 Many security commentators reacted strongly to UK Prime Minister David Cameron’s stated desire to ensure that there could be “no safe place” on the internet for terrorists and criminals.
Many security commentators reacted strongly to UK Prime Minister David Cameron’s stated desire to ensure that there could be “no safe place” on the internet for terrorists and criminals.
Mandatory back doors, front doors, skeleton keys or whatever you choose to call the more intrusive forms of lawful intercept could never be made 100% secure, resulting in the law-abiding public being put at risk. And open source encryption tools freely available on the internet make it trivial to bypass all but the most draconian controls.
With no sign of the UK Government retreating from the rhetoric, the recently published draft Investigatory Powers Bill was awaited with interest. In the run-up, The Telegraph published apocalyptic predictions of its impact, tweeted to his million-and-a-half followers by Edward Snowden.
5 days ago, I warned UK govt sought to ban strong encryption, despite public denials. https://t.co/jV7uW7tTiO Today: pic.twitter.com/qTNB49EGMF
— Edward Snowden (@Snowden) November 2, 2015
Having spent just a few hours studying the draft Bill my conclusion is that whilst there are areas of concern, it bears little resemblance to many of the more alarmist predictions.
There is no wholesale onslaught on encryption, it includes the very welcome introduction of judicial oversight, and it rationalises a whole rag-tag collection of dated legislation. There’s no way that David Cameron can claim that it achieves his stated objective, but don’t tell him I said that!
Press coverage since publication has focussed almost exclusively on Part 4 of the draft Bill, covering Retention of Communications Data. This, in particular, seems to be what has attracted the appellation of “snooper’s charter”.
 It does indeed allow for the collection of Internet Connection Record (ICRs) by Communication Service Providers (CSPs), but these are strictly limited to the IP addresses or domain names of the endpoints of a communication. So if I browse to bbc.co.uk, that would be recorded, but not whether I was looking for programme listings, the news or the weather.
It does indeed allow for the collection of Internet Connection Record (ICRs) by Communication Service Providers (CSPs), but these are strictly limited to the IP addresses or domain names of the endpoints of a communication. So if I browse to bbc.co.uk, that would be recorded, but not whether I was looking for programme listings, the news or the weather.
Specifically, anything following the slash after the domain name, as well as all content, cookies and browser or webpage metadata are excluded, and will of course be invisible in the case of an https connection.
If a youth on his way to radicalisation visits a known terrorist website, this could be picked up. And it would be equally if he were to visit a porn site. But if his new found hero chooses to hang out amongst boring bloggers at bloggingsite.com/incendiarypreacher, this will ring no alarm bells at all.
The draft Bill provides the power to require CSPs to retain data, but a warrant with judicial oversight is required before that data can be handed over, or for a CSP to assist in targeted interception.
Warrants are required for other forms of bulk data collection and also for the examination of data so collected.
Retention of ICRs is limited to 12 months, after which they must be irretrievably destroyed. Furthermore, procedural and technical controls must be applied to limit access to ICRs to the extent and number of staff strictly necessary.
Special protections are provided for certain professions such a journalists, whose need to protect their sources is recognised.
I’m not saying (as Home Secretary Theresa May has tried to assert) that this is no more intrusive than an itemised phone bill. The number of websites I visit in a day far exceeds the number of phone calls I make, and it’s possible that inferences could rightly or wrongly be drawn from the pattern.
Amongst the Guide to Powers and Safeguards (which precedes the formal draft Bill itself) examples are given of how ICRs would be “invaluable to law enforcement”. Some of these seem hardly credible. One example suggests that it might be useful to know that an individual had used mapping services.
Many of us use mapping services all the time, and there would be no indication in the ICRs whether a subject was familiarising himself with the layout of 10 Downing St for nefarious ends, or the geography of his forthcoming holiday destination for his own personal enjoyment.
