 It sounds like a puzzle worthy of a Sherlock Holmes novel.
It sounds like a puzzle worthy of a Sherlock Holmes novel.
How *would* cybercriminals extract information from a malware-infected computer that they *don’t* have physical access to, and that *isn’t* connected to any networks, WiFi or the internet?
At first, you might think it’s impossible. But there is, claim German computer scientists at the Fraunhofer Institute for Communication, Information Processing, and Ergonomics (FKIE), a way.
Michael Hanspach and Michael Goetz say that malware could transmit sensitive data (such as confidential databases or logs of keypresses), covertly and secretly, by transmitting it via the infected computer’s speaker at near ultrasonic frequencies through the infected computer’s built-in speaker.
The idea, described in a paper entitled “On Covert Acoustical Mesh Networks in Air”, is that the data can be sent at high frequency over the air as computer operating systems do not tightly control a program’s access to the speaker.
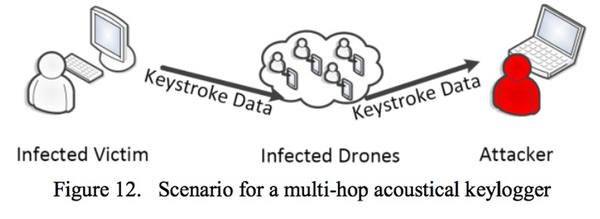
Indeed, Hanspach and Goetz go further and describe how an over the air broadcast of leaked data could have its range extended through the creation of a secret acoustical mesh network – effectively a botnet of drone computers receiving high frequency sounds and hopping them further along.
We further demonstrate how the scenario of covert acoustical communication over the air medium can be extended to multi-hop communications and even to wireless mesh networks. A covert acoustical mesh network can be conceived as a botnet or malnet that is accessible via nearfield audio communications. Different applications of covert acoustical mesh networks are presented, including the use for remote keylogging over multiple hops. It is shown that the concept of a covert acoustical mesh network renders many conventional security concepts useless, as acoustical communications are usually not considered.
So, let’s just back up for a second before people add two and two together and make five…
Firstly, and most importantly, this research does not mean malware can infect your computer via sound.
Playing the individual bytes of a piece of malware code at any frequency is not going to infect the computer hearing the sound through its microphone unless it has already been compromised in some way to act upon receiving executable code in that way.
And, if the target computer has already been compromised to act upon unusual data sent at high frequency, why go to all the effort of transmitting code to it over the air anyway?
Secondly, the bad guys still need a way of infecting the air-gapped target computer in the first place, in order to exfiltrate data from it. Remember, this is a computer which is not connected to any network, is not on WiFi, and probably has tight controls over who can physically access it.
 That doesn’t make infection impossible, of course.
That doesn’t make infection impossible, of course.
Imagine, for instance, malware planted on a USB stick known to be used by staff who use the computer, or meddling that could be done in the supply chain in regards to software destined for installation on the target computer, or if an employee of the targeted organisation turned rogue.
But it does make things much trickier.
Thirdly, it’s not just the target computer that needs to be compromised. As the FKIE research reveals, the physical range of the data transmission between one computer’s speaker and another’s microphone is quite small, necessitating that a series of computers may need to be comandeered to act as a transmission network.
If you’re still worried about this threat affecting your air-gapped computers, there are some steps you can consider.
- Keep your guard up! Tightly control who has access to the computer, and what software they are able to install on it. This attack cannot work at all unless your computer is compromised.
- Disconnect your PC speaker. Physically cut the wire if you want to. It’s brutal, but it works.
- Consider a solution that filters non-audible frequencies from being broadcast through your speaker. Of course, if your computer is already infected by malware that is attempting to transmit data at ultrasonic frequencies, it may also attempt to subvert or disable such a filter.
- Maybe one solution would be to garble the ultrasonic frequencies with white noise, corrupting any attempt to transmit data? This could be rather like the high-pitched Mosquito sonic deterrents said to repel teenage troublemakers from gathering in particular area. After all, if your staff can’t hear the ultrasonic transmissions, is there any drawback in broadcasting white noise at that frequency?
- Remember Alien? “In space, no-one can hear you scream”? And – indeed – you can’t transmit sound through a vacuum. However, the cost of that approach may be going a little too far, when cutting the wire to your speaker costs nothing.
Me? I’m not going to let this bother me and will sleep soundly in my bed tonight. Although I pity Mrs Cluley, who may have to put up with my subsonic snoring…
Hat-tip: “On Covert Acoustical Mesh Networks in Air” via Ars Technica.



We pity Mrs Cluley SHE though she was getting George Clooney!
Sub-sonic snoring shouldn't be a problem, shirley? Unless it's some sort of wet-ware biomatics that transmits your FaceBook password directly out of your subconscious?
I previously suggested white noise as a possible method of blocking badBIOS communications (if badBIOS malware actually exists)*:
https://twitter.com/theJoshMeister/status/397939757910458368
*This was hotly debated amongst much of the security community about a month ago. I've noticed that you've completely avoided speculating about it or even covering the kerfuffle on your site. I was surprised that there wasn't at least some mention of badBIOS or Dragos Ruiu in this article.
Thanks Josh
I did consider mentioning the mythical BadBios, but decided (as it has been such a to-and-fro and lack of real verifiable detail) that it would be a distraction from the meat of the work done by these researchers.
Anyway, the points I raised in the article are applicable to both. Malware cannot infect your computer via sound unless the target computer has already been seriously compromised (which kind of negates the point).
I see that this latest research is being poorly reported by some press, who are incorrectly claiming this is a way for malware to infect computers, rather than a way for a malware-infected computer to transmit data.
Also this method assumes that the receiving computers have some sort of microphone, which is turned on. Pretty easy to unplug or mute a mic and you can still use your speakers …
We don't need to disconnect our Speakers i think. Because the malware has to be executed first on victim pc then it will start its function.
Correct me if wrong. Thanks.