 Here’s some genuine good news to brighten the day of anyone who has had their computer hit hard by one of the most pernicious threats to hit internet users for a long time.
Here’s some genuine good news to brighten the day of anyone who has had their computer hit hard by one of the most pernicious threats to hit internet users for a long time.
Boffins at Fox-IT and FireEye have teamed up to provide a free service – decryptolocker.com – to help anyone has fallen foul of the notorious CryptoLocker malware that encrypts computer files and demands a ransom be paid for the decryption key.
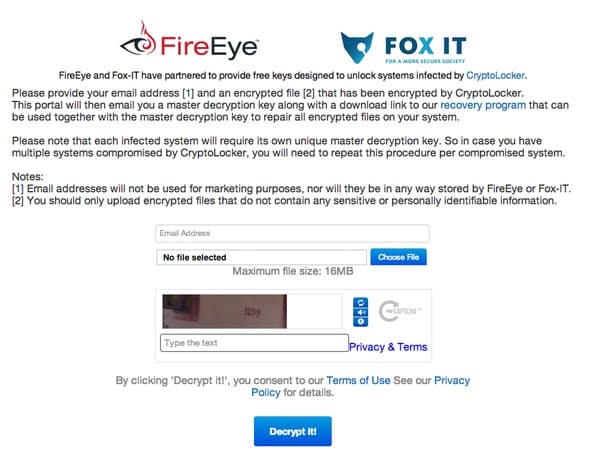
To use the DecryptoLocker service, CryptoLocker victims will need to:
- Identify a single, Cryptolocker-encrypted file that they believe does not contain sensitive information, and upload it to the DecryptoLocker portal. I’m sure the service would work on a file containing sensitive information, but it’s obviously bad practice to upload such a file to the service.
- Wait to receive a private key from the portal and a link to download and install a
decryption tool that can be run locally on their computer. - Run the decryption tool locally on their computer, using the provided private key, to
decrypt all of the encrypted files on their hard drive.
Sounds neat – and if the service wasn’t supplied by trusted, established security experts like Fox-IT and FireEye I would tell people to be suspicious. But this appears to be the real deal – and will be a god send to users who thought they had lost access to their data forever.
Ronald Prins of Fox-IT confirmed on Twitter that it was possible to create the DecryptoLocker service after researchers managed to access the criminals’ database of private keys.
So, it’s still the case that CryptoLocker’s encryption hasn’t been actually cracked, but that doesn’t matter for victims who don’t have access to a backup, or who balked at the idea of paying money to extortionists.
CryptoLocker was a big problem, hitting some 600,000 computer users around the globe, so it’s good to see both law enforcement and the security industry fighting back.
Lets hope that the authorities manage to get their hands on Evgeniy Mikhailovich Bogachev (also known as “Slavik”). 30-year-old Bogachev is the alleged mastermind of the gang that spread the GameOver Zeus (“GOZ”) malware and Cryptolocker ransomware, and was the subject of a recent FBI “Wanted Poster”.

Andy Chandler, senior vice president of Fox-IT, tells me that his company has been tracking Slavik for months, and in partnership with FireEye a clear picture of the criminal group has emerged. Maybe if the current political situation improves we can hope to see more action taken against him and the rest of the CryptoLocker/GameOver Zeus gang.
But for now, if you were a victim of CryptoLocker and chose not to pay up (good for you!), there’s a new way to get your data back: decryptolocker.com.



Any indication this will help those affected by synolocker?
"if the service wasn’t been supplied by trusted by established security experts"
Garbled, needs an edit.
I cant figure how to upload a file ,I lost many things Ill open one of the 4 that have an e like Explorer 3 others they are all on External Drives I just never uploaded and am extremely sick and medicated anyway it said "What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 3.0.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them,
it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 – public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
[redacted]
If for some reasons the addresses are not available, follow these steps:
1.Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2.After a successful installation, run the browser and wait for initialization.
3.Type in the address bar: paytoc4gtpn5czl2.onion/1UQt74
4.Follow the instructions on the site.
IMPORTANT INFORMATION:
Your personal page: [redacted]
Your personal page (using TOR): [redacted]
Your personal identification number (if you open the site (or TOR 's) directly): [redacted]
Tell me what you need Thank You Mark W
Hi,
I have been infected and all my pictures have exx extention now, but when I upload to your site it says files are not cryptolocker infected.
Any advice is appreciated,
regards,
George
I'm afraid I'm not connected to the site. You'll need to contact Fox IT or FireEye.
Does anyone have any info on a fix for files encrypted with Cryptowall 3.0 yet?
Not giving up my files. I have removed the infected drive and holding onto it until there is a solution.
I still have a synology drive from 2014 which has the encrypted files on it (all the photos of my children's births and their first few years).
However the decryptolocker.com. site is no longer available.
Is there anywhere i can still get the decryption key/solution from?
I really am VERY desperate to get my precious photographs back as my son has muscular dystrophy, which is a life limiting condition.
Any help /advice greatly appreciated.