time on the server-side – to the virus/malware they are 'real' machines and there's no effective way for them to detect otherwise.
Whilst people would refer to this solution as a 'virtual machine' it technically isn't as it's effectively a fresh install on a sandboxed server.
I think you're confusing consumer-grade virtual machines (which are easily detectable) with enterprise-grade virtual machines which actually run on dedicated hardware (so aren't a virtual machine in the truest sense of the word).
The article I referenced goes into the technical details.
I do agree with blocking the macro but that's what Microsoft Office does by default when a file is downloaded from the internet.
Trying to remove a suspicious macro (that might not be dangerous) may be unacceptable to some organisations.
The 30-minute delay is, I agree, not ideal although in practice the delay is around 5-minutes.
With all things security: you have security or you have convenience. You've got to find an acceptable compromise.
Thanks Bob. Here is a commercial threat detection system that does remove the threats without spinning up a new machine. Gaining a lot interest from sophisticated cyber security teams around the world. https://www.clearswift.com/solutions/advanced-threat-protection
This is why I only open suspicious emails on my work computer. My personal machines are sacrosanct.
@Pat McGroyne – and I bet your IT department loves you for that too…
Stupidity has no limits.
An IT Pro.
I think as long as end users don’t pay attention and pay attention to the advice they are given time and time again by professionals. There is always going to a big payday for the new wave of malware\ransom ware creators.