It seems to me that the case for collecting ICRs has not been convincingly clinched. If there is indeed a case (and the spooks are famously reluctant to discuss anything about their methods), then it could be made more palatable by reducing the retention time to six, or even just three months. I suspect that the events on the path of a disillusioned youth’s journey into radicalisation are often swift and ephemeral, and that it may often take much less than a year to turn the corner.
The costs to an ISP of storing 12 months’ communications data may not be insignificant, and the implication is that these costs must be borne by the ISP. No doubt they would have to be passed on to users. There is at least a requirement for “feasibility and any other impact” (presumably including cost) to be considered.
But would it not be better to require CSPs to pay for access as they used it? At least this would encourage authorities to look closely at the need, rather than simply requesting data just because they could.
One concern with this part of the draft Bill is that there is no tight definition of a CSP. It obviously includes ISPs, but does it extend to VPN providers, or to Skype, Facebook, messaging apps and email services, all of which provide communications services? If so, few of these might wish to operate from the UK.
The draft Bill recognises the limitations of its jurisdiction. Extra-territorial entities are required to “have regard to” its requirements but cannot be compelled to comply.
So much for Retention of Data, but why I really wanted to examine the draft Bill was to see what it said about encryption, and how this matched up to some of the predictions. What I found was – wait for it – almost nothing!
Reassuringly, the Guide to Powers and Safeguards clearly states that there will be no additional requirements in relation to encryption beyond those in the existing RIPA legislation, which it defines as requiring CSPs to “to maintain permanent interception capabilities, including maintaining the ability to remove any encryption applied by the CSP”.

So if you access a website with https or use a VPN, then the encryption is not applied by the CSP, and there is nothing in the draft Bill to say you shouldn’t do so and no requirement for the CSP to attempt to crack the encryption with a man-in-the-middle or any other kind of attack.
Once again the imprecise definition of a CSP does introduce some uncertainty. CSPs (and I presume not necessarily just ISPs) are only required to “maintain” the ability to retain records. Lawyers might differ but to my mind this doesn’t include developing any new capability. But it’s unclear whether a developer would be obliged to build in such a capability in creating a new service or a new app. If so, this would make the UK an unattractive place for anyone to offer secure communications services.
When it comes to encryption it would seem that those with technical input to the draft Bill were a little less clueless about the subject than some of our politicians appear to be. If they really thought they had some smart guys in GCHQ who could effectively uninvent encryption if they tried hard enough, I would have suggested they first of all apply their minds to uninventing nuclear weapons.
But the smart way to defeat encryption is not to crack it but to bypass it, and this seems to be an objective of Part 5 of the draft Bill.
“Equipment Interference” is one of the spookier sections, covering a range of covert operations such as hacking into a subject’s computer, allowing access to messages and data before encryption or after decryption. It would be naive to think that this has not been going on all along, but it’s reassuring that it now becomes subject to proper regulation and judicial oversight.
 Earlier this year it was alleged that GCHQ was implicated in a massive theft of SIM card authentication keys from Dutch firm Gemalto. If true, this is simply not the sort of thing you expect from the nation that invented cricket!
Earlier this year it was alleged that GCHQ was implicated in a massive theft of SIM card authentication keys from Dutch firm Gemalto. If true, this is simply not the sort of thing you expect from the nation that invented cricket!
The legal basis would probably have been the Intelligence Services Act 1994. This provides for a warrant to be issued by the Secretary of State authorising the Security Services to perform actions that would otherwise be illegal. As such it’s incredibly broad. There is at least some hope that a warrant under the draft Bill for an action similar to the Gemalto breach would come under the critical eye of a cricket-loving judge!
Parts 6 and 7 of the draft Bill cover bulk warrants for interception, data acquisition, equipment interference and personal data. These too are spooky but they are undoubtedly nothing new. Whatever your view of them, it’s got to be an improvement if they are brought out of the shadows, properly codified and made subject to judicial review.
