Britain’s National Crime Agency (NCA) has issued an “urgent alert” to computer users about the threat posed by the CryptoLocker malware.

The NCA’s National Cyber Crime Unit has warned that online criminals have launched a major internet attack designed to hold victims’ computer data hostage, and demand a ransom of hundreds of pounds be paid.
The cybercops’ alert warns that the CryptoLocker ransomware – which encrypts computer files and demands a ransom be paid for the decryption key – has been distributed via spammed-out emails claiming to come from banks and financial institutions.
Last week, US-CERT issued a similar warning to American computer users.
What types of computers does CryptoLocker target?
CryptoLocker targets computers running versions of Windows. Mac computers are not affected.
How is CryptoLocker spread?
CryptoLocker isn’t a virus or a worm, it’s a Trojan horse. That means – like most malware seen today – it can’t travel under its own steam, and doesn’t self-replicate.
Instead, CryptoLocker is typically distributed via spammed-out email messages, perhaps claiming to come from your bank or a delivery company. If you click on the attached file (which might pretend at first glance to be a PDF file, but actually use the .PDF.EXE double extension trick to hide its executable nature), your computer becomes infected.
Of course, it’s possible the criminals behind CryptoLocker could also distribute it in other ways. For instance, by compromising websites with malicious exploit kits that take advantage of software vulnerabilities to install CryptoLocker on visiting computers.
What files does CryptoLocker encrypt?
Once your computer is infected, CryptoLocker hunts for files to encrypt. It doesn’t just on your hard drive, but on any connected drives, including mapped network shares, and even folders that you might sync up with the Cloud – such as DropBox.
Filenames which match the following patterns are encrypted by CryptoLocker:
????????.jpe, ????????.jpg, *.3fr, *.accdb, *.ai, *.arw, *.bay, *.cdr, *.cer, *.cr2, *.crt, *.crw, *.dbf, *.dcr, *.der, *.dng, *.doc, *.docm, *.docx, *.dwg, *.dxf, *.dxg, *.eps, *.erf, *.indd, *.kdc, *.mdb, *.mdf, *.mef, *.mrw, *.nef, *.nrw, *.odb, *.odc, *.odm, *.odp, *.ods, *.odt, *.orf, *.p7b, *.p7c, *.p12, *.pdd, *.pef, *.pem, *.pfx, *.ppt, *.pptm, *.pptx, *.psd, *.pst, *.ptx, *.r3d, *.raf, *.raw, *.rtf, *.rw2, *.rwl, *.sr2, *.srf, *.srw, *.wb2, *.wpd, *.wps, *.x3f, *.xlk, *.xls, *.xlsb, *.xlsm, *.xlsx, img_*.jpg
So, you may well be saying goodbye to your documents, your databases, your photographs, your PowerPoint slides, your spreadsheets, and much else besides.
Will I see anything on my screen to tell me I’ve been hit?
Only when it’s too late.
After files have been encrypted, CryptoLocker displays a message that demands you electronically send the ransom payment (options may include Bitcoin, MoneyPak cashU, or UKash) in order to decrypt the files.
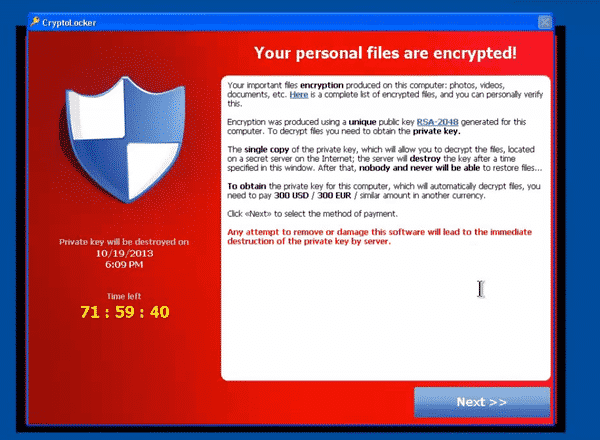
Your personal files are encrypted!
Your important files encryption produced on this computer: photos, videos, documents, etc. Here is a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files…
To obtain the private key for this computer, which will automatically decrypt files, you need to pay 300 USD / 300 EUR / similar amount in another currency.
Click <<Next>> to select the method of payment and the currency.
Any attempt to remove or damage this software will lead to the immediate destruction of the private key by server.
 A 72 hour timer is displayed, which ticks down and explains that if you do not pay the ransom demand, your files will be permanently inaccessible and impossible to ever decrypt.
