 Dropbox user Darrell Whitelaw got a surprise this weekend.
Dropbox user Darrell Whitelaw got a surprise this weekend.
He uploaded a movie file to his Dropbox folder, and – during an instant message conversation – shared a link to it with an online friend.
And that’s where the trouble started.
Because the movie was copyrighted, and Dropbox – it appears – is attempting to stop copyright-infringers from sharing files via public Dropbox links.
This is what was seen when the link was accessed:
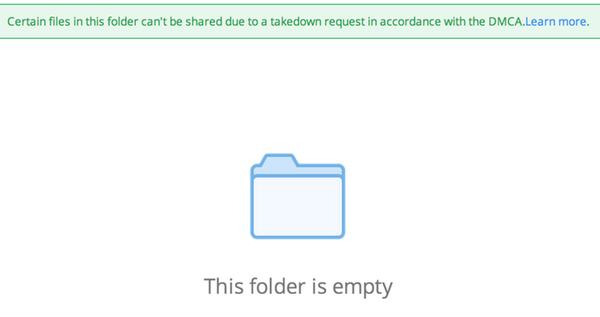
Certain files in this folder can’t be shared due to a takedown request in accordance with the DMCA.
Whitelaw tweeted the screenshot, which was rapidly retweeted by many other Twitter users over the weekend concerned that Dropbox might be snooping on users’ content, and explained:
I treat [Dropbox] like my hard drive, this shows it’s not private, nor mine, even though i pay for it.
The media, understandably, latched onto the story. The folks at Ars Technica reached out to Dropbox, who confirmed that it checks publicly shared links to files, and compares the hashes of shared files to those that have previously been subject to successful DMCA (Digital Millennium Copyright Act) takedown requests.
“We sometimes receive DMCA notices to remove links on copyright grounds. When we receive these, we process them according to the law and disable the identified link. We have an automated system that then prevents other users from sharing the identical material using another Dropbox link. This is done by comparing file hashes.”
There are a few important things to note here.
 Firstly, it doesn’t appear that Dropbox is doing this with all files stored on its data servers. Instead, it only appears to be done for files which are being shared with other internet users via the service.
Firstly, it doesn’t appear that Dropbox is doing this with all files stored on its data servers. Instead, it only appears to be done for files which are being shared with other internet users via the service.
Secondly, the content of the actual files are not being examined. Instead, Dropbox has a database of hashes (checksums, if you prefer) of files that have been previously been identified as copyright material that have been taken down by DMCA requests.
If you share a file with other internet users in a Dropbox folder that has the same hash as one on Dropbox’s list, you’ll no doubt have the same problem as Darrell Whitelaw and his friend.
Finally, the file wasn’t removed from Whitelaw’s Dropbox folder. It was just made inaccessible to other internet users (the public link was disabled, and redirected to the DMCA message).
Whether you consider this snooping or not, is a matter for some debate and argument. But it’s clearly the case that data uploaded to Dropbox is not as private as some might have hoped and imagined.
If you don’t like the idea of your files being examined in this way, you have two choices.
- Stop trusting Dropbox with your files
- Encrypt your files before you upload them to Dropbox
 Tools like Boxcryptor, CloudFogger and SafeMonk provide a seamless way to encrypt your sensitive information before it gets uploaded to Dropbox, meaning the service cannot tell what you are storing in the cloud. Some also swear by open source tools like TrueCrypt to do something similar.
Tools like Boxcryptor, CloudFogger and SafeMonk provide a seamless way to encrypt your sensitive information before it gets uploaded to Dropbox, meaning the service cannot tell what you are storing in the cloud. Some also swear by open source tools like TrueCrypt to do something similar.
Alternatively, the likes of Wuala and SpiderOak offer competing solutions to Dropbox but promise “zero knowledge” of what you’re uploading to their servers. Such solutions have the advantage of having security and privacy baked-in from the outset.
In the case of Wuala, they also make a point of underlining that their data centres are located in Europe rather than the United States, which will be appealing to some.
As with all of these technologies, remember my adage: Don’t call it ‘the cloud’. Call it ‘someone else’s computer’. That really helps you consider the security consequences of what you are doing.
If you have experiences of using alternatives to Dropbox, or have found an encryption regime which works well with Dropbox, please share your experiences by leaving a comment below.



Not at all surprised that they do this. They're trying to avoid another Megaupload scandal. Pretty much all file sharing services do this – at least the ones who aren't dodging it by allowing client-side encryption. The reliance on hashes, however, tends to allow a lot of copyrighted stuff to slip through, so it's mostly a CYA maneuver so they can show in court if need be that they were doing "something" to inhibit file sharing.
Your meme that "cloud" should be "someone else's computer" is excellent.
I thought I would check out Safe Monk to encrypt some of my stuff on Dropbox after reading your article.
I decided to read through the AUP and in section 7 is states:
"Using the Service to encrypt any material that infringes any copyright, trademark, patent, trade secret or other proprietary rights of any third party, including, but not limited to, the unauthorized copying and/or distribution of copyrighted material, the digitization and distribution of photographs from magazines, books, music, video or other copyrighted sources, and the unauthorized transmittal of copyrighted software".
How can they enforce this without looking at your data when it is encrypted?
I've decided to use Truecrypt to encrypt my data as at least I know what I encrypt can't be snooped at.
I don't see a problem if you're sharing copyright material then it's to be expected and their explanation of looking at the hashes seems reasonable.
It's not necessarily copyright material though, just material someone (or some bot) claims is copyright.
BoxCryptor is free for personal use for one cloud provider, as is Viivo (PKWare). I have BoxCryptor working on SkyDrive (OneDrive) and Viivo on Google Drive. BoxCryptor is produced by a German company, Secomba GmbH (and is therefore trustworthy?). SafeMonk appears to work only on DropBox, and has to be paid for.
CloudFogger was last updated in December 2012, which was also the last date of their blog archive. I believe it works, but ongoing support looks doubtful.
Linux has a free solution called EncFS, which seems to work well, and can be combined with BoxCryptor Classic.
DropBox are effectively examining the contents of the files if they are computing hash values. Moreover, there are some natty algorithms for comparing file content with copyright content which can find equivalent content even if you have chopped off the beginning and end of the file – Google's YouTube uses one, as I found out when I uploaded a video that turned out to be copyrighted to a German TV company (ARD), who had effectively put out a DMCA notice to Google. That was discovered immediately after I uploaded it. The process is very efficient; YouTube even shows you which part of your file is the same as the copyright version.
I encrypt my files with Axcrypt before uploading them to Dropbox.