In conclusion, it seems to me that in some form at least, this draft Bill needs to become law. The area is currently governed by a jumble of legislation, no longer fit for purpose in the connected world we live in. Let the politicians and activists fight it out over Data Retention – we need the rest.
In a sense, perhaps it does mean after all that there is no safe place for criminals and terrorists. This is not because we will be able to read all their secret communications but because, as has always has been the case, they have to ensure that their operational security (OpSec) is perfect.
Intelligence gathering is not meant to be easy. It’s only easy in the sort of state where your every friend and colleague might be an informer, and then it’s always corrupt and unreliable. In a democracy, the spooks have to work hard for their intelligence. They can’t expect it on a plate delivered by a skeleton key.
The UK government has always claimed that the oversight of its security services is second to none in the world. I believe this draft Bill is an opportunity to ensure that really is the case and remains so.
Do you agree with Philip Le Riche’s assessment of the draft bill? Leave a comment below sharing your opinion.



Something that is not clear to me is whether ICRs include full urls all the time but (in the first instance) only the url up to the first / would be extracted and provided when properly requested or whether ICRs *only* contain the url up to the first /.
If, on the basis of what's been discovered from the domain name, a full record of urls is requested, does the CSR simply hand over the full urls that had already been collected (on everyone) or do they at that point start to collect the full urls?
You seem to have omitted the most alarming provision:
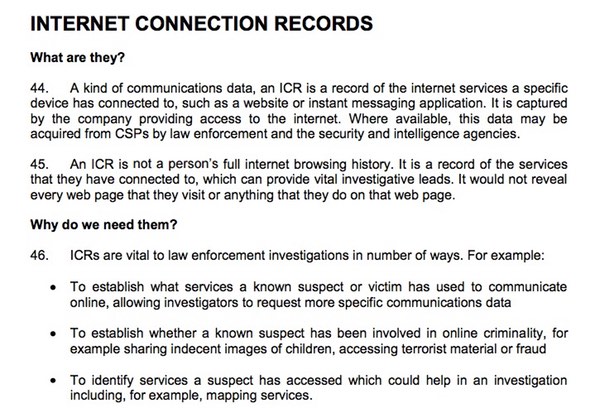
The draft Investigatory Powers Bill forbids anyone involved in interception from ever disclosing that fact, including during court proceedings (section 42). As Danezis writes: "Note that this section is absolute: it does not have exceptions, for example in relation to the public interest: such as the ability to discuss the benefit or downsides of part interception activities; no exception for talking about this to MPs, or other democratic representatives; or even to exculpate anyone who otherwise would be wrongfully found guilty."
http://arstechnica.co.uk/tech-policy/2015/11/snoopers-charter-uk-govt-can-demand-backdoors-give-prison-sentences-for-disclosing-them/
I'm only just starting to get to grips with all the pages of the draft, but a couple of points immediately occur.
You've mentioned the reassurance of judicial oversight. However, some legal commenters appear to be saying that the oversight is only of the process – i.e. were the correct boxes ticked when applying for the surveillance – not of the actual request for surveillance itself. If true, this would make for weak oversight.
Also, the Home Secretary can shortcut the process in an emergency. We can expect that in criminal cases, and particularly in terrorism ones, every instance will be an emergency. Just as RIPA was stretched far beyond its original intent, there is every possibility this bill will also lead to the temptation to over-use, and oversight rules need to bear that in mind.
What!?!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
"Equipment Interference" is one of the spookier sections, covering a range of covert operations such as hacking into a subject's computer, allowing access to messages and data before encryption or after decryption.It would be naive to think that this has not been going on all along, but it's reassuring that it now becomes subject to proper regulation and judicial oversight.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
So, that means its excusable because there is oversight by paid lackeys to turn a blind eye. Jeez! No wonder the black hats are as paranoid as they seem to be. We are all being steered towards the "if you aren't doing anything wrong (in your privacy with no victims), then you've got nothing to fear…" paradigm.