A 72 hour timer is displayed, which ticks down and explains that if you do not pay the ransom demand, your files will be permanently inaccessible and impossible to ever decrypt.
The clock is ticking…
MoneyPak? Bitcoins? Can’t I pay the CryptoLocker ransom with a credit card instead?
No, the criminals don’t give a credit card option.
One of the reasons is presumably because it would be easy for victims to “pay” the ransom using their credit card to have their files decrypted, and then use chargeback to claw back their money.
Of course, many people may not know how to send funds via Moneypak or Bitcoin – a possible stumbling block for the criminals.
So if I don’t pay the ransom in time, all of my data is lost?
Not quite. The first hope has to be that you have kept regular backups of your important data, separate from your computer, and that you can restore your system from them. If you weren’t keeping backups, then please learn something from this horrible experience.
Secondly, and I don’t recommend you take this this option, it has been reported that the criminals are now giving victims the ability to pay the ransom *after* the deadline has passed, and get their files decrypted that way.
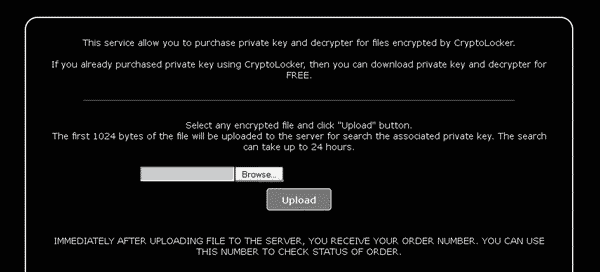
This service allow you to purchase private key and decryptor for files encrypted by CryptoLocker.
If you already purchased private key using CryptoLocker, then you can download private key and decryptor for FREE.
Regardless of whether you approve of encouraging blackmailers by paying the ransom or not, the fact that this late decryption service is only accessible via TOR, and not the conventional web, probably puts it beyond the reach of typical computer users.
Can’t anti-virus software remove CryptoLocker and save my data?
Good anti-virus software should be able to detect and remove CryptoLocker – however, removing CryptoLocker isn’t the same as decrypting your data files. And anti-virus software cannot unscramble your data.
If you do remove a CryptoLocker infection you won’t be able to pay the ransom to have your files decrypted.
Fascinatingly, the criminals behind CryptoLocker anticipated this, and change the Windows wallpaper on infected computers to explain how users can download and reinstall CryptoLocker!
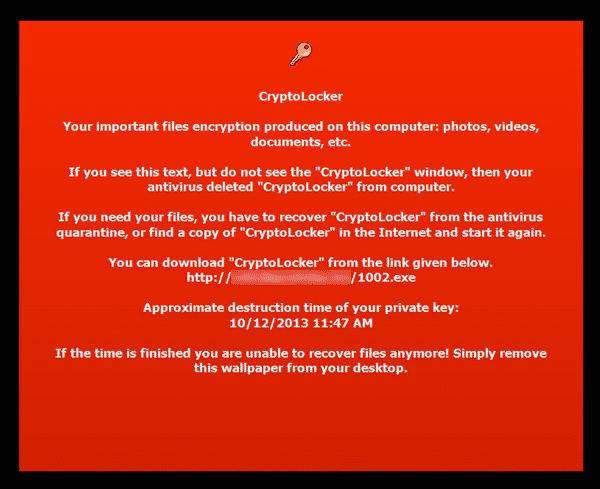
CryptoLocker
Your important files encryption produced on this computer: photos, videos, documents, etc.
If you see this text, but do not see the “CryptoLocker” window, then your antivirus deleted “CryptoLocker” from computer.
If you need your files, you have to recover “CryptoLocker” from the antivirus quarantine, or fine a copy of “CryptoLocker” in the internet and start it again.
How do you protect against CryptoLocker?
Cryptolocker is a serious threat. If you’re unlucky enough to have your computer infected by it, and haven’t taken precautions, you may find yourself in the unpleasant situation of having to choose whether to pay the ransom, or never gain access to your data again.
That means you’re saying goodbye to your family photographs, and any other personal data you have amassed over the years. If you’re a business then the potential losses could be even more significant.
The answer is three-fold.
Firstly, protect your computer from becoming infected by keeping it up-to-date with anti-virus and security patches. Also be cautious of opening unsolicited email attachments or clicking on unknown links. If you are security savvy you can reduce the chances of being hit by a threat like CryptoLocker.
Secondly, consider setting a software restriction policy on your Windows PCs that prevents executables from running from certain locations on your hard drive.
