
There is some more good news for those who have fallen foul of ransomware.
Czech security firm Avast has developed decryption utilities for victims of not one, not two, but three different ransomware strains – meaning that victims who have been hit may be spared paying a ransom to their attackers.
The ransomware in question is Babuk, LockFire, and AtomSilo.
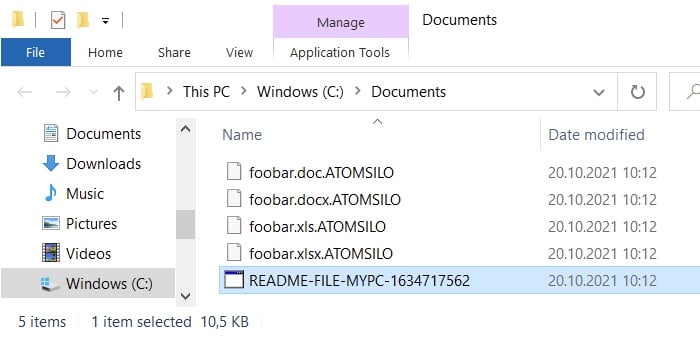
In a blog post, Avast’s researchers explained that their decryption tool tackled both AtomSilo and Lockfire ransomware strains.
Avast also credited malware analyst Jiří Vinopal for his vital role in making the decryption tool possible, after he spent his free time analysing and finding weaknesses in the AtomSilo and LockFile encryption algorithms.
Unfortunately, there are some limitations on what can be decrypted by the tool, as the Avast blog explains:
The Avast AtomSilo decryptor relies on a known file format in order to verify that the file was successfully decrypted. For that reason, some files may not be decrypted. This can include files with proprietary or unknown format, or with no format at all, such as text files.
Nonetheless, the tool is clearly a massive aid for victims of the ransomware who do not have access to clean backups or are unable/unwilling to pay extortionists.
In addition, Avast has also released a free decryption tool for the Babuk ransomware.
Avast was able to create its Babuk decryptor following an analysis of the ransomware’s source code which was leaked onto the internet in September.
According to reports at the time, the Babuk source code was released after one of its developers (a 17-year-old Russian) was “diagnosed with stage 4 lung cancer.”
Avast says that its Babuk decryption tool will work for past victims whose encrypted files had been given the .babuk or .babyk file extensions.


