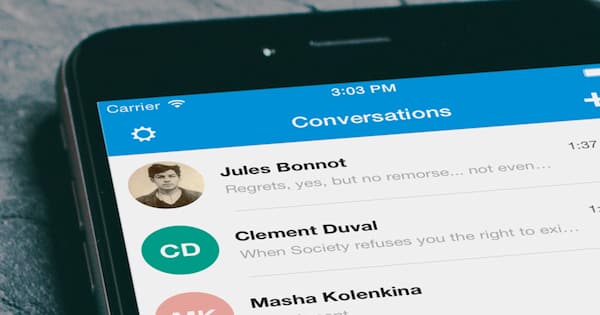
Open Whisper Systems, the developers of encrypted messaging app Signal, got hit by a US government subpoena asking the firm to cough up any information they had on accounts associated with two phone numbers.
A gag order was put on Signal’s makers, preventing them from going public about the US government’s demands for private data. After a legal fight that gag order has now been lifted, revealing…
…well, not revealing that Open Whisper handed over masses of private information about some of Signal’s users, but instead that because the firm – by design – keeps so little data about its users and their communications, it was unable to produce anything of much value.
The American Civil Liberties Union, who represented Open Whisper in court, explains:
As the documents show, the government’s effort did not amount to much—not because OWS refused to comply with the government’s subpoena (it complied), but because the company simply does not keep the kinds of information about their customers that the government sought (and that too many technology companies continue to amass). All OWS was able to provide were the dates and times for when the account was created and when it last connected to Signal’s servers.

The only data Signal was forced to hand over was the date the account was created, and the date it was last used (and even then it was presented as the number of milliseconds since the UNIX epoch – January 1, 1970 00:00:00 UTC).
For many companies it could be quite damaging to reveal just how much data about its customers it had to share with the authorities. With Signal it’s a victory. Privacy wins.
There’s a simple lesson here. If you don’t keep the data in the first place, hackers can’t steal it from you, and governments can’t demand it from you.


Some guy in a tent in Yemen is fist pumping with one hand and soldering with the other. Or maybe it's a pedophile. Who cares right? Privacy trumps all. Hooray for not tracking activity and not allowing anyone, including law enforcement with a subpeona, from getting up in our business.
Wow, you're basic cable. You must be one of the idiots that thinks the government does no wrong. Let me guess, you have nothing to hide so you don't care about privacy? if that's the case, feel free to post your email account login and password. I mean, you have nothing to hide right? nitwit.
Specious reasoning FTW. Would you want a world where the proper authorities can't get access to any communications at all? It would be a nasty, brutish and short existence for us all. How many Orlando or Paris attacks get stopped before the public ever heard about them?
The reality is that in 2016 LE/government requires at least *some* access to keep people safe. Yes, obfuscation and encryption are great tools for us all. They are also great tools for the bad guy. Where would you draw the line in the sand?
well if law enforcement actually took the time to LEGALLY get their subpoenas, instead of violating our privacy every chance they get, maybe these apps wouldnt be needed
What about the protection these apps afford individuals against cyber criminals?
For most people it's not law enforcement who are the enemy – its criminals, hackers, blackmailers and snoops.
These apps only provide some of the protection we used to have. For example if I sent you a letter via snail mail and some weeks later law enforcement went to the Postal service provider and asked what they knew about me or you then how much could they tell them? Granted we may need to do something looking forward to allow monitoring with a suitable subpoena/warrant but retrospectively these apps only give us the protection we used to have
LE can and do intercept snailmail perfectly legally (at least here in the UK), open it, copy it, and send it on to the bad guy who is mostly unaware.
Indeed and agree, but that's only looking forward. They can't look back in time to see snailmail from before the intercept started. Also they can only intercept mail to somebody. LE have no idea what someone sends unless they has the suspect under surveillance and see which postbox they post mail into