If, like me, you own a website then watch out for malicious emails like this.
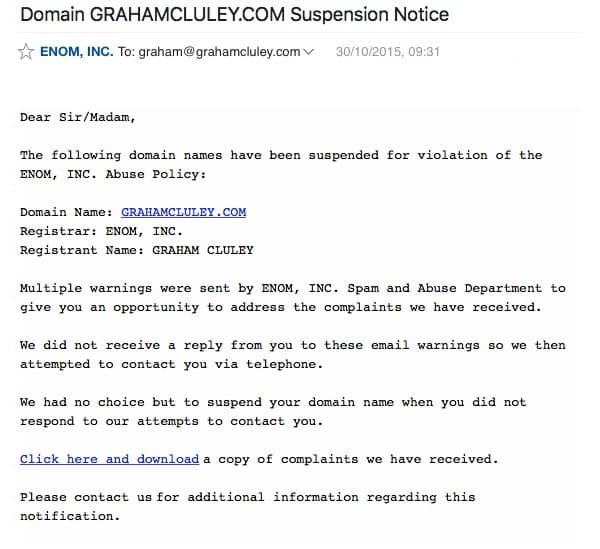
From: ENOM, INC <>
Subject: Domain EXAMPLE.COM Suspension NoticeMessage body:
Dear Sir/Madam,The following domain names have been suspended for violation of the ENOM, INC. Abuse Policy:
Domain Name: EXAMPLE.COM
Registrar: ENOM, INC.
Registrant Name: JOHN DOEMultiple warnings were sent by ENOM, INC. Spam and Abuse Department to give you an opportunity to address the complaints we have received.
We did not receive a reply from you to these email warnings so we then attempted to contact you via telephone.
We had no choice but to suspend your domain name when you did not respond to our attempts to contact you.
Click here and download a copy of complaints we have received.
Please contact us for additional information regarding this notification.
I can easily imagine a spammed-out malware campaign like this fooling some people.
Because the email mentions your real name, your website domain name and (most importantly) says that your domain has been suspended you might rush to click on the link.
 But you should always be careful before acting upon unsolicited emails.
But you should always be careful before acting upon unsolicited emails.
eNom, Inc. is a legitimate domain name registrar, and my site may be registered with them, but the link in the email doesn’t go to eNom’s website.
Instead it goes to a third party site – most probably hacked – hosting a file called example.com_copy_of_complaints.pdf.scr (the precise name will vary depending on your domain name).
Did you spot the .SCR at the end of the filename? That’s the extension that is normally used for executable Windows screensavers – so it doesn’t look like it’s a real Adobe PDF file. Not that I would trust it even if it were a PDF file to be honest, as there are so many Adobe vulnerabilities doing the rounds!
According to VirusTotal, a small number of anti-virus products are currently identifying the file as malicious.
If you were to open the file on your computer, your website would almost certainly not be suspended but you would have a whole host of other problems…

I've received one for one of the sites I have hosted at 1and1.co.uk but the link takes you to a web page and on my version it goes to "bigimesensuality.com/abuse_report.php?mydomain.com"
So, as usual there seem to be several variations out there already.
That sounds the same as the one I received. It linked to a domain with the url example.com/abuse_report.php?mydomain.com, which in turn tried to serve up the malicious file.
Whilst the advice above is all good some modern email servers, take Office 365 as an example, offer advanced protection against these threats. Firstly they check the IP against a blocked list, then check it for content and if it passes those tests they validate its DKIM/DMARC (if any) and SPF.
If they pass all of these tests they then 'detonate' the attachment in a one-use-only hypervisor to assess it for suspicious behaviour e.g. registry changes, escalation of privileges etc.
Microsoft call their solution 'Advanced Threat Protection' but there are others out there.
https://technet.microsoft.com/en-us/library/mt148491%28v=exchg.150%29.aspx
Other commercial email providers should follow suit by doing more to prevent suspicious .pdf.scr attachments; there are plenty of variations on that theme – .txt.exe etc.
In this case the malware wasn't attached to the email. The malware was transmitted to the computers of users who clicked on the link contained within the email.