Finally, for goodness sake, make backups of your important data and keep them separate from your computer (to prevent malware like CryptoLocker from encrypting your backups as well) That way, if the worst does happen, you should be able to restore your valuable data and not pay up to the crooks.
Further reading
To learn much more about CryptoLocker, and how you should respond to it, I recommend you check out the FAQ from BleepingComputer.
Have you encountered CryptoLocker? Share your thoughts and experiences by leaving a comment below.



check out CryptoPrevent
http://www.foolishit.com/vb6-projects/cryptoprevent/
Surf Right's companion to their HitmanPro, a free application named HitmanPro.Alert is now in stable beta with an added component they call 'CryptoGuard' designed to inoculate against encryption ransomware — http://www.surfright.nl/nl/alert/cryptoguard .
Given that somebody had a partial backup, wouldn't be possible to make a known plaintext attack on particular files and derive the RSA key? It may require time probably but is it possible?
It seems that this particular malware fiendishly generates a unique AES256 key for every file, encrypts the file using this new key and then encrypts the unique key with the master key and stores it. You'd need a LOT of time.
Got hit by this Ransomware this morning on my works PC after opening an email in Hotmail that supposedly came from my local council. Subject was BACS Remittance and the attached file was DFA_15113_1_email.zip
My Company IT group have taken away but it appears a network drive has corrupted that I clicked on before the window appeared.
Dreading the consequences if this has got on my Home PC & NAS. 30 Years of memories.
would be helpful to have said that Linux PCs are not
affected…
Sorry, for not being clear.
Right now, CryptoLocker is only affecting Windows computers.
Computers running flavours of Unix, Mac OS X, iPhones, iPads, Android, BlackBerrys, Nokias, Windows Phone, and internet-enabled fridges (imagine your groceries being encrypted and taken hostage) are not impacted.
Of course, if the bad guys make a good deal of money out of CryptoLocker we might see future incarnations (or malware written by other criminals) impacting other platforms… although I suspect your fridge is probably safe.
so how long would my macbook be safe for
Current versions of CryptoLocker don't infect Macs, just Windows.
Of course, there is other malware which *does* infect Macs – so make sure you are running a good anti-virus.
Stop using Win the only reasonable solution. MS should suffer a lot. If win were properly secured from inside out that wouldn't be possible ai ? But 3dt party security solution only kills hardware performance but offering false security.
MACs are being targeted just as much as PCs (if not more now).
http://kmesystems.com/a-new-form-of-ransomware-targets-mac-computers-as-well-as-pcs/
I own and run a one man computer business in central MN. I
am not an expert but wanted to add some experience that
I've had recently with what I think is CryptoLocker or a
clone of it. In both cases (1 Vista and 1 XP I think) I was able to
remove the infection by booting with the HitmanPro trial from a USB
flash drive. Both systems had the same graphics and desktop
wallpaper image, both had the countdown timer. One was down to ~68
hours and the other was ~48 hours. I didn't know about
this Malware and just attacked it as normal with Hitman booted from
a flash drive, ComboFix and Malwarebytes after booting clean.
Anyone else been able to disable/remove this? Hu
Its my understanding that you can remove it, but that they
will still keep the files hostage. Were you able to retrieve the
files after removing it with hitman?
All those people running W7 Home Premium are left without a means to set up policies to prevent CryptoLocker? Unless they run a 3rd-prty application which of course they should trust because…(it's not CryptoLocker … is it?)
how can local policies be set up in W7 Home Premium without a policy editor … are the registry settings for the above policies available? would the registry have to modified on a per-user basis?
Hello!
Maybe there's a simple solution, we have not tested ourselves but it could work.
WINDOWS 7, right click on the folder that is encrypted and select properties> then go to the tab previous versions in properties you will see an earlier version of the folder that your computer has been saved. Then you can simply choose one from the day before you got the virus, and then click the Copy button, make a new folder and copy your work in the new folder – you will get back almost all your files unencrypted, maybe not the last job you have done, but most will be there.
Myzone Team Sweden
I don't see any previous version of my files because I don't use windows back up . My all file extension changed to GTUKOEA. I have removed the CBT virus .But I am unable to recover my data . I tried with many document recover and repair software.But no use. Help me plz
If you have already encrypted your files with bit locker, is crypto locker still able to encrypt your files?
Yes. BitLocker encrypts your HDD so if someone stole your
laptop and didnt know your computer password…your data is safe.
