Chances are that you have read some of the same scary headlines that I’ve seen in the last 24 hours or so.
The claims that the NSA has a backdoor into the iPhone, giving it the opportunity to spy upon virtually all activity on the device, came amid a much wider talk given yesterday by computer security researcher Jacob Appelbaum (aka @ioerror) at 30C3, the 30th Chaos Communication Congress held in Hamburg, Germany.
Although the alleged Apple iPhone backdoor has made most of the headlines, Appelbaum’s talk (a video of which is embedded below) describes a much broader range of tools that the NSA apparently deploys against other technology companies and products, including HP servers, Cisco firewalls, Huawei routers, and so on.
Appelbaum presented his research in parallel with Der Spiegel publishing its own detailed report into the issue.
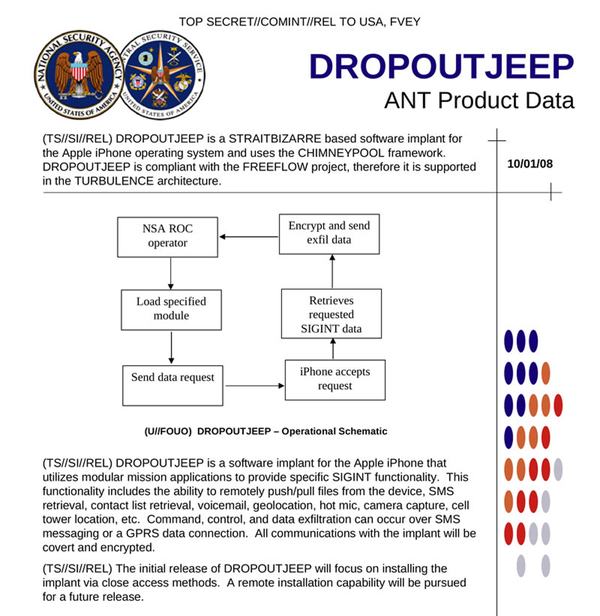
DROPOUTJEEP is a software implant for the Apple iPhone that utilises modular mission applications to provide specific SIGINT functionality. This functionality includes the ability to remotely push/pull files from the device, SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic, camera capture, cell tower location, etc. Command, control and data exfiltration can occur over SMS messaging or a GPRS data connection. All communications with the implant will be covert and encrypted.
But, despite some of the breathless headlines used by some sections of the media, the material presented does not mean that the NSA has “complete control of your iPhone”.
Just take a look at the bottom of the leaked document, which dates from 2008:
The initial release of DROPOUTJEEP will focus on installing the implant via close access methods. A remote installation capability will be pursued for a future release.
In other words, the NSA’s TAO (Tailored Access Operations) hacking unit requires physical access to your iPhone in order to plant spyware on it
Now, it may be that they have since found unpatched vulnerabilities in iOS to install the spyware onto targeted devices remotely (and – one presumes – not told Apple about those security holes), but that’s not what the leaked documents say.
Decide for yourself, and get an eye-opening view on how America’s spies appear to be hoarding zero day exploits in products from US companies, and using them against people worldwide, by watching the video of Appelbaum’s talk. (The short section detailing NSA technology to spy on iOS devices can be found at approximately 44min:30sec)
It sounds as though everything that America has accused the Chinese of attempting in the way of cyber espionage, the US government has also been doing against American users and companies.
The last words on the iPhone backdoor implanting go to Appelbaum, from his talk at 30C3:
I don’t really believe that Apple didn’t help them. I can’t really prove it yet, but they [the NSA] literally claim that anytime they target an iOS device, that it will succeed for implantation. Either they have a huge collection of exploits that work against Apple products, meaning that they are hoarding information about critical systems that American companies produce and sabotaging them, or Apple sabotaged it themselves.
Not sure which one it is. I’d like to believe that since Apple didn’t join the PRISM program until after Steve Jobs died, that maybe it’s just that they write sh**ty software. We know that’s true.
I must admit I tend to believe more in the cock-up theory of history, rather than conspiracy. If that’s the case, let’s hope that Apple has improved its software’s security since 2008.
And if it’s not true, we’ve all got a huge problem.