Here are three counters towards the 'nothing to hide' argument:
https://www.privateinternetaccess.com/blog/2015/07/i-have-nothing-to-hide-really-means-you-cant-confide-anything-in-me/
https://www.amnesty.org/en/latest/campaigns/2015/04/7-reasons-why-ive-got-nothing-to-hide-is-the-wrong-response-to-mass-surveillance/
http://mic.com/articles/119602/in-one-quote-edward-snowden-summed-up-why-our-privacy-is-worth-fighting-for
Part of that "interference" is the use of "Stingray" devices,although unstated,mobile interception is one of all law enforcements favorite tools! And the biggest concerns are the usual RE- interpretations the government spies make with sufficiently vague laws. Section 215 of the Patriot Act as Prime example!
This is just another example of how the state uses the threat of the boogeyman to justify ever more limitations on personal liberty. Anyone who approves of giving the kind of intrusive power to the state that the Investigatory Powers Bill would grant is laboring under the delusion that the state automatically are The Good Guys.
No, they’re not. The “good intentions” of the bill count for nothing, because those who have framed it will fade away and their intent will fade with them. Everyone else will be left with the consequences, forever. Another attack on freedom and the privacy of the individual will have succeeded.
Power engenders its own abuse. In the familiar paraphrase of Lord Acton’s insight, “Power corrupts, and absolute power corrupts absolutely.” The presumption that such power will be used wisely is not merely naive, it is outright fantasy.
'Specifically, anything following the slash after the domain name, as well as all content, cookies and browser or webpage metadata are excluded, and will of course be invisible in the case of an https connection.'
Logs do show the absolute path, however.
'…call the more intrusive forms of lawful intercept could never be made 100% secure'
How convenient that this is already the case (and it will always be this way; there is no 100% security), and so they could just as well stop there. But of course they won't and they'll just abuse the effective tactic of scaremongering – about fear itself. Typical blatant abuse of governments – but yet it works because it abuses emotion (hence 'terror', 'fear', etc.) and too many are too emotional (and emotion and logic don't mix well!) and also blindly accept the lies (I'll refrain from specifying what this equates to) and misinformation – especially if it fits their concerns/agenda.
Thank you all for your comments, both here and on Twitter. (I will not be responding further on Twitter except to direct people here as it's fairly ephemeral, the 140 character limit makes proper discussion difficult, and many of my followers and yours will consider it noise.)
Alan Henness and Coyote: Yes, the draft Bill is quite clear that only "communications data" can be collected under the Data Retention provisions. Of course, a raw Apache log would contain everything after the first single slash, but that must be removed. "Related communications data" may be collected in order, for example, to relate an IP address to a subscriber, but excludes anything which may be used to infer the meaning of the communication. That requires a specific Interception Warrant.
Coyote: I agree that too much policy is based on emotion rather than facts. I touched on that in a previous guest blog posing on this site in Oct 2013.
Bob: This is completely in line with UK legal practice. If MI5 were to tap your phone and hear you planning a serious criminal act, that would not be admissible evidence. A conviction would quite rightly have to rest on overtly collected evidence, testable in court. In addition, the Security Services are very reluctant to allow anything to be publicly disclosed which reveals their capabilities and methods.
David Hills: It would indeed be weak oversight if the Judicial Commissioners were only checking tick boxes. My understanding is that that's the responsibility of the Single Points of Contact, which do a preliminary quality and sanity check. But the effectiveness of Judicial Oversight will depend critically on the competence of the senior judges who are appointed in this specialised and sometimes highly technical area.
Yes, there is an urgency procedure, but it can be overruled by a Judicial Commissioner, in which case the activity which had been authorised must cease immediately.