However cryptolocker encrypts files after the OS is booted thus has
access to the your files. In a nut shell, the files get encrypted
twice. Once by you and once by the virus.
What about System restore, back to before the infection ?
after you have removed the offending trojan of course :) cheers ~
JD
That's it! I am now switching all my PCs to Linux
(Mint 13 LTS). Bye-bye Windoze.
Damn Microsoft not securing Windows from inside out isolated app spaces sandboxes user secure user space and so on all that is missing in win. Tech available but MS simply does not want to do it so their 3dt party partners making huge money on insecure win fixing holes in win that ms left open and so on but user have even more problems. MS should suffer a lot.
For home computer one do not need win use Linux or similar for internet ! If you have powerful hardware then use SmartOS and Win as guest for playing games for internet i recommend some Linux Distro at choice. Why SmartOS ? Its a hypervisor OS and one have backup the whole OS at fingertips of the mouse click ! Something that MS misses to implement ! I too will replace Win with other OS but for specialized work there is no replacement for it. So the best what you can do is cut of network/internet from such computer and pas data/files to it manualy trough USB HDD or flash.
MS should suffer a lot. Did you know that NSA is heavily involved in win development and even financially support MS as long they obey NSA directive. And now use Win for serious work.
How about disabling the EFS service, or Bitlocker service,
or both as a prevention?
Does anyone have an answer for this?+
Hi how can I remove the cryptolocker?
Hmmm…. maybe I'm a cynic, but try this on for
size? Cryptolocker is coded by GCHQ/NSA whoever and floated out
onto the web…. mass media do their best to stoke up fear and
pandemonium within the World internet
"unintelligensia"…. the authorities pinpoint
the source of the problem as "the dark web" or
whatever other ominous name said press has coined for those who
refuse to be spied on by their "democratic
governments"…. the uneducated masses urged on by the
mind control machine"…. sorry mass media then clamour
for a timely crackdown on the unfettered criminality of those
"freedom fighters" and introduce more draconian
legislation to protect the wealth of the "super
elites". As David Eike puts it… Problem – reaction –
solution. Pass me my tin foil hat…they're out to get
me….
Ooh "Cthulu," the lizard men from outer
space have encrypted my data! I'd better call David Icke,
son of God, psychic, and noted computer security expert, to recover
my files. ;)
Thanks for these great ideas. I have looking for ways to get rid of this cryptolocker. I will your solutions and see if it works. Thanks
was on website with apple ipod and screen locked with the fbi, interpol and other investigative angencies reviewing– had a little trouble getting out of lock but was easy enough after double clicking. can this malware virus do this on an apple ipod, ipad?
I recently just got Cryptolocker on my laptop earlier today. Fortunately I haven't had the laptop for very long and only had two unimportant files. I'm getting my OS reset to get rid of it. After reading stuff about it, I figured out how I got it. I went to ipay.adp.com and logged in to view my payment statements and something popped up indicating that I needed to click this pdf link in order to view my statements, which I found odd because normally it would instantly show what I wanted to see. Since I'm still a bit new to the site and hadn't gone on it in a while, I thought maybe it was either something new or it always did that, and I just didn't remember. I didn't think too much about it because I didn't think clicking something on such a common website, would be bad. I needed to view my statements so I clicked the link. It loaded but nothing came up. I gave up after a while, closed that laptop and used my other laptop, which instantly showed what I wanted to see right when I logged in. When I opened my laptop up again about an hour later, there it was. The Cryptolocker. Makes me wonder if that ADP website has been hacked, and if so, what else can and will be hacked? Cyprtolocker is an awful malware. I feel bad for anyone who has encountered it. I am lucky that I only encountered it on a new laptop which didn't have much to lose. It still sucks though that I'm paying $50 to have my OS reset all because I clicked a link on a website I thought could be trusted. I will never look at links to pdfs or emails the same.
Get a Mac.
I recently got what appears to be cryptolocker virus. It does everything that crypto locker does without the serious damage. It still has encrypted all of my photos. and MS office files. Is there a way to recover these encrypted files
Dear Sir,
Appreciate your work and website for providing such helpful informations, I am trying to find out some way as My device (Android Samsung Phone) have been infected with CashU Virus which has blocked it completely displaying the same page whatever and demanding to pay for around 300$ through CashU services. Would you please guide me how to get ride of it as I have many important documents and personal memories saved in my device without backup, your help will be highly appreciated.
Till now I could only find the guidelines from other websites only for Computers, not for android phone.
Waiting for your earliest reply via email.
Best Regards,
Taufiq