 Internet users around the world have been deluged by malicious spam in recent days posing as unpaid invoices.
Internet users around the world have been deluged by malicious spam in recent days posing as unpaid invoices.
The security researchers at ESET have a good write-up on the Nemucod Trojan horse, which is being aggressively spammed out as a ZIP file attachment in order to infect computers with the Teslacrypt ransomware.
The emails have a range of disguises, but typically pose as a demand from a company that you pay an unpaid invoice.
What the criminals are hoping is that you will be so outraged at the thought a company is demanding money for something you never ordered that you will unarchive the attached ZIP file without thinking, and open its contents to learn more.

Unfortunately, inside the ZIP file is a malicious JavaScript file – and opening that could result in your PC running its obfuscated code and install ransomware onto your computer.
Nasty stuff without a doubt.
But what amused me was that the malware spreaders made a mistake – albeit one that probably many potential victims will fail to spot, blinded by the cunning social engineering of an unpaid invoice disguise.
Take a look at the email again.
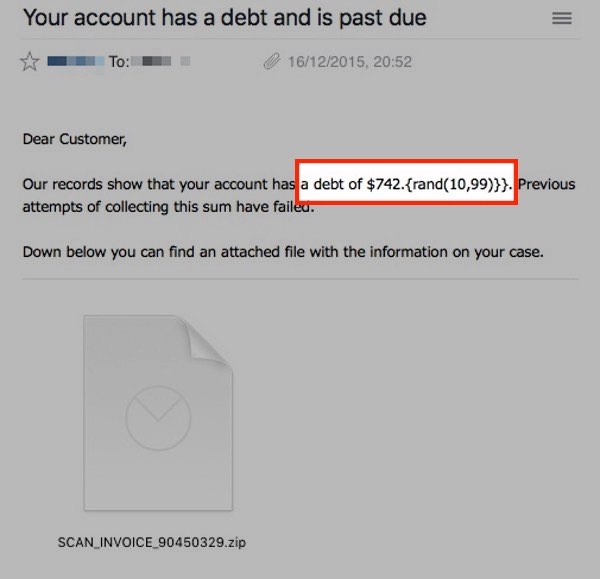
The bad guys have clearly built a template to allow them to quickly adopt different disguises for their malware attack, and in this particular case intended for a random debt to be displayed. But clearly one of the criminals made a finger fumble when coding this particular campaign as their attempts to display a random number of cents (between 10 and 99 cents) failed to work properly!
It’s just a tiny clue that might make some people pause to think before opening the attachment. But the truth is that you cannot rely upon attackers to make elementary mistakes like this all the time.
It’s much better to run up-to-date security software, and always be on your guard over unsolicited email attachments. A little training in the ways in which malware can infect your computer can go a long way to protecting yourself against threats like this.
Being clued up about the dangers is an essential layer of your defence, as the current wave of malware-laden invoices are being rapidly adjusted by the attackers in an attempt to evade detection by anti-virus software.
Be sure to read ESET’s blog post to learn more about the threat.



And it's circulating in the UK…part of today's spam 17-17-15
It got to your date.
Wouldn't it be nice if there was some sort of software you could get, that would block this sort of thing.
There is. It's called Spanarrest. It isn't free but I've been using it for years. Any incoming email that is not from anyone in your address books is diverted and "junked". It never even gets to your machine.
I have gone to Spamarrest to have a look at what I waen't receiving and there were dozens of these fake bills that I never knew were even sent.
Alan,
There is such a tool; Naive Bayes, specifically POPFile from John Graham-Cumming link: http://getpopfile.org/
You simply train it what email malware looks like (on-the-fly) and it can then flag emails as having malicious attachments and/or links, etc. Same with any other material you want classified; spam, scams, geocaching related emails, and so on.
Not bad for a theorem that was written over 300 years ago by a theologian.
Works on Linux, Mac and Windows.
Normal working spam filters will mitigate this. I was running my server without my spam filter (just turned it off to see what comes by) Simply turning on greylisting again was enough to stop this.
I have no idea why people are still getting this kind of shit.
ISP's can easily mitigate this, and a lot of other dangers coming in via email. But somehow they don't. And as long as they don't this will never end. No matter what standards we introduce on SMTP.
I use something similar, which is also written in perl. But instead of "training it" to recognise malware, I just put everything with a potentially malware attachment, into the "suspicious" place. The problem is, "invoice attached" isn't going to be suspicious for many people.
What would be better, is something that removed macros from the doc files, and similar actions for other potentially malicious files.
Alan,
Have a look at EXEFilter, is may do what you require and I seem to remember that you can even use it as an in-line mail filter on *NIX…
http://www.decalage.info/exefilter
Good puns.
And when I saw the error I originally thought maybe those documenting it were showing the intention. To think it actually prints that is much more amusing. Of course, it's not the only stupid errors malware authors have made and it won't be the last either. Yet it's indeed a good reminder to run up-to-date software and also to backup regularly.
There is a way to stop all of this foolishness (and all SPAM as well). I've been using it for years. It isn't free but it's called Spamarrest. When it is in place and incoming email that is not from anyone in your address books is routed to the Spamarrest servers and never gets to touch your machine. You are still able to go to your account in Spamarrest and have a look at all of the junk mail that it threw away over the last seven days. No fake bills no SPAM, no junk email of any kind. It's peaceful.
Really Herman … you want to leave it up to your ISP to determine what items should or should not reach your inbox?
And from the ISP's perspective – why would they want to have responsibility for something else that they know will sooner or later really piss you off.
I have had ISP's set by default to catch spam. I found some friends of mine ask me why I didn't respond to their emails. My ISP was rejecting them as spam.
Best solution I found is have two emails. One I call a throw away that I use for all those signup things. All the spam goes to that address. Another email address I use as primary which rarely receives any spam, maybe 3-4 a year.