(More to come.)
graphicequaliser: If you'll forgive me, you have a jaundiced view of senior judges if you regard them as paid lackeys of the government and security services. Equipment interference is distasteful but sometimes necessary. The security services already have the authority and capability to bug people's homes and tap their phones when necessary and it would be naive to think they haven't been using the same authority to hack people's computers. That authority (probably under the Intelligence Services Act 1994) is incredibly broad and the draft Bill brings it out of the shadows and adds judicial oversight. To my mind, that's got to be an improvement.
Publio Vestrone: All I can say is that when you discover Utopia I recommend you emigrate as soon as you can! It's a question of whether you regard the state as basically good though inevitably subject to human fallibility, or basically evil but trying to wear a human face. I believe the UK is much nearer the first than the second, and has checks and balances, not always perfect, which try to maintain that.
@richietynan (on Twitter): I think you need to spend a few hours studying the draft Bill for yourself. I certainly wouldn't agree that it's an onslaught on encryption, and I believe end-to-end encryption is safe. It states that CSPs must maintain the ability to remove encryption *they* apply. End-to-end encryption is applied by the endpoints, not the CSP.
I thought I saw something that indicated that a CSP is the entity that gives you primary access to the Internet but I can't find it now. Whether it includes messaging services is critical, and to my mind the one thing that most needs clarifying. True, firms like Apple have a UK presence which could be compelled to comply under UK law, but if you're worried, you could always use something like Threema, which provides end-to-end encryption and is based in Switzerland.
Philip, thanks for taking the time to reply to all of us – you obviously care about this subject, which is a good thing. However, I am absolutely flabbergasted to read, "The security services already have the authority and capability to bug people's homes and tap their phones when necessary" in a free, democratic society. I could secretly have horrendous bugs and leaky taps in my house! And, no, I am not talking about the need for insecticide or a plumber! ;-)
Welcome to the real world! But the use of these powers is very manpower intensive and so can only be used where essential. It's also why MI5 can't hope to track all the leads they get. Imagine sitting in a basement listening to hours of idle chatter from an intercept in search of a nugget of actionable intelligence.
Of course, a warrant is required for anything of this sort, issued at a high level.
From a discussion last night with a barrister friend it appears that my understanding of "maintain" may not be correct. He said that legally it could well be interpreted to mean "establish and maintain", but he thought that if that was the intended meaning, that wording should definitely be used.
Previously I hadn't seen any provision for CSPs' costs to be reimbursed. This is given in Section 185, though the level of payment (which cannot be nil) is determined by the Secretary of State. There is no mention of an appeal procedure in this Section.
And here's a little gem: Section 187 amends the Intelligence Services Act 1994. It allows for GCHQ to provide advice and assistance about "cryptography and other matters relating to the protection of information and other material" to (amongst others) members of the public! CESG (the Information Assurance arm of GCHQ) has traditionally provided policy and guidance to government departments and accredited security advisors only, but we can now expect to see some of this disseminated more widely.
I tend to agree with Richard Hills' somewhat more pessimistic assessment about judicial oversight – especially having heard Sir Mark Waller (Intelligence Services Commissioner) yesterday on BBC Radio 4's Law In Action. Sir Mark's position on judicial oversight was that judges would *not* need to be technically expert, since their role would simply be to check that legal requirements had been met (notably those for necessity and proportionality).
Sir Mark was quite "bullish" about judges' capability to discharge this role – wrongly, in my view. I think an assessment of proportionality can indeed depend critically on an understanding of how the technology works. For instance, in the US context, the NSA's former practice of including everyone within "three hops" of a suspect when analysing communications data. It's tempting to assume that you can estimate how many people are within three hops simply by extrapolating from the "first hop" of average user's social graph. However, if you understand that, technically, within the first couple of hops you are likely to encounter a mail service provider or a social network provider, your assessment of the number of people included, and therefore the proportionality of surveillance based on that number, will be radically different.
Under those circumstances I think Sir Mark's optimism is worryingly complacent.