Oh boy. Emails with extensions like .exe .com .scr and the like never make it past my mail server anyway. No exceptions permitted. You don't need any advanced threat protection measures to mitigate these kinds of low hanging fruit emails.
Yes, I think that's a good policy to consider for email attachments – but in this case the malware didn't arrive as an email attachment, but was served up to users who clicked on the link in the email.
VirusTotal is reporting that just three out of 54 products flag this as malware.
It seems to me that these days, a sensible antivirus system consists of a user who rejects incoming (by whatever means) com or exe files, scr files, and zip files that contain those. Doc, docx, pdf and xls files should only be opened by something that doesn't run macros.
That it seems to me, will fend off the constant influx of malware that we're all seeing.
You can add to this, one or more antivirus products, but these have about as much effect as a chocolate teapot.
It's worth bearing in mind that VirusTotal results are not a great way of telling whether a particular anti-virus product might not have been able to intercept a malware attack.
My understanding, for instance, is that VirusTotal doesn't test the versions of products which sit at the email or web gateway – which may run a version of the scanner with different settings, perhaps with more aggressive heuristics or rules such as those you suggest. In addition, VirusTotal isn't testing behavioural analysis, which might provide a higher level of protection than the simple command-line scanner they have in their systems.
So, the bit that VirusTotal is testing might be as useful as a chocolate teapot, but the software being used on a typical corporate network *might* actually confer a higher level of protection.
It's still a "might" though – and I would feel a whole lot happier if I knew for sure.
Pretty scary stuff.
Seems the scammers have cunningly crafted a way to do a lookup on domains, harvesting the registrar's contact details in an attempt to phish the owners.
Double-dot attachments also try to hide the innocence of an attachment if filters fail the end user.
Email headers are king if in doubt. I usually treat any personal email that's not in my contacts list as suspicious until I verify the sender or if am expecting such correspondence(s).
I have my domain registrar hide my contact details. Luckily I get this for free, unlike another I dealt with that would charge an annual fee.
It amazes me, that, even with the latest Windows 10, the extensions of files (known to the system) are hidden from the user. This default is only set this way to "aid" those users who are easily confused, to not worry about extensions and let the relevant app handle it all. We really are not that stupid, and the default setting should be to enable the filenames to be seen in their entirety, especially in the light of all the recent hacks and exploits attempted on the unsuspecting masses.
Agreed with the default file extension setting.
Niceties aside, it's a nuisance and should be visible by default.
Having said that, technophobic people wouldn't know the dangers of launching a *.vbs, *.js, etc… anyhow. Safety mechanism in-place are their only defence.
Agreed with the default file extension setting.
Niceties aside, it's a nuisance and should be visible by default.
Having said that, technophobic people wouldn't know the dangers of launching a *.vbs, *.js, etc… anyhow. Safety mechanisms in-place are their only defence.
I have received several of these in the last 2 days relating to domains recently transferred to Google Domains. What puzzles me is how they got my e-mail, because I elected to keep my details private when registering with Google. I will be calling Google later today.
They didn't get your e-mail. They probably used your domain privacy redirect (proxy) e-mail address on the whois record. Your DNS register service then forwarded the e-mail to you.
I got two of these attacks last night. They must have gotten my contact info out of the DNS records, which isn't hard. I wonder if they were also the people who have been calling. I have gotten a handful of blank messages on the answering machine, and silent calls, when I was here to answer them. This phone number is also in the DNS records. I smelled a rat when I saw where the link was pointed, and even though my browser isn't running under windows I satisfied my curiosity by doing a Google search instead of following the link. The phone number in my email points to a FAX machine in Arizona, according to Google, and the malware was hosted on menos.com and altervista.org. It seems odd that hackers would try to find Windows users in the DNS records. Don't most system administrators run OS X or linux? Has anyone else gotten phone calls? That seems like way more effort than most hackers would take, but maybe the calls were entirely robotic.
I've had multiple emails in for a couple of .com domains. Is my registrar / web host to blame for this? The emails had all gone into my spam folder and I spotted the dubious link. My web host company seemed very cagey when I accused them of being hacked…
I have never gotten anything like this ever until I just moved all my domains to a new hosting and now I'm getting swamped with these emails