![Everything we know about NSA spying [VIDEO]](https://grahamcluley.com/wp-content/uploads/2014/01/nsa-thumb1.jpeg)
This article
(http://www.dailydot.com/politics/nsa-backdoor-iphone-access-camera-mic-appelbaum/)
suggests that having physical access to the device to install the
malware was "achieved by rerouting shipments of devices
purchased online".
Thanks. Applebaum covers that in his talk as well. Check out the video embedded above
This is why people should switch to the Android. Its 1000x times better than shitty Apple
Its not fair! Why do 480,000 NSA employees get access to massive power like this, being able to spy, steal login credentials, and track virtually any product or service for insider information, financial gain, etc.
And then there are typical blackhat hackers who want to have full backdoor access to a massive service like Facebook or Apple in order to make tons of money, either through exploitation or selling it to the NSA. But these days, a critical privacy exploit is rare. But just imagine if just one of those employees decides to become a blackhat. Then what?
The NSA is allowed to do illegal hacking? Double standard.
Video was chilling but very expected. I researched (in
1994) that the Feds (USA) required control of all encryption
algorithyms and required all internet controllers have special
devices for the gov to access. That was 2 decades ago… they
certainly haven't slowed down!!!
"In other words, the NSA’s TAO (Tailored Access
Operations) hacking unit requires physical access to your iPhone in
order to plant spyware on it." That is incorrect. As
Applebaum <a
href="https://mailman.stanford.edu/pipermail/liberationtech/2014-January/012498.html">has
written</a>: "There are quite a few news
articles and most of them have focused on the iPhone backdoor known
as DROPOUTJEEP – they largely miss the big picture asserting that
the NSA needs physical access. This is a misunderstanding. The way
that the NSA and GCHQ compromise devices with QUANTUMNATION does
not require physical access – that is merely one way to compromise
an iPhone. Generally the NSA and GCHQ compromise the phone through
the network using QUANTUM/QUANTUMNATION/QUANTUMTHEORY related
attack capabilities." [See the link for more.] And anyway,
beyond the interdiction of online shipments to physically implant
exploits, as Applebaum pointed out in one of the many frightening
parts of his presentation, "physical access" has
become an incredibly elastic thing. Apparatus like the NIGHTSTAND
hardware (which appears to have specifically targeted Windows
systems) — which had already been "deployed in the
field" in 2007 — could wirelessly access devices and
inject exploits from as much as 8 miles away, and Applebaum
speculated that such hardware might well be transported via drone
(or van) to bring the apparatus within the desired physical
range.
Not to be annoying, but I'm going to repost (with small changes) my previous comment given that it all got mashed into one unreadable paragraph:
Graham Cluley: "In other words, the NSA’s TAO (Tailored Access
Operations) hacking unit requires physical access to your iPhone in
order to plant spyware on it."
That is incorrect. As Applebaum has written:
"There are quite a few news articles and most of them have focused on the iPhone backdoor known
as DROPOUTJEEP – they largely miss the big picture asserting that the NSA needs physical access. This is a misunderstanding. The way that the NSA and GCHQ compromise devices with QUANTUMNATION does not require physical access – that is merely one way to compromise
an iPhone. Generally the NSA and GCHQ compromise the phone through the network using QUANTUM/QUANTUMNATION/QUANTUMTHEORY related attack capabilities."
[see https://mailman.stanford.edu/pipermail/liberationtech/2014-January/012498.html for more]
And anyway, beyond interdicting online shipments to physically implant exploits as Anon mentioned, "physical access" has become an incredibly elastic thing, as Applebaum showed in one of the many frightening parts of his presentation. Apparatus like the NSA's NIGHTSTAND hardware (which appears to have specifically targeted Windows systems) — which had already been "deployed in the
field" in 2007 — could wirelessly access devices and inject exploits from as much as 8 miles away, and Applebaum speculated that such hardware might well be transported via drone (or van) to bring the apparatus within the desired physical range.
In order to protect the security of our country, NSA has to spy on our network. However, as an individual, if you want to protect your family from danger, you should also spy on your family members\' PCs and cell phones using spy tools like Micro Keylogger or iKeyMonitor ( http://ikeymonitor.com ). It is so far the most convenient and easiest way to protect your family.
I do agree with what the article say, And I have heard that the iKeyMonitor can log many things ,such as messages ,the calls and so on. I am using the iPhone 5s, and I want to try this, this article give me a clear look.