A few days ago I warned Windows users that an unpatched security hole in Microsoft Office was being used by malicious hackers to spread malware.
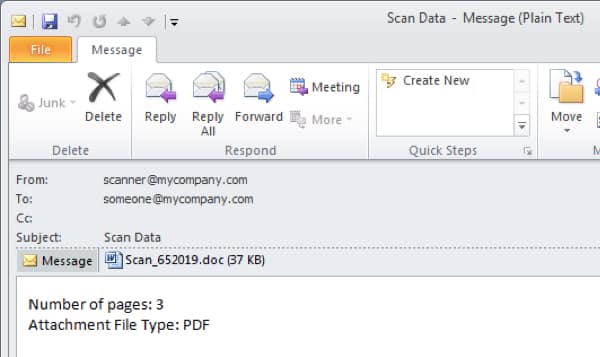
The vulnerability was in all versions of Microsoft Word, and – as researchers at Proofpoint reported – a widespread attack had been seen using it to spread the Dridex malware in emails purporting to have been sent by your company’s photocopier.
The malware attacks were particularly interesting because they did not rely on the now-familiar technique of tricking recipients into enabling macros.
Fortunately there is now some good news, as on Tuesday Microsoft released its regular bundle of security patches – including a fix for the Office zero-day vulnerability (known as CVE-2017-0199).
It turns out that that wasn’t the only zero-day vulnerability fixed by Microsoft in this month’s patch update. An elevation of privilege vulnerability in Internet Explorer (CVE-2017-0210) that would allow an attacker to convince a user to visit a compromised website, was also fixed.
In all Microsoft has released fixes for over 40 unique vulnerabilities, 13 of which are rated “critical.”
Make sure that you have installed the latest security patches at your earliest opportunity. Home users and small businesses may in particular appreciate the benefits of turning on automatic updates.
By the way, Microsoft has this month redesigned the way in which it communicates details of the security holes it has patched – doing away with its familiar security bulletins and replacing it with a new-look Security Update Guide.
Personally, I find the new layout rather confusing to navigate and less than helpful. But maybe that’s just my lack of familiarity with the way it’s designed. I would be interested in hearing readers’ feedback.
Finally, this Patch Tuesday bundle marks the end of Microsoft’s extended support for Windows Vista. The company won’t be issuing security updates for Vista anymore. You have been warned…



"Personally, I find the new layout rather confusing to navigate and less than helpful […] I would be interested in hearing readers' feedback."
I think they've designed it like that deliberately Graham. It's extremely complicated to see at a glance what the vulnerabilities are. Microsoft's email alert service or RSS feeds don't make it any clearer either.
I'm inclined to agree with El Reg's assessment of the situation:
https://www.theregister.co.uk/2017/04/11/patch_tuesday_mess/
This is the same company (Microsoft) who stopped sending out full information to administrators. The lack of information might be fine for home users but for businesses (who need to assess the patches) it's not good at all.
Those tables are awful, even on a large monitor, and make the situation no clearer.
More commentary Graham:
https://arstechnica.com/information-technology/2017/04/windows-admins-what-do-you-think-about-microsoft-getting-rid-of-security-bulletins/
And on the recent Shadow Brokers release:
"What's particularly curious is that four of the exploits — EternalBlue, EternalChampion, EternalRomance and EternalSynergy — were fixed in an update just last month, on March 14th."
https://www.engadget.com/2017/04/15/microsoft-says-it-already-patched-several-shadow-brokers-nsa-l/