I have a practical question about the notion of retention. Nobody who wishes to remain in business for more than a week operate their computers without backup. You expect me to believe that on the appropriate date, some Clark is going down to the vault, pull the drives out of cold storage, and skim through them to find the appropriate data to remove it from the back up files. Really. Oh look, unicorns.
The draft Bill requires that the CSP uses procedural and technical means to limit access to stored ICRs to the minimum number of people and the minimum level of access. The only way to do that sensibly is to collect the data on a dedicated server behind a firewall. The firewall would allows ICRs (domain name or IP address only) to pushed to the server as collected, and maybe allow ICRs to be extracted by the security services using a VPN tunnelled through the firewall and enabled against a warrant. A RAID array would be used for storage so no other backup would be needed. Not a single unicorn in sight.
Well, there are unicorns if the firewall can be hacked. And there are plenty that can. Firewalls are layer 7 on the network stack, and I prefer Windows IPSEC which operates at layer 2 or 3, and is almost impossible to tamper with. What you suggest can be done, but, if the government are handling it, it will be done very poorly (just look at their track record). The government would probably get a cheap Huawei hardware firewall, with its inbuilt back-doors (http://www.eweek.com/security/huawei-is-a-security-threat-and-theres-proof-says-hayden)!
I find it supremely depressing that the discussion seems to focus in on whether any of this is useful, or how it will work.
These are irrelevant, given the fact that it is morally wrong, and it doesn't matter how useful or easy it might be.
I am disappointed in the government, the security services, the police, and my fellow citizens, who seem, in the majority, to not find this kind of unwarranted surveillance to be morally unacceptable.
In a world without crime I'd have to agree with you, but unfortunately that's not the world we live in. You could say let's have complete and unrestricted freedom and privacy, and let the terrorists do their worst until they get bored. That argument could have some merit since ultimately, the only way to defeat terrorism is to refuse to be terrorised. But I think you'd find it a hard sell politically. So in order to get some sort of handle on crime of all sorts, we need to determine the degree to which law enforcement can be allowed to intrude into our daily lives in order to achieve a residual level of criminality that we can live with.
Philip, I think you've misunderstood my comments or the ArsTechnica article.
Section 42 means that if you were in court for an offence (any offence) and there existed secret surveillance which, if produced would result in you being acquitted, they would NOT be allowed to adduce it in evidence. Therefore even if you're innocent, and secret surveillance proves that, it'll be a criminal offence for a person involved with the surveillance to produce that. In short – you can be spied upon BUT if the information gleaned during the operation exculpates you – tough; not even a court sitting in camera can hear it.
If what you meant was: the security service aren't allowed to use secret evidence in court then, again, you're wrong I'm afraid. For a past few years there have been 'secret courts' where the defendant doesn't get to see any of the evidence against him. His defence, specially handpicked barristers (normally referred to as 'cleared' counsel – they undergo 'developed vetting') can't even ask him questions that may reveal any secret information elicited about him. The court (in secret) and in the absence of the defendant can convict him on the basis of surveillance or other evidence.
It's very unfair, but that's the law.
Bob, this is very British understatement. What you describe is not simply unfair. It is a complete negation of the rule of law ( and, for that matter the rules of Natural Justice). The Court of Star Chamber and end even the medieval courts of the Plantagenet kings would not have dared to behave in such a manner.
The Senior Judges (presumably meaning the Queen's Bench Division, the Chancery Division and the various appellate courts) no longer have anything remotely like the caliber of men that they enjoyed in the 19th and early to mid 20th centuries and have become little more than a pale parody of their former selves. Being a judge today is no longer a vocation, it is a profession and like all professionals judges must please both their masters and the press, especially if they want to be promoted. In the UK today the doctrine of the separation of powers is, if it is alive at all, in its dying days.
'and will of course be invisible in the case of an https connection'
Not if they look at server logs it won't. And who's to say they won't force a company or organisation to fork them over?